PowerShell/NetWalker.B!tr.ransom
 Analysis
Analysis
PowerShell/NetWalker.B!tr.ransom is a generic detection for a ransomware trojan.
Since this is a generic detection, malware that are detected as PowerShell/NetWalker.B!tr.ransom may have varying behaviour.
Below are some of its observed characteristics/behaviours:
- This malware is a PowerShell script that is associated with the NetWalker ransomware family.
- This ransomware utilizes "vssadmin.exe" to delete all shadow copies to prevent system recovery.
- It will traverse through the victim's system, targeting files with a specific file extension to encrypt. Some files excluded from the encryption process include those with the file extension ".exe", ".dll", ".ini", ".msi" and ".pdf". The encrypted files will be appended with an extension consisting of 6 characters which will be referenced in the ransom note.
- Following the encryption process the malware will delete itself and a ransom note, with the name "[6CharacterExtension]-Readme.txt", will be dropped to the desktop and opened. A ransom note will also be dropped into every directory containing encrypted files. The note will instruct the victim to make contact with the attacker via a TOR site. Affected users are discouraged on taking this action as it does not guarantee the retrieval of data upon payment.
- Below are images of the result of executing the ransomware:
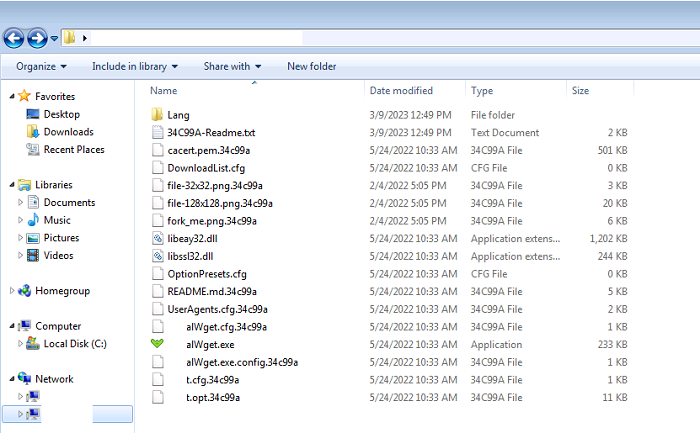
- Figure 1: Encrypted files
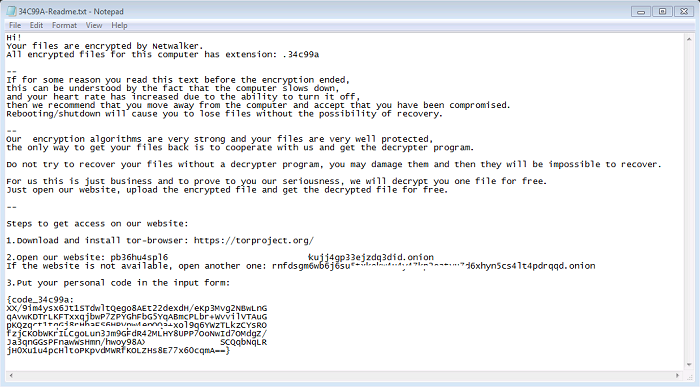
- Figure 2: Ransom note.
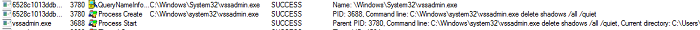
- Figure 3: Delete shadow copies.
- Below are some of the sites associated with the ransomware:
- pb36hu4spl[removed]kujj4gp33ejzdq3did.onion
- rnfdsgm6wb6j6su5txkekw[removed]n5cs4lt4pdrqqd.onion
- Following are some of the exact file hashes associated with this detection:
- Md5: 25c0fde038e01fe84fd3df69c99e60a1
Sha256: 129a0f0f4dd667e3ecbcc252b890f306eb041ad0295cb1511343c307c12a658d - Md5: 93f91bfcc1bf0c858fc7f3bd4536eba6
Sha256: 59ba11aa5b9a4d2ef80d260b9e51f605d556781b8ce682443ad1e547898eb0a6 - Md5: b49ea17739f484b2ccccf79f245186f3
Sha256: 7a456f306593a051bea004493f073bb54c5135d8ce3c428f2433c877afd858f3 - Md5: cb78a77e9ab26e4cf759e7d7b34bdbdc
Sha256: f2b96f7d6f1bfd464507790120d07bba46cb4c9856399335748f93ebd52b5696 - Md5: f8d08504911575dfb0642fbaafa07d9a
Sha256: 7613c54cb9be20699f177966f55be12ed7e66c3b3d293ea3d05b54f5c836d168
- Md5: 25c0fde038e01fe84fd3df69c99e60a1
 Recommended Action
Recommended Action
- Make sure that your FortiGate/FortiClient system is using the latest AV database.
- Quarantine/delete files that are detected and replace infected files with clean backup copies.
 Telemetry
Telemetry
Detection Availability
| FortiGate | |
|---|---|
| FortiClient | |
| FortiAPS | |
| FortiAPU | |
| FortiMail | |
| FortiSandbox | |
| FortiWeb | |
| Web Application Firewall | |
| FortiIsolator | |
| FortiDeceptor | |
| FortiEDR |