W32/Filecoder_Rapid.A!tr.ransom
 Analysis
Analysis
W32/Filecoder_Rapid.A!tr.ransom is a generic detection for the Rapid Ransomware trojan.
Since this is a generic detection, this malware may have varying behaviour.
Below are some of its observed characteristics/behaviours:
- This malware may drop any of the following file(s):
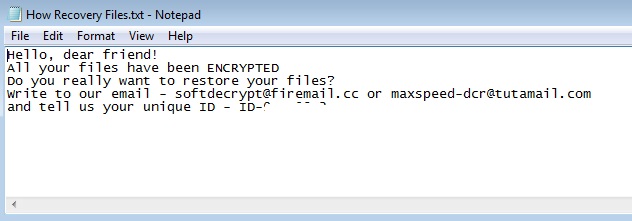
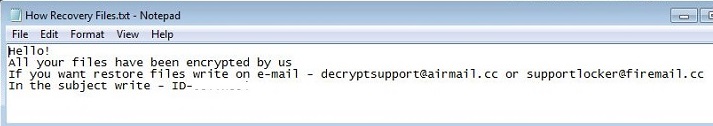
- How Recovery Files.txt : This file is dropped in every infected folder. It will serve as ransom note.
- %Appdata%\recovery.txt : This file is the copy of file "How Recovery Files.txt".It will serve as ransom note when the user logs in to the system.
- %Appdata%\info.exe. : This file is a copy of the malware itself.
- Affected files of this Ransomware will use the following filenaming format:
- {original name}.no_more_ransom
- {original name}.rapid
- HKCU\Software\Microsoft\Windows\Currentversion\Run
- Encrypter_074 = %Appdata%\info.exe
- HKCU\Software\Microsoft\Windows\Currentversion\Run
- userinfo = %Appdata%\recovery.txt
- softdecrypt@firemail.cc
- maxspeed-dcr@tutamail.com
- decryptsupport@airmail.cc
- supportlocker@firemail.cc
- help.ransom@protonmail
- rapid.file@tuta.io
- To delete the shadow volume copies so that the user cannot restore them.
- Delete the system backups in other forms.
- Sets the system up to ignore failures on future boots and disable an automatic repair effort.
|
|
 Recommended Action
Recommended Action
- Make sure that your FortiGate/FortiClient system is using the latest AV database.
- Quarantine/delete files that are detected and replace infected files with clean backup copies.
 Telemetry
Telemetry
Detection Availability
| FortiClient | |
|---|---|
| Extreme | |
| FortiMail | |
| Extreme | |
| FortiSandbox | |
| Extreme | |
| FortiWeb | |
| Extreme | |
| Web Application Firewall | |
| Extreme | |
| FortiIsolator | |
| Extreme | |
| FortiDeceptor | |
| Extreme | |
| FortiEDR |
Version Updates
| Date | Version | Detail |
|---|---|---|
| 2022-05-25 | 90.02622 | |
| 2022-05-24 | 90.02591 | |
| 2021-07-27 | 87.00933 | |
| 2020-09-01 | 80.05600 | Sig Updated |
| 2020-06-03 | 77.89800 | Sig Updated |
| 2018-12-27 | 65.21000 | Sig Updated |
| 2018-12-11 | 64.82100 | Sig Updated |
| 2018-11-28 | 64.51700 | Sig Updated |
| 2018-10-23 | 63.14400 | Sig Updated |
| 2018-10-10 | 62.83000 | Sig Updated |