Linux/RedGo.REAL!tr
 Analysis
Analysis
Linux/RedGo.REAL!tr is a generic detection for a trojan.
Since this is a generic detection, malware that are detected as Linux/RedGo.REAL!tr may have varying behaviour.
Below are some of its observed characteristics/behaviours:
- This malware is associated with the Realtek SDK outbreak which involves the CVE-2021-35394 vulnerability. The arbitrary command injection vulnerability and memory corruption vulnerabilities, found in the diagnostic tool of Realtek Jungle SDK version v2.x to v3.4.14B, allow for remote attackers to exploit the vulnerabilities and spread malicious payloads.
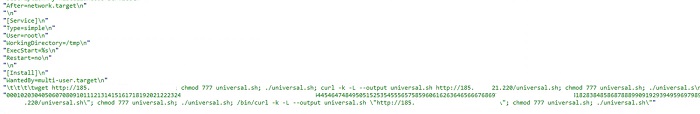
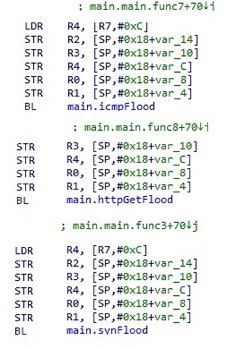
- Linux/RedGo.REAL!tr is a botnet. It will attempt to gain access to a victim's system and wait for commands from a control server. The malware will attempt to perform distributed denial-of-service(DDoS) attacks.
- The following are some IP's the botnet may attempt to connect to :
- 185.24.[removed].220
- This malware has been associated with the following third party article/advisory.
https://nvd.nist.gov/vuln/detail/CVE-2021-35394 https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2021-35394
|
|
- Md5: 75ade86d5cb702c76576c587c167c451
Sha256: 1967370203138b9324f11c5cb3fd15ac8d2f0c585373486614600b676a4e2641 - Md5: aaee43e63d5a3abd70ffa774a16c816e
Sha256: 26e96945ee32199536d4c85124a24c28e853b557eb31f3907d19f08b9798dff4 - Md5: c1492f719a4553bb4280b5a8c8c39095
Sha256: 81e581ed06515af959c8477442243f20baa77c0e54a1054542900936c6e81ff5 - Md5: cd56bea395c994290ebc71cc1482dfe0
Sha256: ab3de77616b4d85f032a226da6c3629de4a8f1c1b4d32674c1bed30afb9419e1 - Md5: fd1facf3a3fca0fd6108bbbe98f8d5fd
Sha256: 78b55d3f1b34f1154a28ce4fc855252bc3104a07944053facf6acce9195b2e77
 Outbreak Alert
Outbreak Alert
FortiGuard Labs continue to see Realtek SDK vulnerabilities being exploited in the wild with over 10,000+ average IPS detections per month to deploy and distribute Denial-of-service botnet malware such as new Hinata Botnet, RedGoBot, GooberBot and Marai based Botnet.
 Recommended Action
Recommended Action
- Make sure that your FortiGate/FortiClient system is using the latest AV database.
- Quarantine/delete files that are detected and replace infected files with clean backup copies.
 Telemetry
Telemetry
Detection Availability
| FortiGate | |
|---|---|
| FortiClient | |
| FortiAPS | |
| FortiAPU | |
| FortiMail | |
| FortiSandbox | |
| FortiWeb | |
| Web Application Firewall | |
| FortiIsolator | |
| FortiDeceptor | |
| FortiEDR |