Android/BdMir.A!tr
 Analysis
Analysis
Android/BadMirror.A!tr is a malware which targets Android mobile devices.
It creates a pop up notification bubble with additional APKs for users to download and sends private information of the user's phone to a remote server. ( device board, brand, cpu, imei, imsi, mac, model, etc )
It may also execute commands from the server like downloading an app or viewing a URL.
Technical Details
The malware comes packaged as mobi.upgk1.kcjx.
A pop up notification bubble will appear once the malware parses the JSON object from the server for the APKs that can be downloaded.
Figure 1.

Figure 2.
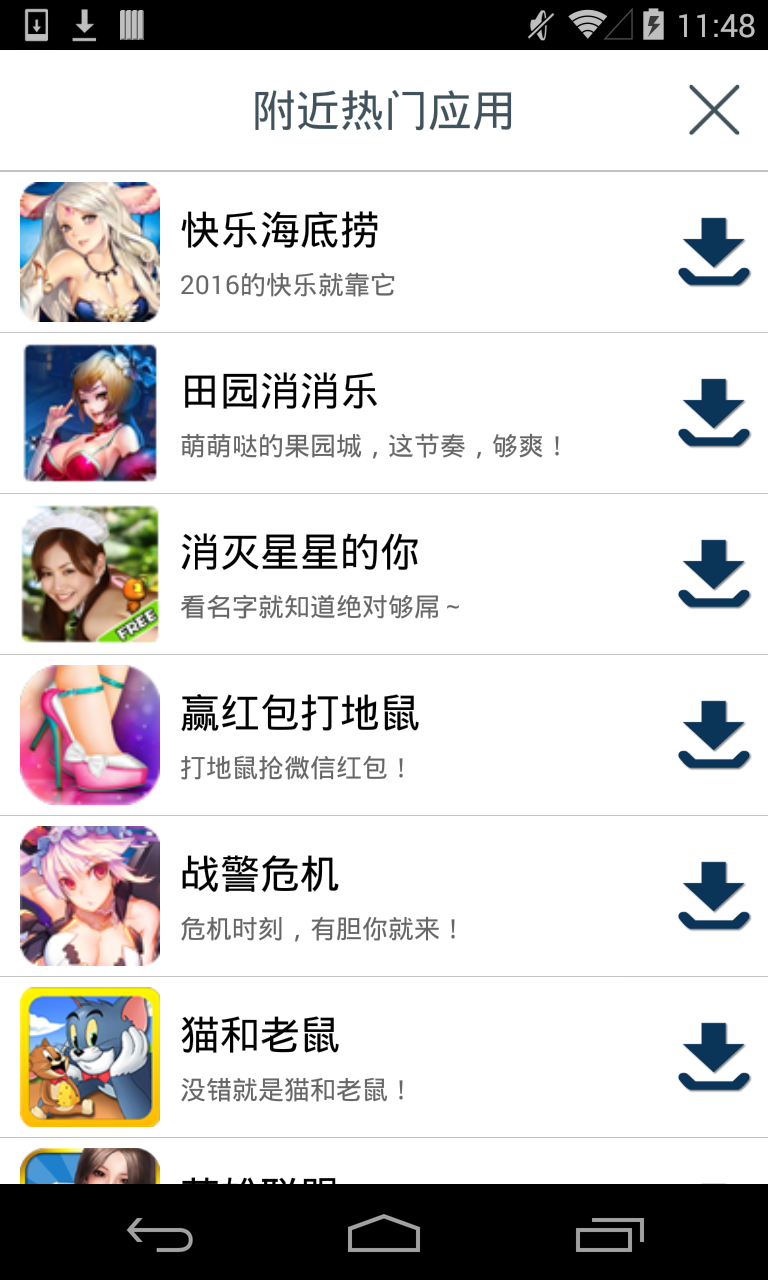
In the background, the malware first checks if there is an update to the app. Then it pushes the phone's information to the server. The information includes:
The malware has the potential to execute commands based on the JSON object response from the server like downloading an APK or viewing a URL.
- when a "apk" command is received: "Buffer setted"
- when a SETP command is received: "Number setted". The SMS also contains the phone's IMEI and model.
The malware installs the following files on the device:
- ./resources.arsc
- ./assets/ck
- ./assets/data.jpg
- ./assets/pd
- ./assets/pkg
- ./AndroidManifest.xml
- ./res/color/*
- ./res/drawable/*
- ./res/drawable-hdpi/*
- ./res/drawable-ldpi/*
- ./res/drawable-v11/*
- ./res/drawable-xhdpi/*
- ./res/layout/*
- ./res/layout-large/*
- ./res/layout-v14/*
- ./res/layout-xlarge/*
- ./res/menu/*
- ./classes.dex
- ./META-INF/ALI10314.RSA
- ./META-INF/ALI10314.SF
- ./META-INF/MANIFEST.MF
- READ_PHONE_STATE
- SYSTEM_ALERT_WINDOW
- CAMERA
- GET_TASKS
- WRITE_EXTERNAL_STORAGE
- INTERNET
- ACCESS_WIFI_STATE
- ACCESS_NETWORK_STATE
 Recommended Action
Recommended Action
- Make sure that your FortiGate/FortiClient system is using the latest AV database.
- Quarantine/delete files that are detected and replace infected files with clean backup copies.
 Telemetry
Telemetry
Detection Availability
| FortiGate | |
|---|---|
| Extreme | |
| FortiClient | |
| Extended | |
| FortiMail | |
| Extended | |
| FortiSandbox | |
| Extended | |
| FortiWeb | |
| Extended | |
| Web Application Firewall | |
| Extended | |
| FortiIsolator | |
| Extended | |
| FortiDeceptor | |
| Extended | |
| FortiEDR |