ConnectWise ScreenConnect Attack
Watch Video
ConnectWise ScreenConnect Attack Video
An IT remote access tool actively targeted
Threat actors including ransomware gangs are seen exploiting newly discovered critical flaws in remote monitoring and management software called ScreenConnect. Learn More »
Common Vulnerabilities and Exposures
Background
One of the flaws, CVE-2024-1709 is an authentication bypass vulnerability using an alternate path or channel that could let attackers gain administrative access to a ScreenConnect instance. The second flaw tracked as CVE-2024-1708 is a path traversal vulnerability that may allow an attacker to execute remote code. According to Shadowserver, around 8200 vulnerable ConnectWise ScreenConnect instances were found on the internet and 643 IPs were observed attacking it. According to the company website, ConnectWise remote-access software is one of the leading providers used by Managed service providers (MSPs) to remotely connect to their customer's systems. This could pose a significant threat to end user's systems that could be targeted downstream and can allow hackers to plant malicious code remotely.
Threat Radar Overall Score: 4.2
| CVSS Rating | 10.0 | |
| FortiRecon Score | 96/100 | |
| Known Exploited | Yes | |
| Exploit Prediction Score | 94.46% | |
| FortiGuard Telemetry | 7187 |
Latest Development
Recent news and incidents related to cybersecurity threats encompassing various events such as data breaches, cyber-attacks, security incidents, and vulnerabilities discovered.
February 19, 2024: ConnectWise published a security advisory and has released a patch covering both vulnerabilities.
https://www.connectwise.com/company/trust/security-bulletins/connectwise-screenconnect-23.9.8
February 21, 2024: Proof of Concept (PoC) code was released on GitHub.
February 22, 2024: CVE-2024-1709 was added to CISA's known exploited catalog.
https://www.cisa.gov/known-exploited-vulnerabilities-catalog
February 22, 2024: FortiGuard Labs released a Threat Signal on ConnectWise ScreenConnect Vulnerabilities (CVE-2024-1708 and CVE-2024-1709)
https://www.fortiguard.com/threat-signal-report/5389/
March 07, 2024: FortiGuard MDR and the FortiGuard IR team responded to several incidents related to exploitation of ConnectWise ScreenConnect and has released a detailed analysis. https://community.fortinet.com/t5/FortiEDR/Threat-Coverage-How-FortiEDR-protects-against-post-exploitation/ta-p/303439
FortiGuard Labs recommends companies to apply the most recent upgrade or patch from the vendor as soon as possible.
Attack Sequence
Actions taken by cyber attacker or a malicious entity to compromise a target system or network.
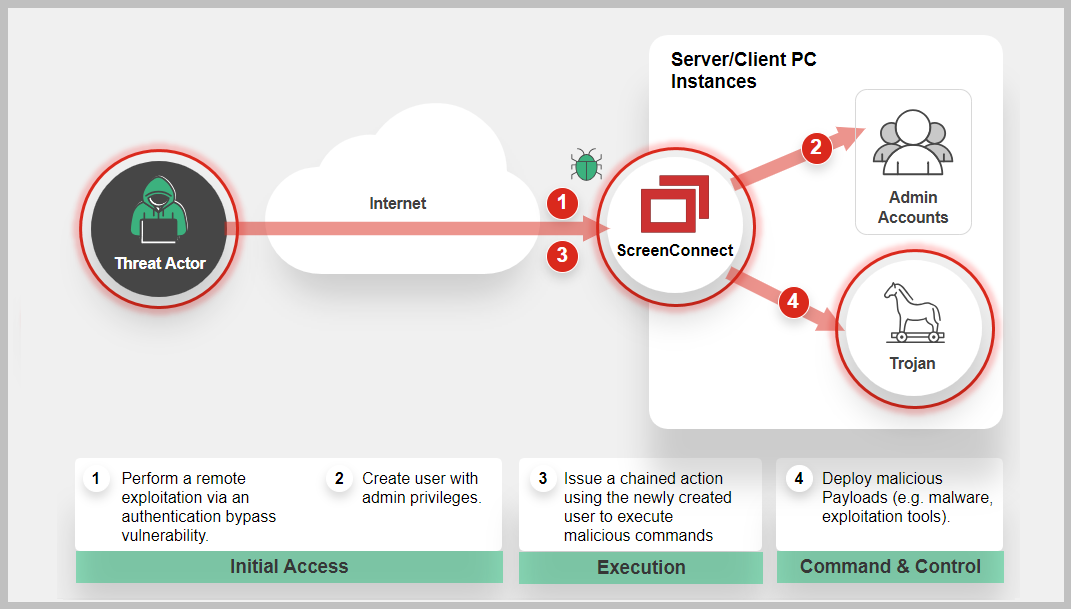
Attack Sequence

Attack Sequence Video
FortiGuard Cybersecurity Framework
Mitigate security threats and vulnerabilities by leveraging the range of FortiGuard Services.
-
Lure
-
Decoy VM
-
AV
-
Vulnerability
-
AV (Pre-filter)
-
IPS
-
Outbreak Detection
-
Threat Hunting
-
IOC
-
Playbook
-
Assisted Response Services
-
Automated Response
-
NOC/SOC Training
-
End-User Training
-
Vulnerability Management
-
Attack Surface Hardening
-
Business Reputation
Lure Redirect an attacker to engage with a decoy instead of a real ConnectWise ScreenConnect
Decoy VM Detects attack attemtps and monitor malicious activities on the network
AV Detects known malware related to ConnectWise ScreenConnect Attack
Vulnerability Detects vulnerable ScreenConnect software installed on the network (CVE-2024-1708 and CVE-2024-1709)
AV (Pre-filter) Detects known malware related to ConnectWise ScreenConnect Attack
IPS Detects and blocks attack attempts targeting ConnectWise ScreenConnect Auth bypass (CVE-2024-1709 & CVE-2024-1708)
Outbreak Detection
Threat Hunting
Playbook
Assisted Response Services Experts to assist you with analysis, containment and response activities.
Automated Response Services that can automaticlly respond to this outbreak.
NOC/SOC Training Train your network and security professionals and optimize your incident response to stay on top of the cyberattacks.
End-User Training Raise security awareness to your employees that are continuously being targetted by phishing, drive-by download and other forms of cyberattacks.
Vulnerability Management Reduce the attack surface on software vulnerabilities via systematic and automated patching.
Attack Surface Hardening Check Security Fabric devices to build actionable configuration recommendations and key indicators.
Business Reputation Know attackers next move to protect against your business branding.
Threat Intelligence
Information gathered from analyzing ongoing cybersecurity events including threat actors, their tactics, techniques, and procedures (TTPs), indicators of compromise (IOCs), malware and related vulnerabilities.
Loading ...
 Indicators of compromise
Indicators of compromise
IOC Indicator List
 Indicators of compromise
Indicators of compromise
IOC Threat Activity
Last 30 days
Chg
Avg 0
Mitre Matrix

Click here for the ATT&CK Matrix
References
Sources of information in support and relation to this Outbreak and vendor.