ELF/CoinMiner.F7AE!tr
 Analysis
Analysis
ELF/CoinMiner.F7AE!tr is a detection for an ELF Coinmining trojan.
Below are some of its observed characteristics/behaviours:
- This malware was observed to issue the following commands as probably part of its coinmining:
- grep -q "0.0.0.0 p[Removed].cpuminerpool.com" /etc/hosts
- grep -q "0.0.0.0 systemte[Removed].org" /etc/hosts
- grep -q "0.0.0.0 pastebi[Removed].com" /etc/hosts
- grep -q "0.0.0.0 lsd.systemte[Removed].org" /etc/hosts
- grep -q "0.0.0.0 aliyu[Removed].one" /etc/hosts
- It also attempts to connect/download from the following URLs/IPs:
- [Removed].141.38.247
- [Removed].251.59.65
- [Removed].141.38.114
- [Removed].178.208.150
- [Removed].100.85.150
- [Removed].162.228.156
- [Removed].212.249.177
- [Removed].251.89.65
- [Removed].229.33.40
- [Removed].56.101.79
- tencentjy5kpcc[Removed].civiclink.network/cpu
- tencentjy5kpcc[Removed].tor2web.to/cpu
- tencentjy5kpcc[Removed].tor2web.io/cpu
- tencentjy5kpcc[Removed].tor2web.su/cpu
- tencentjy5kpcc[Removed].onion.in.net/cpu
- tencentjy5kpcc[Removed].onion.pet/cpu
- tencentjy5kpcc[Removed].onion.to/cpu
- tencentjy5kpcc[Removed].onion.glass/cpu
- tencentjy5kpcc[Removed].onion.ws/cpu
- tencentjy5kpcc[Removed].civiclink.network/cmd
- tencentjy5kpcc[Removed].tor2web.to/cmd
- tencentjy5kpcc[Removed].tor2web.io/cmd
- tencentjy5kpcc[Removed].tor2web.su/cmd
- tencentjy5kpcc[Removed].onion.in.net/cmd
- tencentjy5kpcc[Removed].onion.pet/cmd
- tencentjy5kpcc[Removed].onion.to/cmd
- tencentjy5kpcc[Removed].onion.glass/cmd
- tencentjy5kpcc[Removed].onion.ws/cmd
- tencentxjy5kpcc[Removed].d2web.org
- tencentxjy5kpcc[Removed].onion.mn
- tencentxjy5kpcc[Removed].4tor.ml
- tencentxjy5kpcc[Removed].onion.ly
- It drops/creates a bash script as ~/.qcloud-stargate-admin-start.sh and attempts to place it under crontab for resiliency:
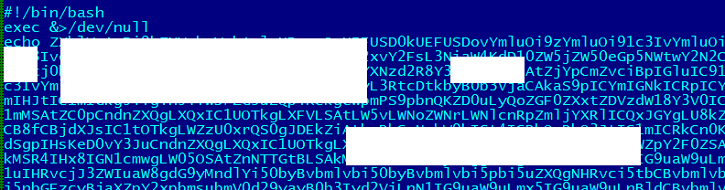
- Figure 1: B64 Shell Script.
- This malware has been associated with the exploit CVE-2016-3088 Apache ActiveMQ Exploit.
 Recommended Action
Recommended Action
- Make sure that your FortiGate/FortiClient system is using the latest AV database.
- Quarantine/delete files that are detected and replace infected files with clean backup copies.
 Telemetry
Telemetry
Detection Availability
| FortiClient | |
|---|---|
| Extreme | |
| FortiMail | |
| Extreme | |
| FortiSandbox | |
| Extreme | |
| FortiWeb | |
| Extreme | |
| Web Application Firewall | |
| Extreme | |
| FortiIsolator | |
| Extreme | |
| FortiDeceptor | |
| Extreme | |
| FortiEDR |