MSOffice/CVE_2017_11882.A!exploit
 Analysis
Analysis
MSOffice/CVE_2017_11882.A!exploit detects Microsoft Office documents that may be exploiting a memory corruption vulnerability in the EQNEDT32.EXE executable that can be invoked via an older suite of Microsoft Office of products.
For more details, please visist: CVE 2017-11882 exploit
- Most commonly encountered is a Rich-Text Format (RTF) file with the extension .rtf. The file may appear to be empty or show text like the following images:
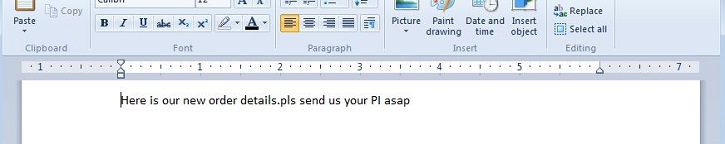
- Figure 1: Text in malicious RTF Document.
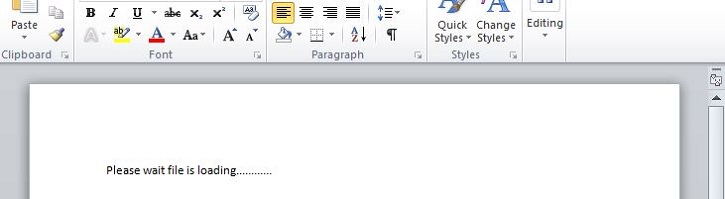
- Figure 2: Text in malicious RTF Document.
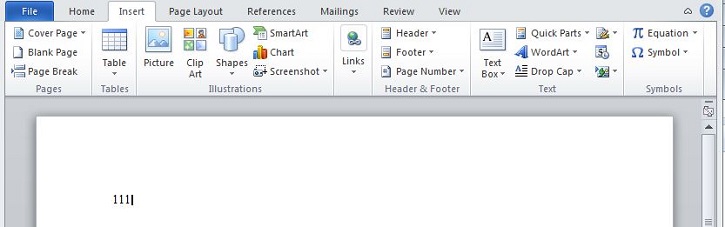
- Figure 3: Text in malicious RTF Document.
- When the file is opened, the following popup error message may show:
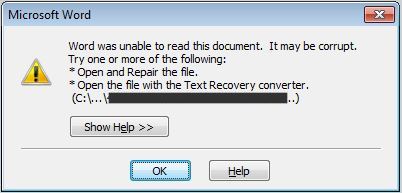
- Figure 4: Error Message.
- When the file is opened, the following securtiy alert message may show:
- Figure 5: Security Alert Message.
- When the file is run in MS Word or Wordpad, a call to a domain may be triggered in the background. The following domain(s) have been observed:
- http://atgro{Removed}.lk
- https://windo{Removed}.erlivia.ltd
- http://jopitt{Removed}.zapto.org
- http://fiebig{Removed}.us
- http://www.uwao{Removed}.info
- http://www.al-enay{Removed}.com
- The file may attempt to download any of the following:
- atgro{Removed}.lk/wp-login/zgnU.hta - Removed from website
- windo{Removed}.erlivia.ltd/plugin/windows-plugin.hta - Removed from website
- jopitt{Removed}.zapto.org/jose/jose.html - Removed from website
 Recommended Action
Recommended Action
- Make sure that your FortiGate/FortiClient system is using the latest AV database.
- Quarantine/delete files that are detected and replace infected files with clean backup copies.
Detection Availability
| FortiGate | |
|---|---|
| FortiClient | |
| FortiAPS | |
| FortiAPU | |
| FortiMail | |
| FortiSandbox | |
| FortiWeb | |
| FortiADC | |
| FortiIsolator | |
| FortiDeceptor | |
| FortiEDR |
Version Updates
| Date | Version | Status | Detail |
|---|---|---|---|
| 2025-05-12 | 93.03085 |
Modified
|
|
| 2024-10-09 | 92.07911 |
Modified
|
|
| 2024-07-08 | 92.05673 |
Modified
|
|
| 2024-03-17 | 92.02550 |
Modified
|
|
| 2024-01-02 | 92.00281 |
Modified
|
|
| 2023-11-20 | 91.08981 |
Modified
|
|
| 2023-07-11 | 91.05011 |
Modified
|
|
| 2023-07-05 | 91.04826 |
Modified
|
|
| 2023-07-04 | 91.04805 |
Modified
|
|
| 2023-01-24 | 90.09944 |
Modified
|