Actively targeted in the wild
CVE-2023-29357 is an authentication bypass vulnerability, which means that adversaries may use it to escalate privileges on affected installations of Microsoft SharePoint Server. If the user is a privileged account, such as an administrator, the attacker will gain elevated privileges. Learn More »
Common Vulnerabilities and Exposures
Background
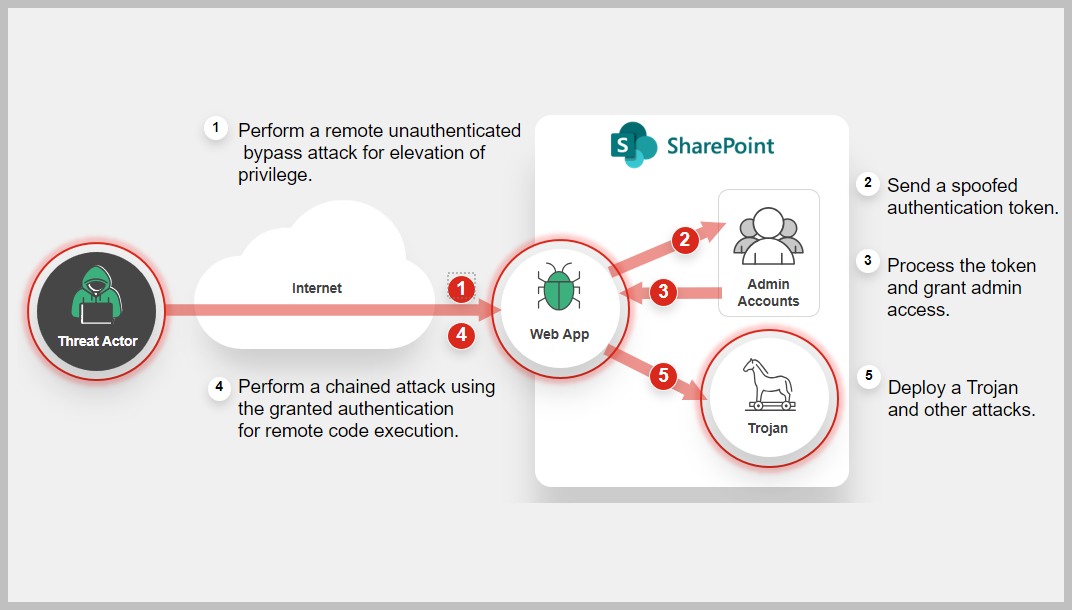
This vulnerability stems from the validation check used to verify JSON Web Tokens (JWTs) used for authentication. An attacker who has gained access to spoofed JWT authentication tokens can use them to bypasses authentication and gain access to the privileges of an authenticated user. Attackers may chain CVE-2023-29357 vulnerability with other vulnerabilities for remote code execution to compromise the integrity, availability, and confidentiality of the target system.
Latest Development
Recent news and incidents related to cybersecurity threats encompassing various events such as data breaches, cyber-attacks, security incidents, and vulnerabilities discovered.
Jun 13, 2023: Microsoft released the advisory and patch guide for the vulnerability (CVE-2023-29357)
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2023-29357
Jan 1, 2024: CISA added CVE-2023-29357 to its known exploited catalog.
Fortinet customers remain protected via the IPS signature service and can detect vulnerable SharePoint servers to CVE-2023-29357. IPS signature has been released since June, 2023 to protect and detect any attack attempts, however users are recommended to apply patches to the vulnerable systems as soon as possible to mitigate any risks if not already done.
FortiGuard Cybersecurity Framework
Mitigate security threats and vulnerabilities by leveraging the range of FortiGuard Services.
-
Vulnerability
-
IPS
-
Outbreak Detection
-
Threat Hunting
-
Assisted Response Services
-
Automated Response
-
NOC/SOC Training
-
End-User Training
-
Vulnerability Management
-
Attack Surface Hardening
-
Business Reputation
Threat Intelligence
Information gathered from analyzing ongoing cybersecurity events including threat actors, their tactics, techniques, and procedures (TTPs), indicators of compromise (IOCs), malware and related vulnerabilities.
Loading ...
References
Sources of information in support and relation to this Outbreak and vendor.