 Analysis
Analysis
W32/Xorist.DD8C!tr.ransom is a generic detection for a Ransomware Xorist trojan.
Since this is a generic detection, this malware may have varying behaviour.
Below are some of its observed characteristics/behaviours:
- This malware may drop any of the following file(s):
- HOW TO DECRYPT FILES.txt : This file is a text file and will serve as ransom note. It is dropped in every infected folder.
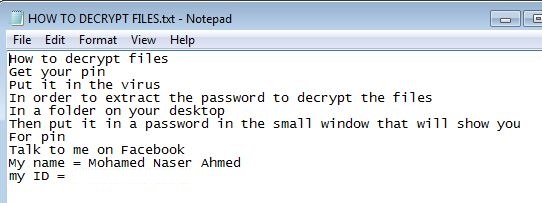
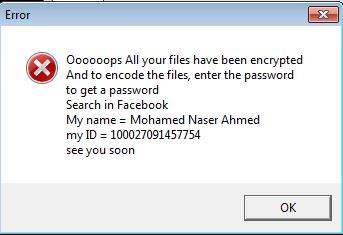
- how to decrypt files.txt facebook contact Ahmed Mohamed Naser : This file is a text file and will serve as ransom note. It is dropped in every infected folder.
- %Temp%\XXXXXXXXXXXXXXX.exe : This file is currently detected as W32/Xorist.DD8C!tr.ransom. For some variants, this file is the copy of the original malware itself. Here X is any alphanumeric character.
- %Temp%\svchost.exe : This file is currently detected as W32/Xorist.DD8C!tr.ransom .
One variant of this Ransomware can be downloaded through the obfuscated JavaScript file spread through the spam email. The description for that JavaScript file can be found as : JS/Xorist.DD8C!tr.ransom .
Affected files of this Ransomware will use the filenaming format:
- {OriginalMalware.Ext}....PAY_IN_MAXIM_24_HOURS_OR_ALL_YOUR_FILES_WILL_BE_PERMANENTLY_DELETED_PLEASE_BE_REZONABLE_you_have_only_1_single_chance_to_make_the_payment.
- {Originalfilename.Ext}.Boom
- {Originalfilename.Ext}.EnCiPhErEd
This malware was also observed to affect/encrypt files located on shared drived within the same subnet.
Affected victims of this Ransomware are redirected by the attacker via:
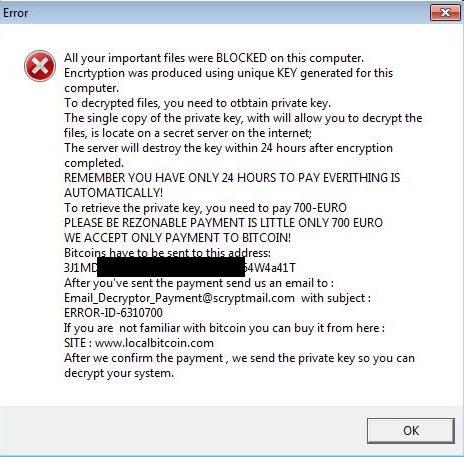
- Email_Decryptor_Payment@scryptmail.com
This malware may apply any of the following registry modification(s):
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\Currentversion\Run
- Alcmeter = %Temp%\XXXXXXXXXXXXXXX.exe
The malware configures itself to run every time any user logs on to the infected system.
- HKEY_LOCAL_MACHINE\Software\Wow6432node\Microsoft\Windows\Currentversion\Run
- Alcmeter = %Temp%\XXXXXXXXXXXXXXX.exe
The malware configures itself to run every time any user logs on to the infected system.
This Ransomware may kill the following processes:
- Taskhost.exe
- Outlook.exe
- Iexplorer.exe
- Winmail.exe
- explorer.exe
Below is an illustration of the malware's Ransom notes:
 Analysis
Analysis


 Recommended Action
Recommended Action Telemetry
Telemetry