W32/GenKryptik.BXUS!tr
 Analysis
Analysis
W32/GenKryptik.BXUS!tr is a generic detection for a Injector/Botnet trojan.
Since this is a generic detection, malware that are detected as W32/GenKryptik.BXUS!tr may have varying behaviour.
Below are some of its observed characteristics/behaviours:
- This malware may drop any of the following file(s):
- %AppData%\[Random]\[Random].exe : This file is detected as W32/GenKryptik.BXUS!tr.
- %AppData%\[Random]\[Random].lck : This file is non-malicious.
- %AppData%\cfm\cfm.exe : This file is a copy of the original malware itself.
- %AppData%\corning inc\corning inc.exe : This file is a copy of the original malware itself.
- %AppData%\gencorp inc\gencorp inc.exe : This file is a copy of the original malware itself.
- %AppData%\peter kiewit sons'\peter kiewit sons'.exe : This file is a copy of the original malware itself.
- %AppData%\pid.txt : This file is non-malicious, possibly process ID of the malware.
- %AppData%\pidloc.txt : This file is non-malicious.
- %AppData%\remcos\logs.dat : This file is non-malicious.
- %AppData%\remcos\remcos.exe : This file is a copy of the original malware itself.
- %AppData%\windows update.exe : This file is a copy of the original malware itself.
- %Temp%\[Random].bat : This file is detected as BAT/Small.NAN!tr.
- %Temp%\[Random].exe : This file is detected as MSIL/AgentTesla.38BB!tr.
- %Temp%\[Random]\yu.exe : This file is detected as W32/GenKryptik.BXUS!tr.
- %Temp%\[Random]\yu.vbs : This file serves as an autostart for W32/GenKryptik.BXUS!tr.
- %Temp%\sysinfo.txt : This file is a text file.
- This malware may connect to any of the following remote sites(s):
- 21{Removed}.146.43.71
- 9{Removed}.192.100.60
- checkforupdat{Removed}.sytes.net
- hxxp://beamli{Removed}.ga/fine/kyle/shit.exe
- hxxp://sarmadgrou{Removed}.org/holaunblocekersw/WebPanel/api.php
- www.gloryblo{Removed}.tk/Panel/five/fre.php
- This malware may apply any of the following registry modification(s):
- HKEY_CURRENT_USER\Software\Microsoft\Windows\Currentversion\Run
- Corning inc = %AppData%\corning inc\corning inc.exe
- Peter kiewit sons' = %AppData%\peter kiewit sons'\peter kiewit sons'.exe
- Remcos = %AppData%\remcos\remcos.exe
- Gencorp inc = %AppData%\gencorp inc\gencorp inc.exe
- [Hash String] = [Original Malware Executed] ..
- Cfm = %AppData%\cfm\cfm.exe
- HKEY_CURRENT_USER\Software\Microsoft\Windows\Currentversion\Runonce
- Oiuyg = %Temp%\[Random]\yu.vbs
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\Currentversion\Run
- [Hash String] = [Original Malware Executed] ..
- HKEY_CURRENT_USER\Software\Microsoft\Windows\Currentversion\Run
- Below are some examples of Spam mail carrying this malware:
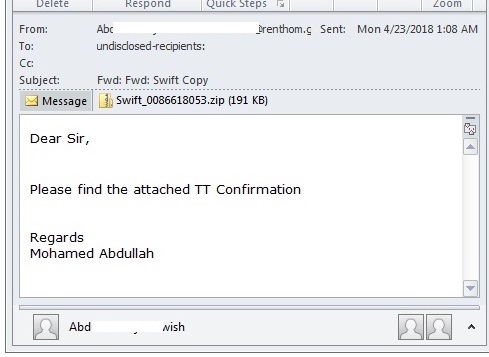
- Figure 1: Spam Mail.
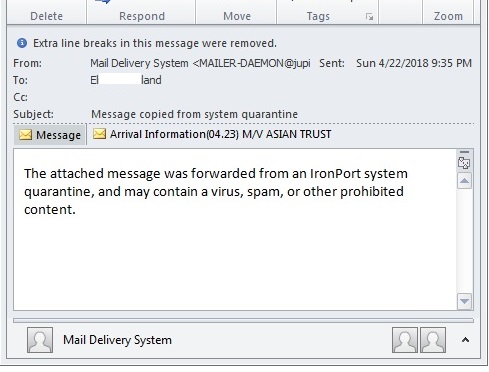
- Figure 2: Spam Mail.
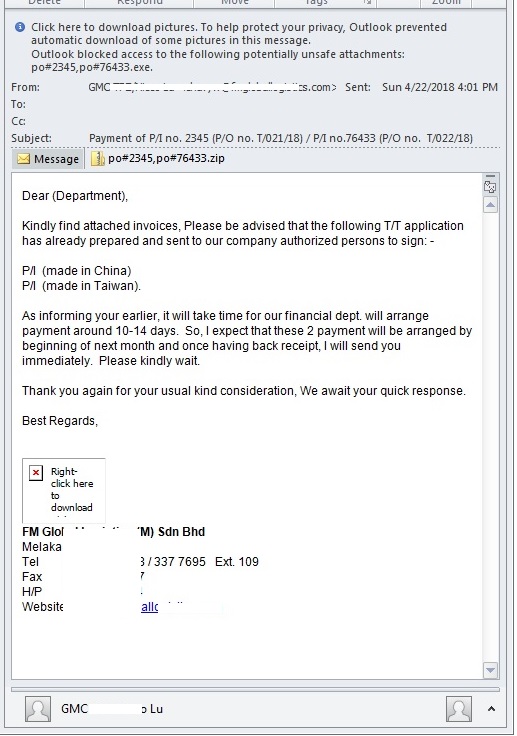
- Figure 3: Spam Mail.
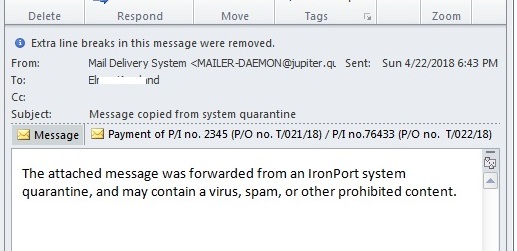
- Figure 4: Spam Mail.
- Some instances of this malware has been found to spread through USB External Drive, by dropping a copy of itself as sys.exe, along with an autorun.inf.
- Some instances of this malware may have Botnet capabilities.
- Some instances of this malware may have Injector capabilities.
- The malware itself may be deleted after execution.
 Recommended Action
Recommended Action
- Make sure that your FortiGate/FortiClient system is using the latest AV database.
- Quarantine/delete files that are detected and replace infected files with clean backup copies.
 Telemetry
Telemetry
Detection Availability
| FortiGate | |
|---|---|
| Extended | |
| FortiClient | |
| FortiMail | |
| FortiSandbox | |
| FortiWeb | |
| Web Application Firewall | |
| FortiIsolator | |
| FortiDeceptor | |
| FortiEDR |