MSIL/Filecoder.RI!tr.ransom
 Analysis
Analysis
MSIL/Filecoder.RI!tr.ransom is a generic detection for a Ransomware trojan. Since this is a generic detection, this malware may have varying behaviour.
Below are some of its observed characteristics/behaviours:
- This ransomware masquerades as an Amazon application and go to the Amazon website when the user runs it as a administrator.
- Affected victims of this Ransomware are redirected by the attacker via:
- johnnydiab@campus.technion.ac.il
- nhulaihel@campus.technion.ac.il
- The ransomware connects to the website hxxps://fransomware.azurewebsites.net/api/initialConnection to indicate the new infection and to initiate encryption. At the time of our replication, the results could not be reproduced because of inactive URL.
- This ransomware charges different bitcoin amount for decryption depending on file priority as shown in figure 3.
- This ransomware may skip the following folders from encryption:
- ZoneAlarm
- AVG
- Panda
- TheHacker
- BitDefender
- eScan
- Trapmine
- Avast
- McAfee
- Program Files
- Program Files (x86)
- Windows
- Windows.old
- GoogleDrive
- OneDrive
- Downloads
- While encrypting files it looks for following keywords:
- family
- client
- project
- wedding
- trip
- important
- password
- code
- It encrypts the files with following file extensions:
- .csv
- .html
- .xml
- .c
- .cpp
- .java
- .py
- .cs
- .class
- .sql
- .psb
- .psd
- .eps
- .ai
- .png
- .icp
- .jpeg
- .jpg
- .bmp
- .dib
- .ps
- .svg
- .tif
- .tiff
- .jfif
- .gif
- .aif
- .wav
- .cda
- .mp3
- .wma
- .wpl
- .mpa
- .mid
- .doc
- .docx
- .ppt
- .pptx
- .pptn
- .key
- .odp
- .pps
- .xls
- .xlsx
- .txt
- .doc
- .docx
- .xls
- .xlsx
- .ppt
- .pptx
- .odt
- .jpg
- .png
- .csv
- .sql
- .mdb
- .sln
- .php
- .asp
- .aspx
- .html
- .xml
- .psd
- It deletes the shadow volume copies so that the user cannot restore them.
- This ransomware kills the following processes from running:
- sqlserever.exe
- sqlwriter.exe
- mysqld.exe
- Microsoft.Exchage
- MSExchange
- This ransomware modifies the following registry entries:
- HKLM\SOFTWARE\Policies\Microsoft\Windows Defender
- DisableAntiSpyware = 1
- HKLM\SOFTWARE\Policies\Microsoft\Windows Defender\Real-Time Protection
- DisableBehaviorMonitoring = 1
- HKLM\SOFTWARE\Policies\Microsoft\Windows Defender\Real-Time Protection
- DisableOnAccessProtection = 1
- HKLM\SOFTWARE\Policies\Microsoft\Windows Defender\Real-Time Protection
- DisableScanOnRealtimeEnable = 1
- HKLM\SOFTWARE\Policies\Microsoft\Windows Defender
- Below is an illustration of the malware's Ransom notes:
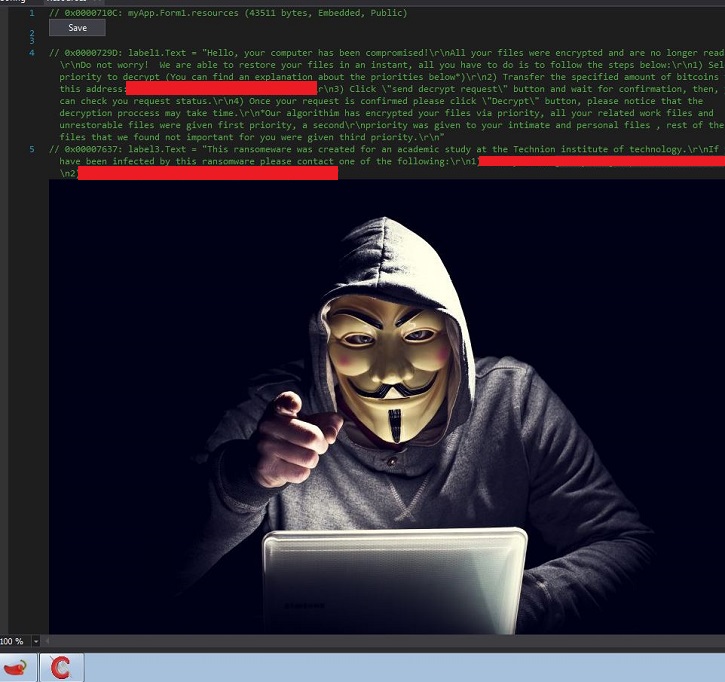
- Figure 1: Ransom note.
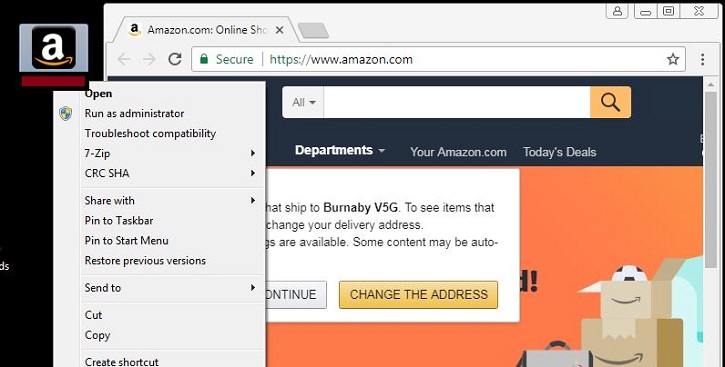
- Figure 2: Masquerades as an Amazon application.
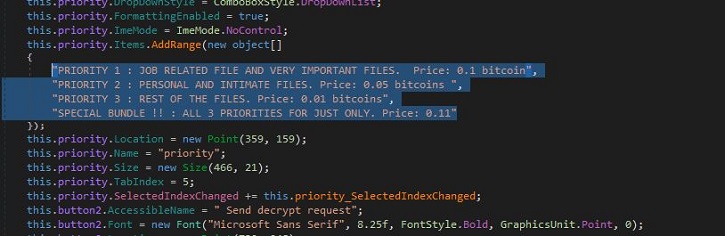
- Figure 3: Different bitcoin amount depending on file priority.
 Recommended Action
Recommended Action
- Make sure that your FortiGate/FortiClient system is using the latest AV database.
- Quarantine/delete files that are detected and replace infected files with clean backup copies.
 Telemetry
Telemetry
Detection Availability
| FortiClient | |
|---|---|
| Extreme | |
| FortiMail | |
| Extreme | |
| FortiSandbox | |
| Extreme | |
| FortiWeb | |
| Extreme | |
| Web Application Firewall | |
| Extreme | |
| FortiIsolator | |
| Extreme | |
| FortiDeceptor | |
| Extreme | |
| FortiEDR |