W32/NetWalker.B!tr.ransom
 Analysis
Analysis
W32/NetWalker.B!tr.ransom is a generic detection for a ransomware trojan.
Since this is a generic detection, malware that are detected as W32/NetWalker.B!tr.ransom may have varying behaviour.
Below are some of its observed characteristics/behaviours:
- This malware is associated with the NetWalker ransomware family.
- This ransomware utilizes "vssadmin.exe" to delete all shadow copies to prevent system recovery.
- It will traverse through the victim's system, targeting files with a specific file extension to encrypt. Some files excluded from the encryption process include those with the file extension ".exe", ".dll", ".ini", ".msi" and ".pdf". The encrypted files will be appended with an extension consisting of 6 characters which will be referenced in the ransom note.
- Following the encryption process the malware will delete itself and a ransom note, with the name "[6CharacterExtension]-Readme.txt", will be dropped to the desktop and opened. A ransom note will also be dropped into every directory containing encrypted files. The note will instruct the victim to make contact with the attacker via a TOR site. Affected users are discouraged on taking this action as it does not guarantee the retrieval of data upon payment.
- Below are images of the result of executing the ransomware:
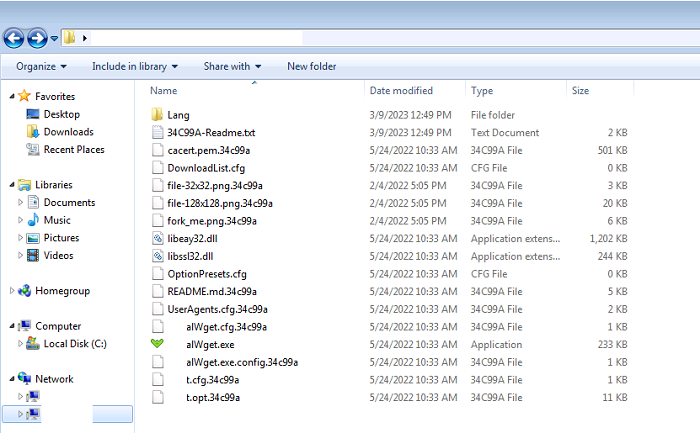
- Figure 1: Encrypted files
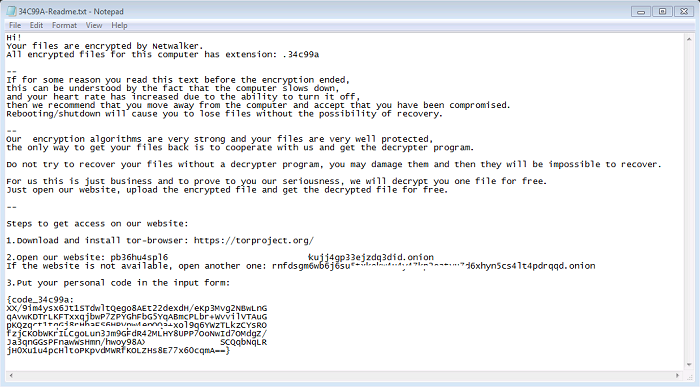
- Figure 2: Ransom note.
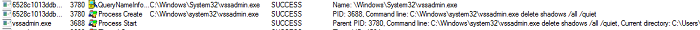
- Figure 3: Delete shadow copies.
- Below are some of the sites associated with the ransomware:
- pb36hu4spl[removed]kujj4gp33ejzdq3did.onion
- rnfdsgm6wb6j6su5txkekw[removed]n5cs4lt4pdrqqd.onion
- Following are some of the exact file hashes associated with this detection:
- Md5: 63eb7712d7c9d495e8a6be937bdb1960
Sha256: 0d0ed90929351c08c47dbd7541073d037240718c4a2fd63c09d2377090d4cd7a - Md5: 6528c1013ddb23f6eeca08d02f3d7834
Sha256: c677014c312b87da89362fbd16f7abf7ba5546220000bfdaa0f77bba1edf5144 - Md5: d09cfda29f178f57dbce6895cfb68372
Sha256: f298725e197f974b7a8407c5d79114a4ac322c573813d543141ccf1d9119dd8b
- Md5: 63eb7712d7c9d495e8a6be937bdb1960
 Outbreak Alert
Outbreak Alert
Versions prior to R1 2020 (2020.1.114) are susceptible to remote code execution attacks on affected web servers of Telerik User Interface (UI) for ASP-NET due to a deserialization vulnerability found in RadAsyncUpload function. FortiGuard Labs continue seeing high exploitation activity of these old vulnerabilities.
 Recommended Action
Recommended Action
- Make sure that your FortiGate/FortiClient system is using the latest AV database.
- Quarantine/delete files that are detected and replace infected files with clean backup copies.
Detection Availability
| FortiGate | |
|---|---|
| FortiClient | |
| FortiAPS | |
| FortiAPU | |
| FortiMail | |
| FortiSandbox | |
| FortiWeb | |
| FortiADC | |
| FortiIsolator | |
| FortiDeceptor | |
| FortiEDR |
Version Updates
| Date | Version | Status | Detail |
|---|---|---|---|
| 2025-03-18 | 93.01781 |
Modified
|
|
| 2025-03-17 | 93.01758 |
Modified
|
|
| 2023-09-05 | 91.06684 |
Modified
|
|
| 2023-03-16 | 91.01487 |
Modified
|
|
| 2023-03-09 | 91.01272 |
Modified
|
|
| 2023-03-08 | 91.01247 |
Modified
|
|
| 2020-06-02 | 77.87200 |
Modified
|
Sig Updated |
| 2020-03-20 | 76.10200 |
Modified
|
Sig Updated |
| 2020-03-12 | 75.91800 |
New
|
Sig Added |