MSIL/HiddenTear.01B1!tr.ransom
 Analysis
Analysis
MSIL/HiddenTear.01B1!tr.ransom is a generic detection for a Ransomware HiddenTear trojan.
Since this is a generic detection, this malware may have varying behaviour.
Below are some of its observed characteristics/behaviours:
- This malware may drop any of the following file(s):
- %Desktop%\READ_IT.txt : This text file will serve as ransom note.
- %Username%\ransom.jpg : This file is a picture/image and will serve as ransom notes. This picture is downloaded from the URL hxxp://i.imgur.com/xZuL{Removed}.jpg
- %Username%\Rand123\local.exe : This file is the copy of the original malware itself.
- This Ransomware encrypts the following file extensions:
- .jar
- .exe
- .dat
- .contact
- .settings
- .doc
- .xls
- .docx
- .xlsx
- .ppt
- .pptx
- .odt
- .jpg
- .png
- .csv
- .py
- .sql
- .mdb
- .sln
- .php
- .asp
- .aspx
- .html
- .htm
- .xml
- .psd
- .dll
- .c
- .cs
- .mp3
- .mp4
- .f3d
- .dwg
- .cpp
- .zip
- .rar
- .mov
- .rtf
- .bmp
- .mkv
- .avi
- .apk
- .lnk
- .iso
- .7-zip
- .ace
- .arj
- .bz2
- .cab
- .gzip
- .lzh
- .tar
- .uue
- .xz
- .z
- .001
- .mpeg
- .mp3
- .mpg
- .core
- .crproj
- .pdb
- .ico
- .pas
- .db
- .torrent
- .txt
- This Ransomware encrypts the files from following folders:
- Desktop
- Links
- Contacts
- Desktop
- Documents
- Downloads
- Pictures
- Music
- OneDrive
- Saved Games
- Favorites
- Searches
- Videos
- This Ransomware has its own decrypter. It connects to URL hxxp://www.iptvb{Removed}.net/Panel/write.php to verify the password or key entered by the infected user to decrypt files.
- This Ransomware also changes desktop background to ransom notes using %Username%\ransom.jpg .
- Affected files of this Ransomware will use the filenaming format {OriginalFilename.Ext}.locked.
- Affected victims of this Ransomware are redirected by the attacker via:
- KyMERA-Gian@outlook.com
- Below is an illustration of the malware's Ransom notes:

- Figure 1:Ransom note .
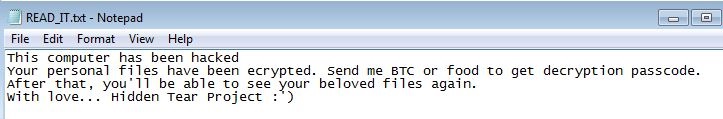
- Figure 2: Ransom note .
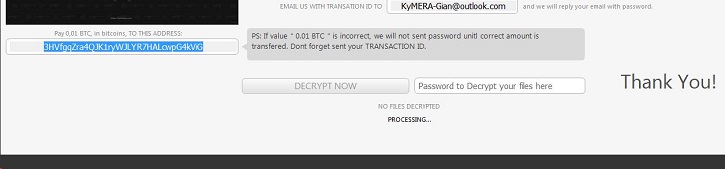
- Figure 3: Ransom note .
 Recommended Action
Recommended Action
- Make sure that your FortiGate/FortiClient system is using the latest AV database.
- Quarantine/delete files that are detected and replace infected files with clean backup copies.
 Telemetry
Telemetry
Detection Availability
| FortiGate | |
|---|---|
| Extended | |
| FortiClient | |
| Extreme | |
| FortiAPS | |
| FortiAPU | |
| FortiMail | |
| Extreme | |
| FortiSandbox | |
| Extreme | |
| FortiWeb | |
| Extreme | |
| Web Application Firewall | |
| Extreme | |
| FortiIsolator | |
| Extreme | |
| FortiDeceptor | |
| Extreme | |
| FortiEDR |