PowerShell/CoinMiner.WOARK!tr
 Analysis
Analysis
PowerShell/CoinMiner.WOARK!tr is a generic detection for a trojan.
Since this is a generic detection, malware that are detected as PowerShell/CoinMiner.WOARK!tr may have varying behaviour.
Below are some of its observed characteristics/behaviours:
- This malware is related to the CVE-2022-22954 vulnerability, affecting VMware Workspace ONE Access and Identity Manager.
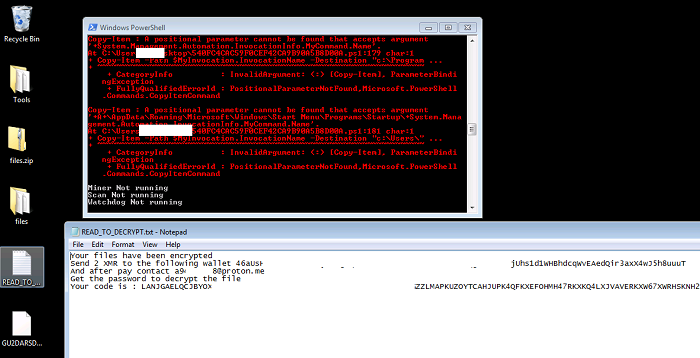
- This PowerShell script is an initialization script for the GuardMiner trojan and RAR1 ransomware.
- The script will download the following files from https://cloudflare-ipfs.com/ip[removed]5mc
and https://crustwebsites.net/ip[removed]5mc:
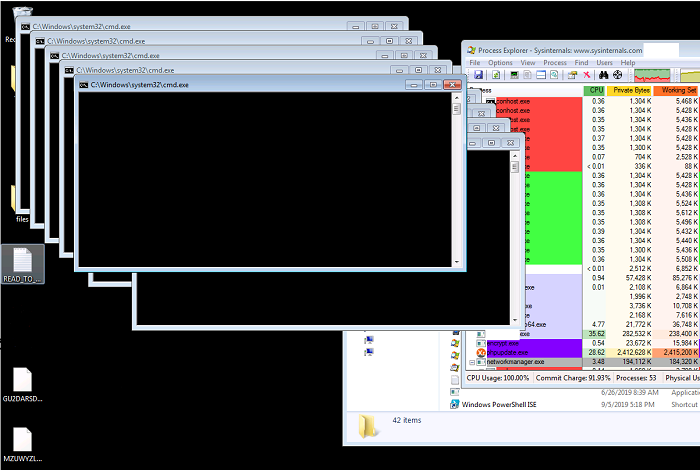
- phpupdate.exe : Xmrig Monero mining software
- config.json: Configuration file for mining pools
- networkmanager.exe: Executable used to scan and spread infection
- phpguard.exe: Executable used for guardian Xmrig miner to keep running
- init.sh: Copy of itself
- clean.bat: Script file to remove other cryptominers and processes
- encrypt.exe: RAR1 ransomware
- It will execute "encrypt.exe" and then proceed to start the GuardMiner attack.
- A scheduled task will be created to run every 30 minutes for persistence and "clean.bat" will be executed to stop any processes related to other cryptominers found on the compromised host.
- This malware has been associated with the following third party article/advisory.
https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2022-22954
|
|
- https://cloudflare-ipfs.com/ip[removed]pdate
- https://crustwebsites.net/ip[removed]pupdate
- https://cloudflare-ipfs.com/ip[removed]5mc/init.sh
- https://crustwebsites.net/ipn[removed]mc/init.sh
- https://cloudflare-ipfs.com/ip[removed]config.json
- https://crustwebsites.net/ipn[removed]mc/config.json
- https://cloudflare-ipfs.com/i[removed]5mc/networkmanager
- https://crustwebsites.net/ip[removed]5mc/networkmanager
- https://cloudflare-ipfs.com/ipn[removed]mc/phpguard
- https://crustwebsites.net/ip[removed]5mc/phpguard
- https://cloudflare-ipfs.com/ipn[removed]5mc/clean.bat
- https://crustwebsites.net/ip[removed]clean.bat
- https://cloudflare-ipfs.com/ip[removed]encrypt.exe
- https://crustwebsites.net/ipn[removed]encrypt.exe
- Md5: 540fc4cac59f0cef42ca9b90a5b8d00a
Sha256: 9c00823295f393358762542418bb767b44cfe285c4ab33e7e57902c6e1c2dacb - Md5: 2d282c09fdb9df557fccb21f8e915622
Sha256: 4b4c0d3cb708612b1fdb0394e029e507e4c0f6136fc44e415200694624ed5b68 - Md5: 4d1ee42106b6c9158be11af06df3bd3b
Sha256: 7fc7c242ad1fa439e515725561a9e304b3d94e40ba91f61df77471a4c2ff2b39 - Md5: 8c03343112c1372e68da4c08032b292a
Sha256: f2a6827ea5f60cefc2f6528269b2d1557a7cc1e68f84edca4029e819dd0509cb - Md5: 00f1119f4f108c12fc63dbbf64e3cc41
Sha256: 66db83136c463441ea56fb1b5901c505bcd1ed52a73e23d7298f7055db2108d1 - Md5: d01e11f0f95fff6f9175d1a7f4e445fa
Sha256: 4761e5d9bd3ebe647fbd7840b7d2d9c1334bde63d5f6b05a4ed89af7aa3a6eab
 Recommended Action
Recommended Action
- Make sure that your FortiGate/FortiClient system is using the latest AV database.
- Quarantine/delete files that are detected and replace infected files with clean backup copies.
 Telemetry
Telemetry
Detection Availability
| FortiGate | |
|---|---|
| FortiClient | |
| FortiAPS | |
| FortiAPU | |
| FortiMail | |
| FortiSandbox | |
| FortiWeb | |
| Web Application Firewall | |
| FortiIsolator | |
| FortiDeceptor | |
| FortiEDR |
Version Updates
| Date | Version | Detail |
|---|---|---|
| 2022-11-09 | 90.07683 |