W32/GandCrypt.FOD!tr.ransom
 Analysis
Analysis
W32/GandCrypt.FOD!tr.ransom is a detection for a Ransomware GANDCRAB trojan.
Below are some of its observed characteristics/behaviours:
- This malware may drop any of the following file(s):
- XXXXX-DECRYPT.txt : This file is txt file and will serve as ransom notes, where X is alphanumeric character.
- Affected files of this Ransomware will use the filenaming format {original name}.xxxxx, where X is alphanumeric character.
- This malware was also observed to affect/encrypt files located on shared drived within the same subnet.
- This Ransomware also changes desktop background to ransom notes.
- This malware may connect to any of the following remote sites(s):
- hxxp://www.billeri{Removed}.com
- hxxp://www.macarte{Removed}.eu
- hxxp://www.poke{Removed}.com
- hxxp://perova{Removed}.ru
- hxxp://asl-{Removed}.ru
- hxxp://www.fabb{Removed}.gm
- hxxp://www.perfectfunnel{Removed}.com
- hxxp://www.wash-{Removed}.com
- hxxp://al{Removed}.be
- hxxp://ce{Removed}.net
- hxxp://www.n2{Removed}.co.th
- hxxp://www.rm{Removed}.in
- hxxp://boatshow{Removed}.com
- hxxp://dna-{Removed}.com
- hxxp://ac{Removed}.fr
- Below are sample illustrations of prompts when potential infected document are opened:
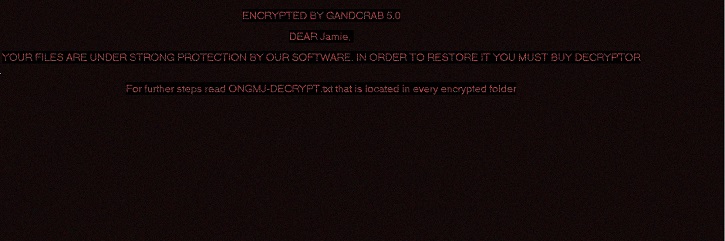
- Figure 1: Ransom notes.

- Figure 2: Ransom notes.
 Recommended Action
Recommended Action
- Make sure that your FortiGate/FortiClient system is using the latest AV database.
- Quarantine/delete files that are detected and replace infected files with clean backup copies.
 Telemetry
Telemetry
Detection Availability
| FortiClient | |
|---|---|
| Extreme | |
| FortiMail | |
| Extreme | |
| FortiSandbox | |
| Extreme | |
| FortiWeb | |
| Extreme | |
| Web Application Firewall | |
| Extreme | |
| FortiIsolator | |
| Extreme | |
| FortiDeceptor | |
| Extreme | |
| FortiEDR |
Version Updates
| Date | Version | Detail |
|---|---|---|
| 2018-10-03 | 62.66000 | Sig Updated |