W32/Crysis.EE29!tr.ransom
 Analysis
Analysis
W32/Crysis.EE29!tr.ransom is a generic detection for the Crysis Ransomware trojan. Since this is a generic detection, this malware may have varying behaviour.
Below are some of its observed characteristics/behaviours:
- This malware may drop any of the following file(s):
- FILES ENCRYPTED.txt : This file is dropped all over the affected hosts drive and will serve as ransom notes.
- Start Menu\Programs\Startup\Info.hta : This file is an html page and will serve as ransom notes.
- %Appdata%\Roaming\Info.hta : This file is an html page and will serve as ransom notes.
- C:\\Data.hta : Phobos variant of this ransomware drops this file and it will serve as ransom note. It is similar to Info.hta.
- %Desktop%\[Email_Address].exe: Phobos variant of this ransomware drops this file. This file is currently detected as W32/Kryptik.GOLH!tr .
- %StartUp%\[OriginalMalware].exe : This file is a copy of the original malware itself.
- %common_startup%\[OriginalMalware].exe : This file is a copy of the original malware itself.
- %Appdata%\Roaming\[OriginalMalware].exe : This file is a copy of the original malware itself.
- %SystemRoot%\system32\[OriginalMalware].exe : This file is a copy of the original malware itself with same file name.
- %Appdata%\Roaming\regsvcs.exe : This file is usually dropped when .NET versions of the malware has been used by the attacker, and this is legitimate software program that belongs to software Microsoft .Net Framework.
- %SystemRoot%\system32\regsvcs.exe : This file is usually dropped when .NET versions of the malware has been used by the attacker, and this file is legitimate software program that belongs to software Microsoft .Net Framework.
- %StartUp%\regsvcs.exe : This file is usually dropped when .NET versions of the malware has been used by the attacker, and this file is legitimate software program that belongs to software Microsoft .Net Framework.
- %common_startup%\regsvcs.exe : This file is usually dropped when .NET versions of the malware has been used by the attacker, and this file is legitimate software program that belongs to software Microsoft .Net Framework.
- %StartUp%\vbc.exe: This file is usually dropped when .NET versions of the malware has been used by the attacker, and this file is legitimate software program that belongs to Microsoft Visual Studio 2005.
- %Appdata%\Roaming\vbc.exe: This file is usually dropped when .NET versions of the malware has been used by the attacker, and this file is legitimate software program that belongs to Microsoft Visual Studio 2005.
- %SystemRoot%\system32\vbc.exe: This file is usually dropped when .NET versions of the malware has been used by the attacker, and this file is legitimate software program that belongs to Microsoft Visual Studio 2005.
- Affected files of this Ransomware will use the filenaming format {original name}.id-{id}.[email_address].{extensions}, here id represents the identifier having eight alphanumeric characters.
- Below are some of email address examples:
- buydecrypt@qq.com
- decryptdata@qq.com
- bitpandacom@qq.com
- backdata@qq.com
- tocktock@qq.com
- broodmother@cock.li
- backtonormal@foxmail.com
- symabkp@protonmail.com
- decrypt@fros.cc
- GetDataBack@fros.cc
- koklok@protonmail.com
- stopencrypt@qq.com
- backtonormal@foxmail.com
- getdataback@fros.cc
- techdataback@india.com
- fordecrypt72hours@qq.com
- payransom@qq.com
- admin@decryption.biz
- malibumood@tutanota.com
- cryptoblazer@asia.com
- syndicateXXX@aol.com
- back@decryption.biz
- veracrypt@foxmail.com
- annihilation1@foxmail.com
- relvirosa1981@aol.com
- mfdoom@420blaze.it
- silver@decryption.biz
- fittanatos@cock.li
- pro_100@aol.com
- raphaeldupon@aol.com
- bestdecoding@cock.li
- dta@cock.li
- despicableme@keemail.me
- writehere@qq.com
- ncaracemco1987@aol.com
- lebeciouded1975@aol.com
- sebekgrime@tutanota.com
- help32decrypt@qq.com
- datadecrypt@qq.com
- hydrasynth@tutanota.com
- hydrasynth@cock.li
- writehere@qq.com
- lordoftheweed@420blaze.it
- btc@decoding.biz
- Below are some of the file extension names this Ransomware may use:
- .dharma
- .wallet
- .onion
- .arena
- .cobra
- .java
- .arrow
- .bip
- .cmb
- .brr
- .gamma
- .bkp
- .monro
- .boost
- .adobe
- .tron
- .AUDIT
- .cccmn
- .BEAR
- .Back
- .phobos
- .btc
- .best
- .aye
- .ETH
- .AYE
- It assign a unique alphanumeric code(Base64) to identify each infection.
