AutoIt/Ouroboros.A!tr.ransom
 Analysis
Analysis
AutoIt/Ouroboros.A!tr.ransom is a detection for a Ransomware Ouroboros trojan.
Since this is a generic detection, this malware may have varying behaviour.
Below are some of its observed characteristics/behaviours:
- This malware may drop any of the following file(s):
- %Desktop%\README!!! ALL YOUR FILES HAVE BEEN SECURELY ENCRYPTED!!!.txt : This text file will serve as ransom note.
- %StartUp%\setup.exe : This file is the copy of the original malware itself.
- %CommonProgramFiles%\log.txt : This text file contains the list of the encrypted files.
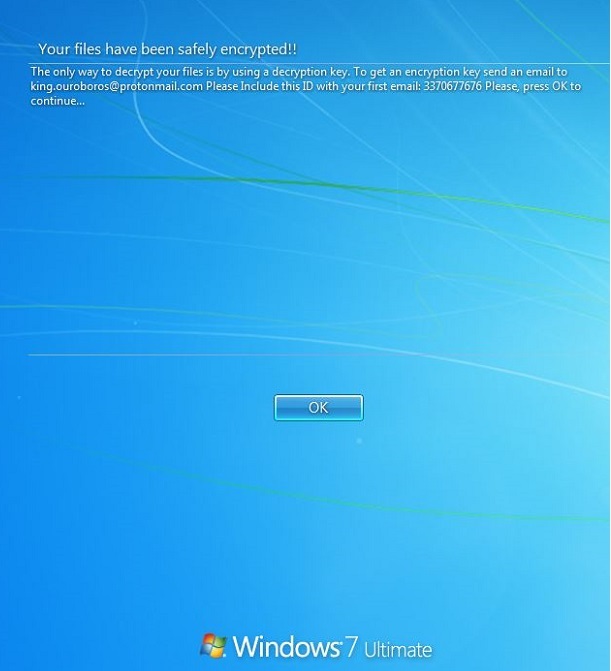
- %CommonProgramFiles%\wallpaper.jpg : This JPEG file will serve as ransom note.
- %CommonProgramFiles%\{Originalmalware}.exe : This file is the copy of the original malware itself.
- This Ransomware also changes desktop background to ransom notes using %CommonProgramFiles%\wallpaper.jpg .
- Affected files of this Ransomware will use the filenaming format {OriginalFilename}.king_ouroboros.{OriginalExt} .
- Affected victims of this Ransomware are redirected by the attacker via:
- king.ouroboros@protonmail.com
- a@savemyfile.pw
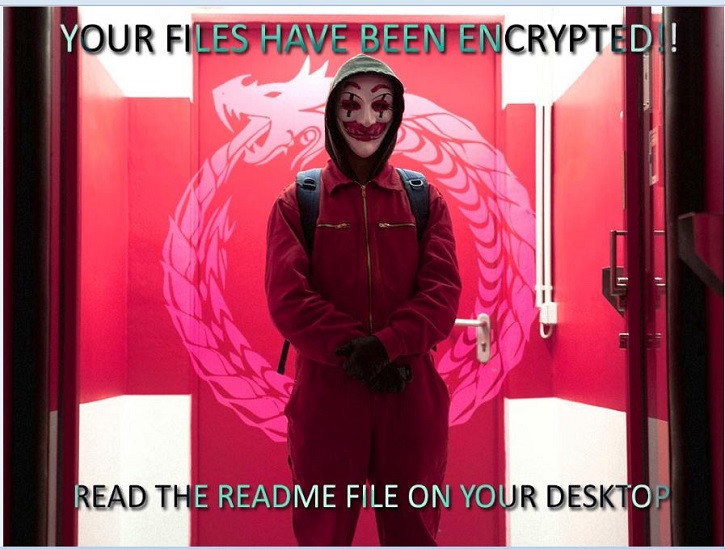
- After encrypting the files, it reboots the infected system and displays the ransom note as shown in figure 3.
- This Ransomware may apply the following operations:
- Delete the shadow volume copies so that the user cannot restore them.
- Sets the system up to ignore failures on future boots and disable an automatic repair effort.
