Zero-day vulnerabilities actively exploited
Widespread exploitation of zero-day vulnerabilities affecting Ivanti Connect Secure and Policy Secure gateways underway. Learn More »
Common Vulnerabilities and Exposures
Background
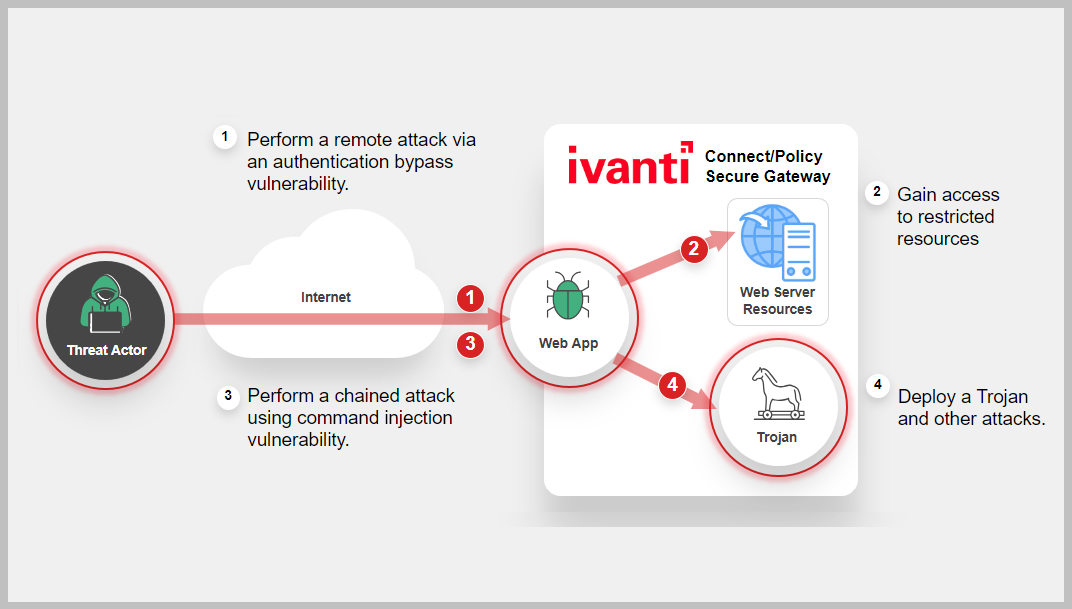
CVE-2023-46805 Is an Authentication Bypass Vulnerability found in the web component of Ivanti Connect Secure (ICS) and Ivanti Policy Secure to allow a remote attacker to access restricted resources by bypassing control checks. CVE-2024-21887 is a command injection vulnerability in web components of ICS and Ivanti Policy Secure. If CVE-2024-21887 is used in conjunction with CVE-2023-46805, exploitation does not require authentication and enables a threat actor to craft malicious requests and execute arbitrary commands on the system.
Latest Development
Recent news and incidents related to cybersecurity threats encompassing various events such as data breaches, cyber-attacks, security incidents, and vulnerabilities discovered.
-
September 02, 2025: People's Republic of China (PRC) state-sponsored cyber threat actors are targeting networks globally.
https://www.cisa.gov/news-events/cybersecurity-advisories/aa25-239a?utm_source=SaltTyphoon&utm_medium=GovDelivery -
June 25, 2024: Skibidi Botnet Malware targets Ivanti Connect Secure Vulnerability (CVE-2024-21887)
https://www.fortinet.com/blog/threat-research/growing-threat-of-malware-concealed-behind-cloud-services -
February 29, 2024: CISA released a Cybersecurity Advisory on Threat Actors Exploiting Vulnerabilities in Ivanti Connect Secure and Policy Secure Gateways
https://www.cisa.gov/news-events/cybersecurity-advisories/aa24-060b/nz -
February 13, 2024: A new report by Orange Cyberdefense shows attackers using CVE-2024-21893 to install a new backdoor named DSLog. Please note, this is an ongoing investigation and as the situation is evolving, FortiGuard Labs will update and add new protections accordingly.
https://www.orangecyberdefense.com/fileadmin/general/pdf/Ivanti_Connect_Secure_-_Journey_to_the_core_of_the_DSLog_backdoor.pdf -
February 09, 2024: Ivanti disclosed a fifth vulnerability- CVE-2024-22024 (XXE) for ICS and Ivanti Policy Secure.
https://forums.ivanti.com/s/article/CVE-2024-22024-XXE-for-Ivanti-Connect-Secure-and-Ivanti-Policy-Secure?language=en_US -
February 01, 2024: Ivanti identified additional vulnerabilities in ICS and Ivanti Policy Secure, and Ivanti Neurons for ZTA. CVE-2024-21888 allows for privilege escalation and CVE-2024-21893 is a server-side request forgery in the SAML component which allows a threat actor to access certain restricted resources without authentication. Vendor mentions in the advisory that CVE-2024-21893 appears to be seen in some targeted attacks and expects an increase in the attacks. CVE-2024-21893 has also been added to CISA's known exploited vulnerability catalog (KEV).
-
January 22, 2024: FortiGuard Labs has released IPS signatures to detect and block Authentication Bypass (CVE-2023-46805) and Server-Side Request Forgery Vulnerability (CVE-2024-21893) is observing high IPS activity since the release of the signatures.
-
January 22, 2024: Ivanti plans to begin releasing patches addressing these vulnerabilities on a schedule. Until patches are available, Ivanti has provided a workaround for the users to mitigate exploitation risks
https://forums.ivanti.com/s/article/KB-CVE-2023-46805-Authentication-Bypass-CVE-2024-21887-Command-Injection-for-Ivanti-Connect-Secure-and-Ivanti-Policy-Secure-Gateways -
January 19, 2024: CISA released a Cybersecurity Advisory on Threat Actors Exploiting Vulnerabilities in Ivanti Connect Secure and Policy Secure Gateways
https://www.cisa.gov/news-events/directives/ed-24-01-mitigate-ivanti-connect-secure-and-ivanti-policy-secure-vulnerabilities
FortiGuard Cybersecurity Framework
Mitigate security threats and vulnerabilities by leveraging the range of FortiGuard Services.
-
Lure
-
Decoy VM
-
AV
-
AV (Pre-filter)
-
IPS
-
Web App Security
-
IOC
-
Outbreak Detection
-
Threat Hunting
-
Automated Response
-
Assisted Response Services
-
NOC/SOC Training
-
End-User Training
-
Attack Surface Hardening
-
Attack Surface Monitoring (Inside & Outside)
Threat Intelligence
Information gathered from analyzing ongoing cybersecurity events including threat actors, their tactics, techniques, and procedures (TTPs), indicators of compromise (IOCs), malware and related vulnerabilities.
References
Sources of information in support and relation to this Outbreak and vendor.