- This malware was also observed to encrypt files located on shared drives within the same subnet.
- This malware attempts to delete Shadow Volume Copies so that the user cannot restore them.
- The attacker indicates a payment site as listed below:
- hxxps://localbitcoins[.]com/buy_bitcoins
- Affected victims of this Ransomware are redirected by the attacker via:
- techdataback@india.com
- datafilesbtc@tuta.io
- vacuum_0@aol.com
- This malware may apply any of the following registry modification(s):
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\Currentversion\Run
- [OriginalMalware].exe = %SystemRoot%\system32\[OriginalMalware].exe or %Appdata%\Roaming\[OriginalMalware].exe
- Regsvcs.exe = %SystemRoot%\system32\regsvcs.exe or %Appdata%\Roaming\regsvcs.exe
- vbc.exe = %SystemRoot%\system32\vbc.exe or %Appdata%\Roaming\vbc.exe
- HKEY_CURRENT_USER\Software\Microsoft\Windows\Currentversion\Run
- [OriginalMalware].exe = system32\[OriginalMalware].exe or %Appdata%\Roaming\[OriginalMalware].exe
- %Appdata%\Roaming\Info.hta = mshta.exe "Appdata%\Roaming\Info.hta"
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\Currentversion\Run
- After encrypting all the files, it drops the file "FILES ENCRYPTED.Txt". Below is the illustation of such file:
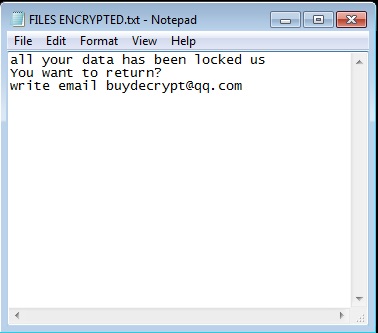
- Figure 1: Ransom notes.
- Below is the illustration of the message it displays on the screen after encrypting files.
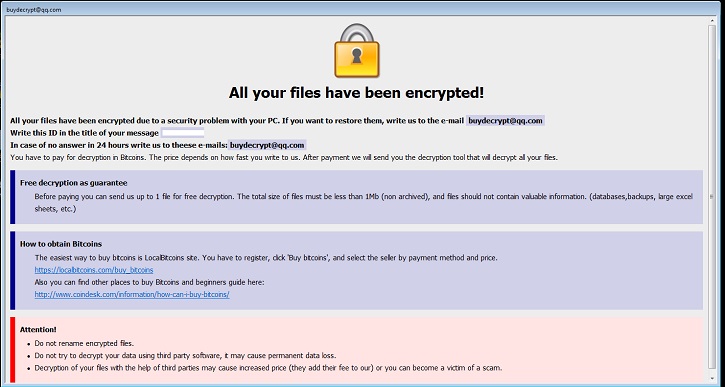
- Figure 2: Ransom notes.
- Below are some of email address examples:
 Recommended Action
Recommended Action
- Make sure that your FortiGate/FortiClient system is using the latest AV database.
- Quarantine/delete files that are detected and replace infected files with clean backup copies.
 Telemetry
Telemetry
Detection Availability
| FortiGate | |
|---|---|
| FortiClient | |
| FortiAPS | |
| FortiAPU | |
| FortiMail | |
| FortiSandbox | |
| FortiWeb | |
| Web Application Firewall | |
| FortiIsolator | |
| FortiDeceptor | |
| FortiEDR |
Version Updates
| Date | Version | Detail |
|---|---|---|
| 2022-05-25 | 90.02622 | |
| 2021-07-27 | 87.00933 | |
| 2020-01-06 | 74.33900 | Sig Updated |
| 2019-10-15 | 72.34800 | Sig Updated |
| 2019-10-01 | 72.01200 | Sig Updated |
| 2019-09-10 | 71.50800 | Sig Updated |
| 2019-09-05 | 71.39200 | Sig Updated |
| 2019-08-20 | 71.01900 | Sig Updated |
| 2019-08-06 | 70.52400 | Sig Updated |
| 2019-07-30 | 70.35800 | Sig Updated |