- This Ransomware may connect to following remote sites:
- HXXPS://5VLBLODOCT6HO26SWNMXMEMIAB{Removed}.PW/ROBOTS.TXT
- HXXPS://ORANGEPR{Removed}.PW/KIM/USR.PHP
- This Ransomware encrypts the files with following extensions:
- ZIP
- 7Z
- RAR
- DOC
- DOCX
- XLS
- XLSX
- PPTX
- PUB
- ONE
- VSDX
- ACCDB
- ASD
- XLSB
- MDB
- SNP
- WBK
- PPT
- PSD
- AI
- ODT
- ODS
- ODP
- ODM
- ODC
- ODB
- DOCM
- WPS
- XLSM
- XLK
- PPTM
- PST
- DWG
- DXF
- DXG
- WPD
- RTF
- WB2
- MDF
- DBF
- PDD
- EPS
- INDD
- CDR
- DNG
- 3FR
- ARW
- SRF
- SR2
- BAY
- CRW
- CR2
- DCR
- KDC
- ERF
- MEF
- MRW
- NEF
- NRW
- ORF
- RAF
- RAW
- RWL
- RW2
- P7B
- P7C
- ABW
- TIL
- AIF
- ARC
- AS
- ASC
- ASF
- ASHDISC
- ASM
- ASP
- ASPX
- ASX
- AUP
- AVI
- BBB
- BDB
- BIBTEX
- BKF
- BMP
- BPN
- BTD
- BZ2
- C
- CDI
- HIMMEL
- CERT
- CFM
- CGI
- CPIO
- CPP
- CSR
- CUE
- DDS
- DEM
- DMG
- DSB
- EDDX
- EDOC
- EML
- EMLX
- EPS
- EPUB
- FDF
- FFU
- FLV
- GAM
- GCODE
- GHO
- GPX
- GZ
- H
- HBK
- HDD
- HDS
- HPP
- ICS
- IDML
- IFF
- IMG
- IPD
- ISO
- ISZ
- IWA
- J2K
- JP2
- JPF P7B
- P7C
- ABW
- TIL
- AIF
- ARC
- AS
- ASC
- ASF
- ASHDISC
- ASM
- ASP
- ASPX
- ASX
- AUP
- AVI
- BBB
- BDB
- BIBTEX
- BKF
- BMP
- BPN
- BTD
- BZ2
- C
- CDI
- HIMMEL
- CERT
- CFM
- CGI
- CPIO
- CPP
- CSR
- CUE
- DDS
- DEM
- DMG
- DSB
- EDDX
- EDOC
- EML
- EMLX
- EPS
- EPUB
- FDF
- FFU
- FLV
- GAM
- GCODE
- GHO
- GPX
- GZ
- H
- HBK
- HDD
- HDS
- HPP
- ICS
- IDML
- IFF
- IMG
- IPD
- ISO
- ISZ
- IWA
- J2K
- JP2
- JPF
- R3D
- PTX
- PEF
- SRW
- X3F
- DER
- CER
- CRT
- PEM
- PFX
- P12
- JPM
- JPX
- JSP
- JSPA
- JSPX
- JST
- KEY
- KEYNOTE
- KML
- KMZ
- LIC
- LWP
- LZMA
- M3U
- M4A
- M4V
- MAX
- MBOX
- MD2
- MDBACKUP
- MDDATA
- MDINFO
- MDS
- MID
- MOV
- MP3
- MP4
- MPA
- MPB
- MPEG
- MPG
- MPJ
- MPP
- MSG
- MSO
- NBA
- NBF
- NBI
- NBU
