PAN-OS GlobalProtect Command Injection Vulnerability
Watch Video
PAN-OS GlobalProtect Command Injection Vulnerability Video
An actively exploited critical vulnerability in the PAN-OS Global Protect
The attack on PAN-OS GlobalProtect devices identified as CVE-2024-3400 allows a malicious actor to remotely exploit an unauthenticated command injection vulnerability that leads to remote code execution. Once established, the attacker can further collect configurations, deliver malware payloads and move laterally and internally. Learn More »
Common Vulnerabilities and Exposures
Background
The GlobalProtect Gateway provides security solution for roaming users by extending the same next-generation firewall-based policies.
Threat Radar Overall Score: -
| CVSS Rating | 10.0 | |
| FortiRecon Score | 100/100 | |
| Known Exploited | Yes | |
| Exploit Prediction Score | 95.36% | |
| FortiGuard Telemetry | Analyzing |
Latest Development
Recent news and incidents related to cybersecurity threats encompassing various events such as data breaches, cyber-attacks, security incidents, and vulnerabilities discovered.
The FortiGuard is continuously monitoring and investigating the attack to increase protection coverages and reduce the attack surface.
Apr 25, 2024: The FortiGuard Labs noted a significant increase in the detection of IPS signatures through FortiGuard telemetry, blocking attacks on over 10,000+ unique IPS devices targeting the PAN-OS vulnerability (CVE-2024-3400).
Apr 19, 2024: Palo Alto released more information on CVE-2024-3400 and how it was attacked. https://www.paloaltonetworks.com/blog/2024/04/more-on-the-pan-os-cve/
Apr 15, 2024: FortiGuard released an IPS signature to detect and block exploitation attempts targeting edge devices. https://www.fortiguard.com/encyclopedia/ips/55555
Apr 12, 2024: FortiGuard published this Outbreak Alert report.
Apr 12, 2024: FortiGuard issued a Threat Signal. https://www.fortiguard.com/threat-signal-report/5423/
Apr 11, 2024: Palo Alto Networks released a security advisory on their GlobalProtect. https://security.paloaltonetworks.com/CVE-2024-3400
Apr 10, 2024: Volexity identified zero-day exploitation of a vulnerability found within the GlobalProtect. https://www.volexity.com/blog/2024/04/12/zero-day-exploitation-of-unauthenticated-remote-code-execution-vulnerability-in-globalprotect-cve-2024-3400/
Attack Sequence
Actions taken by cyber attacker or a malicious entity to compromise a target system or network.
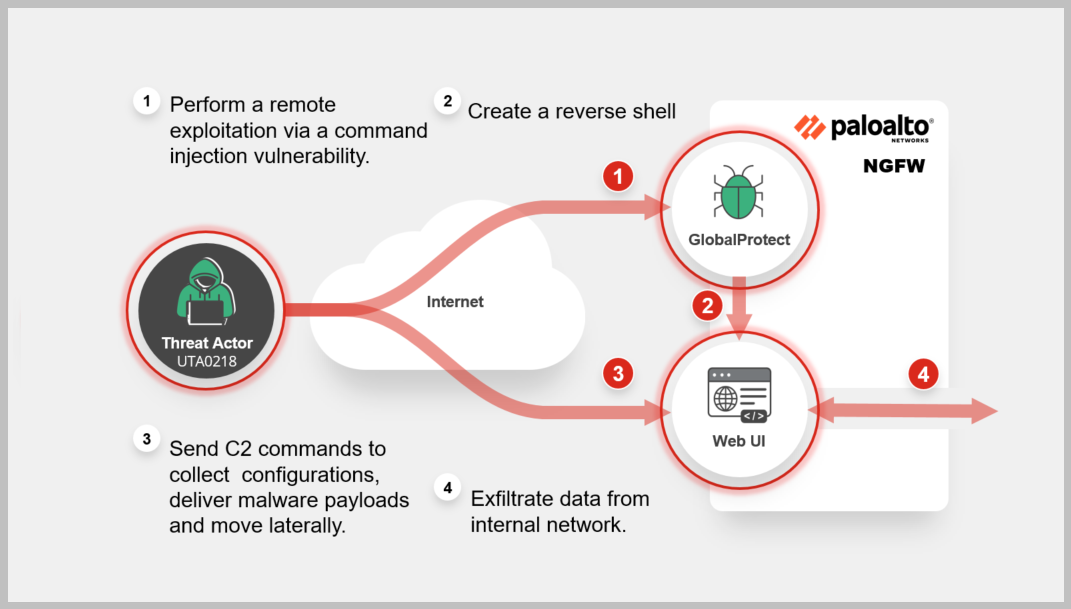
Attack Sequence

Attack Sequence Video
FortiGuard Cybersecurity Framework
Mitigate security threats and vulnerabilities by leveraging the range of FortiGuard Services.
-
Lure
-
Decoy VM
-
AV
-
AV (Pre-filter)
-
IPS
-
Outbreak Detection
-
Threat Hunting
-
Playbook
-
Assisted Response Services
-
Automated Response
-
NOC/SOC Training
-
End-User Training
-
Attack Surface Hardening
-
Inventory Management
-
Business Reputation
Lure
Decoy VM
AV Detects and blocks known malware related to the PAN-OS GlobalProtect Attack (CVE-2024-3400)
AV (Pre-filter) Detects and blocks known malware related to the PAN-OS GlobalProtect Attack (CVE-2024-3400)
IPS Detects and blocks exploitation attempts targeting the PAN-OS Global Protect vulnerability (CVE-2024-3400)
Outbreak Detection
Threat Hunting
Playbook
Assisted Response Services Experts to assist you with analysis, containment and response activities.
Automated Response Services that can automaticlly respond to this outbreak.
NOC/SOC Training Train your network and security professionals and optimize your incident response to stay on top of the cyberattacks.
End-User Training Raise security awareness to your employees that are continuously being targetted by phishing, drive-by download and other forms of cyberattacks.
Attack Surface Hardening Check Security Fabric devices to build actionable configuration recommendations and key indicators.
Inventory Management Check Security Fabric devices to build actionable configuration recommendations and key indicators.
Business Reputation Know attackers next move to protect against your business branding.
Threat Intelligence
Information gathered from analyzing ongoing cybersecurity events including threat actors, their tactics, techniques, and procedures (TTPs), indicators of compromise (IOCs), malware and related vulnerabilities.
Loading ...
 Indicators of compromise
Indicators of compromise
IOC Indicator List
 Indicators of compromise
Indicators of compromise
IOC Threat Activity
Last 30 days
Chg
Avg 0
Mitre Matrix

Click here for the ATT&CK Matrix
References
Sources of information in support and relation to this Outbreak and vendor.