Multiple 0-Day vulnerabilities on Cisco IOS XE Web UI
Active exploitation of a previously unknown vulnerabilities in the Web User Interface (Web UI) of Cisco IOS XE software when exposed to the internet or untrusted networks. According to open source articles, thousands of vulnerable devices have been compromised. Learn More »
Common Vulnerabilities and Exposures
Background
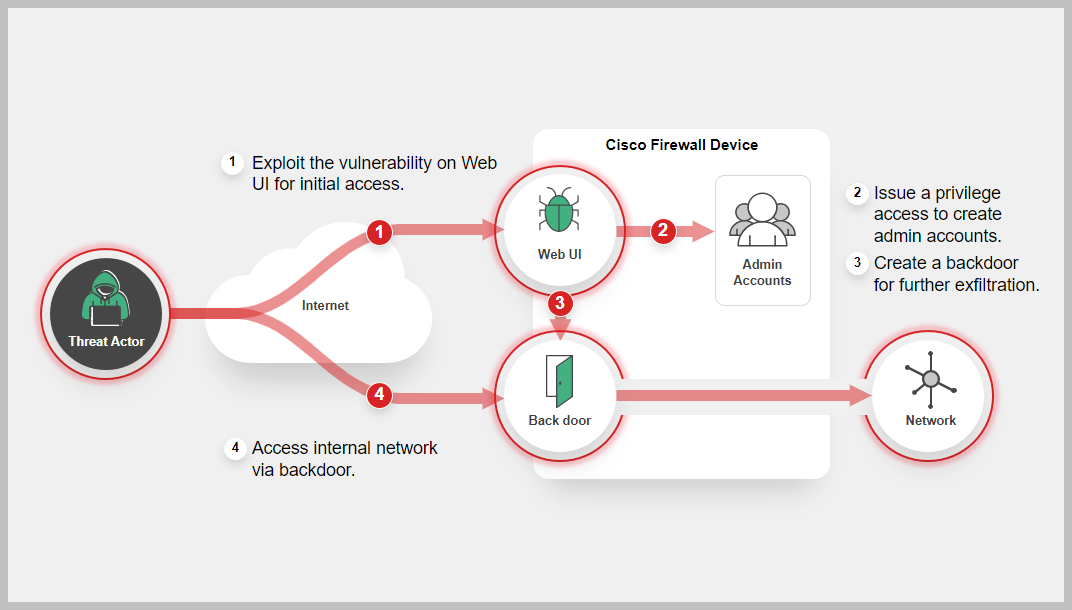
Cisco IOS XE is the internetworking operating system used by the Next-Generation Cisco Systems such as routers and switches. The Web User Interface (WebUI) provides simplified deployment and manageability of the devices. According to the vendor report, this vulnerability (CVE-2023-20198) allows a remote, unauthenticated attacker to create an account on an affected system. The attacker can then use that account to gain control of the affected system including installing a backdoor. Next, the attacker can use the new unauthorized local user account to exploit a second previously unknown vulnerability (CVE-2023-20273) in another component of the WebUI feature. This allows the adversary to inject commands with elevated (root) privileges, giving them the ability to run arbitrary commands on the device.
Latest Development
Recent news and incidents related to cybersecurity threats encompassing various events such as data breaches, cyber-attacks, security incidents, and vulnerabilities discovered.
Oct 16, 2023: Cisco released an advisory for CVE-2023-20198
https://sec.cloudapps.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-iosxe-webui-privesc-j22SaA4z
Oct 16, 2023: Cisco Talos released a detailed blog about the CVE-2023-20198 vulnerability and its active exploitation.
https://blog.talosintelligence.com/active-exploitation-of-cisco-ios-xe-software/
Oct 16, 2023: FortiGuard Labs released a Threat Signal for the vulnerability (CVE-2023-20198)
https://www.fortiguard.com/threat-signal-report/5293
Oct 19, 2023: CISA added CVE-2023-20198 to its known exploited list (KEV) Catalog.
https://www.cisa.gov/known-exploited-vulnerabilities-catalog
Oct 20, 2023: Cisco identified an additional vulnerability (CVE-2023-20273) that is exploited to deploy the implant. Fixes for both CVE-2023-20198 and CVE-2023-20273 are estimated to be available on October 22 according to the vendor advisory. Please see the following link for software fix availability:
https://www.cisco.com/c/en/us/support/docs/ios-nx-os-software/ios-xe-dublin-17121/221128-software-fix-availability-for-cisco-ios.html
FortiGuard Cybersecurity Framework
Mitigate security threats and vulnerabilities by leveraging the range of FortiGuard Services.
-
Lure
-
Decoy VM
-
IPS
-
Web App Security
-
Outbreak Detection
-
Threat Hunting
-
Content Update
-
Assisted Response Services
-
Automated Response
-
NOC/SOC Training
-
End-User Training
-
Attack Surface Hardening
-
Business Reputation
Threat Intelligence
Information gathered from analyzing ongoing cybersecurity events including threat actors, their tactics, techniques, and procedures (TTPs), indicators of compromise (IOCs), malware and related vulnerabilities.
Loading ...
References
Sources of information in support and relation to this Outbreak and vendor.