JetBrains TeamCity Authentication Bypass Attack
Watch Video
JetBrains TeamCity Authentication Bypass Attack Video
Advanced Persistent Threat Groups exploiting the flaw in (CI/CD) application
Multiple Threat actors seen exploiting the authentication bypass flaw in JetBrains TeamCity that could lead to remote code execution. If compromised, they can access a TeamCity server, gaining entry to a software developer's source code, signing certificates, and the power to manipulate software building and deployment procedures. This access could also be misused by these malicious actors to carry out supply chain operations. Learn More »
Common Vulnerabilities and Exposures
Background
TeamCity is a continuous integration/continuous deployment (CI/CD) application used by organizations for DevOps and other software development activities. Software developers use TeamCity software to manage and automate software compilation, building, testing, and releasing.
Threat Radar Overall Score: 4.0
| CVSS Rating | 9.0 | |
| FortiRecon Score | 100/100 | |
| Known Exploited | Yes | |
| Exploit Prediction Score | 97.1% | |
| FortiGuard Telemetry | 6633 |
Latest Development
Recent news and incidents related to cybersecurity threats encompassing various events such as data breaches, cyber-attacks, security incidents, and vulnerabilities discovered.
September 6, 2023: Researchers from Sonar discovered a critical TeamCity On-Premises vulnerability (CVE-2023-42793).
September 20, 2023: JetBrains released the advisory and hot fixes for the vulnerability.
https://blog.jetbrains.com/teamcity/2023/09/critical-security-issue-affecting-teamcity-on-premises-update-to-2023-05-4-now/
September 27, 2023: A public exploit for this vulnerability was released by Rapid7.
In mid-October 2023, the FortiGuard Incident Response (IR) team was engaged to investigate a compromised organization's network. See full details on the blog;
https://www.fortinet.com/blog/threat-research/teamcity-intrusion-saga-apt29-suspected-exploiting-cve-2023-42793
Oct 18, 2023: Microsoft Threat Intelligence reported that multiple North Korean threat actors exploiting the TeamCity CVE-2023-42793 vulnerability
https://www.microsoft.com/en-us/security/blog/2023/10/18/multiple-north-korean-threat-actors-exploiting-the-teamcity-cve-2023-42793-vulnerability/
December 13, 2023: FortiGuard Labs released a detailed threat research on a different threat actor, (APT-29) exploiting CVE-2023-42793
https://www.fortinet.com/blog/threat-research/teamcity-intrusion-saga-apt29-suspected-exploiting-cve-2023-42793
December 13, 2023: CISA and Partners Release Advisory on Russian SVR-affiliated Cyber Actors Exploiting CVE-2023-42793
https://www.cisa.gov/news-events/alerts/2023/12/13/cisa-and-partners-release-advisory-russian-svr-affiliated-cyber-actors-exploiting-cve-2023-42793
According to CISA's advisory, as a result of this latest SVR cyber activity, they identified a few dozen compromised companies in the United States, Europe, Asia, and Australia and the Identified victims included: an energy trade association; companies that provide software for billing, medical devices, customer care, employee monitoring, financial management, marketing, sales, and video games; as well as hosting companies, tools manufacturers, and small and large IT companies.
Attack Sequence
Actions taken by cyber attacker or a malicious entity to compromise a target system or network.