- NBZ
- NCO
- NES
- NOTE
- NRG
- NRI
- AFSNIT
- OGG
- OVA
- OVF
- OXPS
- P2I
- P65
- P7
- PAGES
- PCT
- PEM
- PHTM
- PHTML
- PHP
- PHP3
- PHP4
- PHP5
- PHPS
- PHPX
- PHPXX
- PL
- PLIST
- PMD
- PMX
- PPDF
- PPS
- PPSM
- PPSX
- PS
- PSD
- PSPIMAGE
- PVM
- QCN
- QCOW
- QCOW2
- QT
- RA
- RM
- RTF
- S
- SBF
- SET
- SKB
- SLF
- SME
- SMM
- SPB
- SQL
- SRT
- SSC
- SSI
- STG
- STL
- SVG
- SWF
- SXW
- SYNCDB
- TAGER
- TC
- TEX
- TGA
- THM
- TIF
- TIFF
- TOAST
- TORRENT
- TXT
- VBK
- AU3
- VCARD
- VCD
- VCF
- VDI
- XML
- TIB
- METADATA
- VFS4
- VHD
- VHDX
- VMDK
- VOB
- WBVERIFY
- WAV
- WEBM
- WMB
- WPB
- WPS
- XDW
- XLR
- XLSX
- XZ
- YUV
- ZIPX
- JPG
- JPEG
- PNG
- BMP
- INDL
- INDT
- INDB
- INX
- XQX
- ICML
- OBJ
- SCAD
- OFF
- AMF
- CSG
- HTACCESS
- TAR
- PGP
- CMD
- BAT
- RLE
- DIB
- MOS
- CIN
- DPX
- RLA
- RPF
- EI
- JPE
- MA
- EXR
- PCX
- XYZE
- RGBE
- HDR
- SGI
- BW
- RGB
- PIC
- VDA
- ICB
- VST
- AEP
- AET
- AAF
- AEPX
- PRPROJ
- Below is an illustration of the malware's Ransom notes:
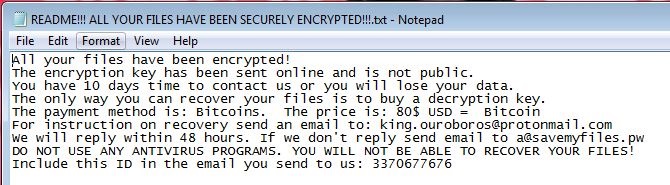
- Figure 1: Ransom note .
- Figure 2:Ransom note .
- Figure 3:Ransom note .
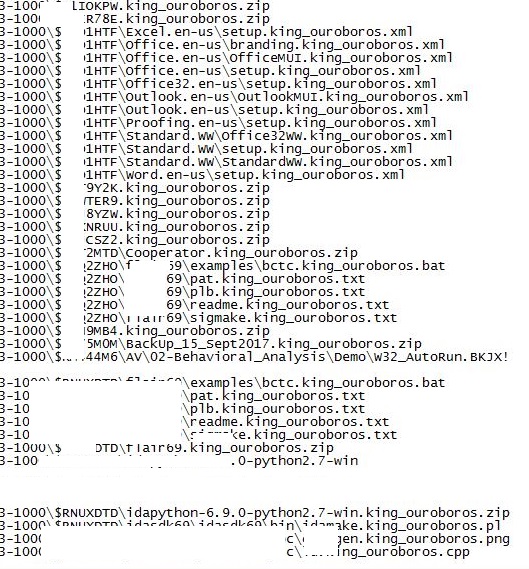
- Figure 4: list of encrypted files.
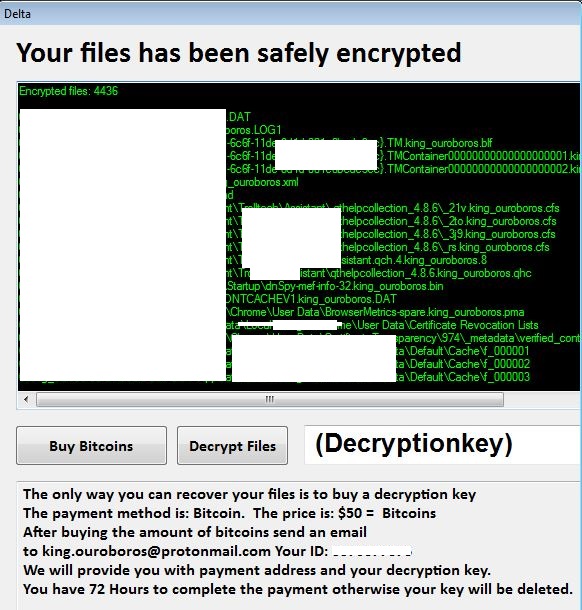
- Figure 5: Ransom note.
 Recommended Action
Recommended Action
- Make sure that your FortiGate/FortiClient system is using the latest AV database.
- Quarantine/delete files that are detected and replace infected files with clean backup copies.
 Telemetry
Telemetry
Detection Availability
| FortiClient | |
|---|---|
| Extreme | |
| FortiMail | |
| Extreme | |
| FortiSandbox | |
| Extreme | |
| FortiWeb | |
| Extreme | |
| Web Application Firewall | |
| Extreme | |
| FortiIsolator | |
| Extreme | |
| FortiDeceptor | |
| Extreme | |
| FortiEDR |