INF/Agent.380C!tr
 Analysis
Analysis
LNK/Agent.380C!tr.dldr is a generic detection for a URL shortcut Downloader trojan. Since this is a generic detection, malware that are detected as LNK/Agent.380C!tr.dldr may have varying behaviour.
Below are examples of some of these behaviours:
- This internet shortcut malware directs victims to a malicious JavaScript that has been seen to download the QuantLoader virus that is capable of downloading other malware onto the infected system.
- Listed below are some of the URL's observed where the URL are pointing to:
- rightote{Removed}.com/documents/U189486343.js
- 16{Removed}.239.128.144/documents/FF69E.wsf
- enreclittdosan{Removed}.in/documents/Purchase Order_1869496987546_27032018.wsf
- 16{Removed}.239.128.129/media_source/VM_03-04-2018_2872025.wsf
- There was an instance of this malware that managed to download/drop a file as %AppData%\Roaming\[Random]\dwm.exe and is currently detected as W32/GenKryptik.BUUI!tr.
- This malware was observed to have been distributed as a zipped file attachement to some of the spam mails indicated below:
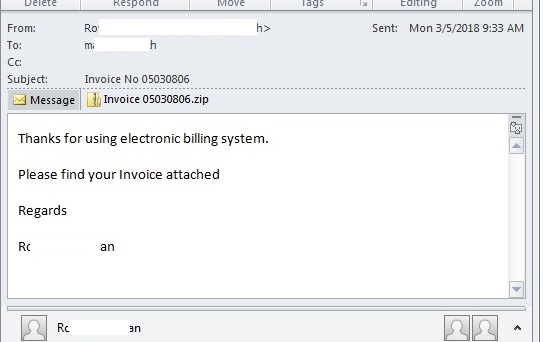
- Figure 1: Spammed mail.
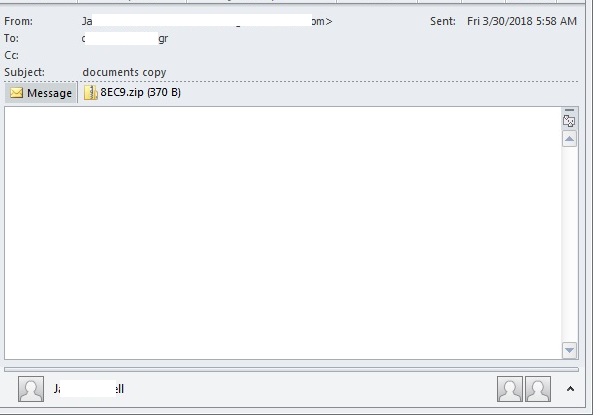
- Figure 2: Spammed mail.
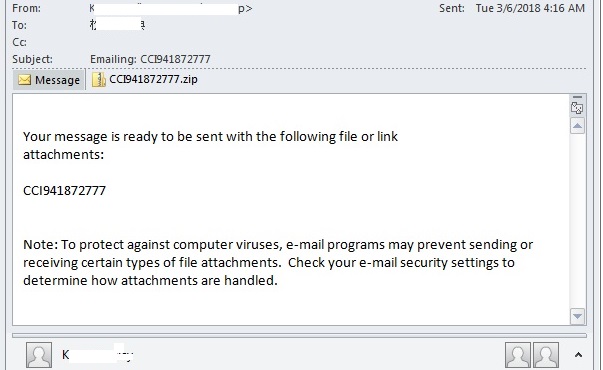
- Figure 3: Spammed mail.
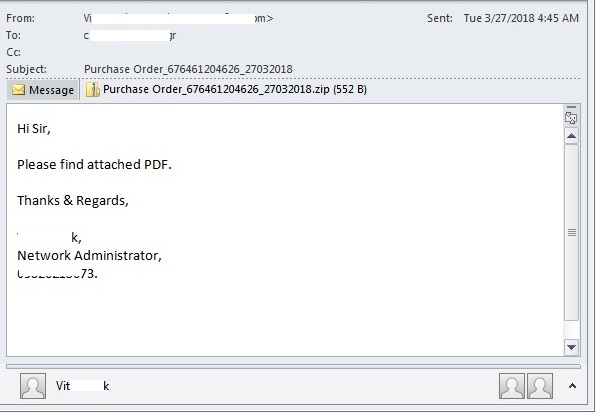
- Figure 4: Spammed mail.
 Recommended Action
Recommended Action
- Make sure that your FortiGate/FortiClient system is using the latest AV database.
- Quarantine/delete files that are detected and replace infected files with clean backup copies.
 Telemetry
Telemetry
Detection Availability
| FortiGate | |
|---|---|
| FortiClient | |
| FortiAPS | |
| FortiAPU | |
| FortiMail | |
| FortiSandbox | |
| FortiWeb | |
| Web Application Firewall | |
| FortiIsolator | |
| FortiDeceptor | |
| FortiEDR |