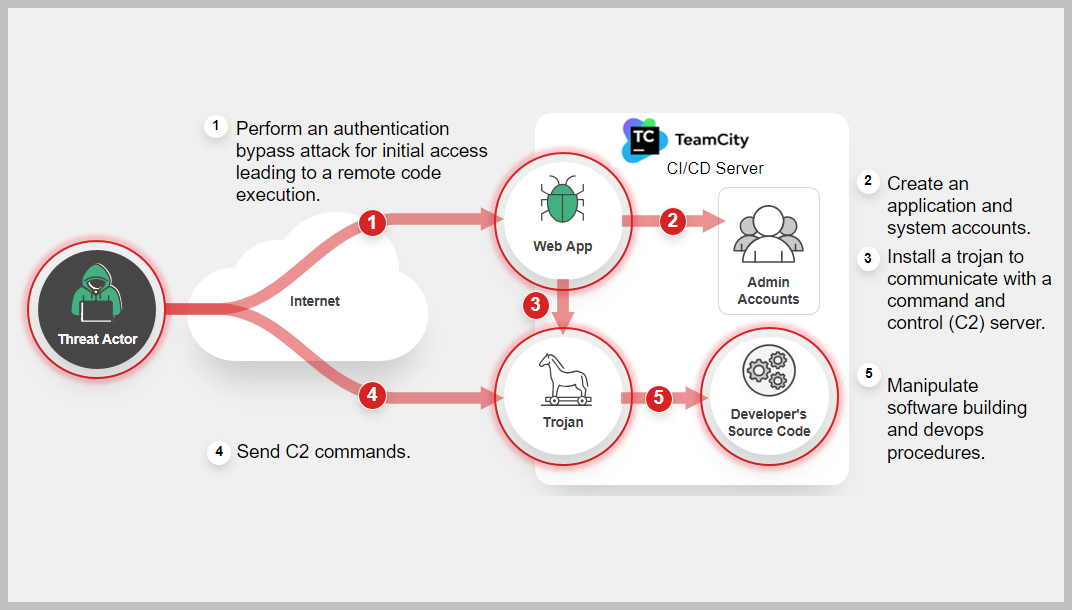
Attack Sequence

Attack Sequence Video
FortiGuard Cybersecurity Framework
Mitigate security threats and vulnerabilities by leveraging the range of FortiGuard Services.
-
AV
-
Vulnerability
-
AV (Pre-filter)
-
IPS
-
Web App Security
-
Web & DNS Filter
-
Botnet C&C
-
Outbreak Detection
-
Threat Hunting
-
Assisted Response Services
-
Automated Response
-
NOC/SOC Training
-
End-User Training
-
Attack Surface Hardening
-
Business Reputation
AV Detects and blocks malware related to JetBrains TeamCity Authentication Bypass Attack (CVE-2023-42793)
Vulnerability Detects vulnerable JetBrains TeamCity application running on the network
AV (Pre-filter) Detects and blocks malware related to JetBrains TeamCity Authentication Bypass Attack (CVE-2023-42793)
IPS Detects and blocks exploitation of JetBrains TeamCity Authentication Bypass Vulnerability (CVE-2023-42793)
Web App Security Detects and blocks exploitation of JetBrains TeamCity Authentication Bypass Vulnerability (CVE-2023-42793)
Web & DNS Filter Known related URL, IPs, Domains are rated as "Malicious "
Botnet C&C Blocks communication with related malicous C2 servers and domains.
Outbreak Detection
Threat Hunting
Assisted Response Services Experts to assist you with analysis, containment and response activities.
Automated Response Services that can automaticlly respond to this outbreak.
NOC/SOC Training Train your network and security professionals and optimize your incident response to stay on top of the cyberattacks.
End-User Training Raise security awareness to your employees that are continuously being targetted by phishing, drive-by download and other forms of cyberattacks.
Attack Surface Hardening Check Security Fabric devices to build actionable configuration recommendations and key indicators.
Business Reputation Know attackers next move to protect against your business branding.
Threat Intelligence
Information gathered from analyzing ongoing cybersecurity events including threat actors, their tactics, techniques, and procedures (TTPs), indicators of compromise (IOCs), malware and related vulnerabilities.
Loading ...
 Indicators of compromise
Indicators of compromise
IOC Indicator List
 Indicators of compromise
Indicators of compromise
IOC Threat Activity
Last 30 days
Chg
Avg 0
Mitre Matrix

Click here for the ATT&CK Matrix
References
Sources of information in support and relation to this Outbreak and vendor.