W32/Injector.DZGI!tr
 Analysis
Analysis
W32/Injector.DZGI!tr is a generic detection for a trojan. Since this is a generic detection, malware that are detected as W32/Injector.DZGI!tr may have varying behaviour.
Below are some of its observed characteristics/behaviours:
- This malware may:
- provide remote access to the infected computer, including keylogging and botnet functionality.
- steal files and computer information.
- mine cryptocurrency.
- disable anti-virus features of Windows Defender.
- download other malware.
- The screenshot below shows an example of stolen data:
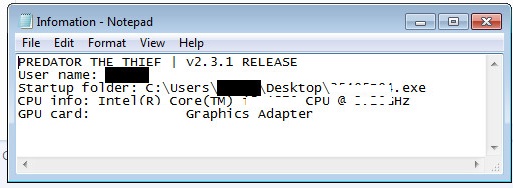
- This malware may drop any of the following file(s):
- %Temp%\flashplayer.exe: This is a copy of the malware.
- %ProgramFiles%\DPI Host\dpihost.exe: This is a copy of the malware.
- %AppData%\{random}\TCP Host\tcphost.exe: This is a copy of the malware.
- %AppData%\WindowsUpdate.exe: This is a copy of the malware.
- %AppData%\expllor\explor.exe: This is a copy of the malware.
- %AppData%\419EFC\C057BF.exe: This is a copy of the malware.
- %Temp%\{4 letters and numbers}.tmp.zip: This file may be detected as W32/Injector.DZGI!tr W32/Miner.DV!tr.
- %AppData%\Microsoft\explorer.exe: This file may be detected as W32/Injector.DZGI!tr or W32/Miner.DV!tr.
- %AppData%\Microsoft\manager.exe: This file may be detected as W32/Injector.DZGI!tr or Riskware/OxyPumper.
- %Startup%\explorer.exe.vbs: This file will serve as an autostart for the malware itself.
- %Startup%\expllor.vbs: This file will serve as an autostart for the malware itself.
- %Startup%\mt103 transfer details.vbs: This file will serve as an autostart for the malware itself.
- %AppData%\{random}\Logs\{username}\KB_{numbers}.dat: This file is used for logging the activities of the infected user.
- %Temp%\{random}.bat : This Batch file deletes the original malware itself, detected as BAT/Small.NAN!tr.
- This malware may delete itself after executing.
- This malware may connect to any of the following websites:
- hxxp://t22{removed}.beget.tech/api/gate.get?p1=0&p2=0&p3=0&p4=0&p5=0&p6=0&p7=0
- hxxp://sqi{removed}.ga/jboy/pony/shit.exe
- hxxp://pes{removed}.net/sql/Panel/five/fre.php
- zpr{removed}.online: This domain is used for cryptocurrency mining.
- xmr{removed}.nanopool.org: This domain is used for cryptocurrency mining.
- nan{removed}.ddns.net
- lon{removed}.ddns.net
- www.pro{removed}.com
- www.765{removed}.info
- www.the{removed}.online
- www.e-in{removed}.com
- www.nez{removed}.net
- www.fra{removed}.ltd
- {removed}.101.152.199
- 3{removed}.235.1.174
- 1{removed}.63.2.227: This IP address is associated with the Fareit botnet.
- 3{removed}.186.8.89: This IP address is associated with the Loki botnet.
- This malware may apply any of the following registry modification(s):
- HKEY_CURRENT_USER\Software\Microsoft\Windows\Currentversion\Run
- DPI Host = %ProgramFiles%\DPI Host\dpihost.exe
- TCP Host = %AppData%\{random}\TCP Host\tcphost.exe
- Windows Update = %AppData%\WindowsUpdate.exe
- HKEY_CURRENT_USER\Software\Microsoft\Windows\Currentversion\Run
- This malware may schedule a Windows Task to execute itself.
 Recommended Action
Recommended Action
- Make sure that your FortiGate/FortiClient system is using the latest AV database.
- Quarantine/delete files that are detected and replace infected files with clean backup copies.
 Telemetry
Telemetry
Detection Availability
| FortiGate | |
|---|---|
| Extended | |
| FortiClient | |
| FortiMail | |
| FortiSandbox | |
| FortiWeb | |
| Web Application Firewall | |
| FortiIsolator | |
| FortiDeceptor | |
| FortiEDR |