JS/Agent.RNU!tr.dldr
 Analysis
Analysis
JS/Agent.RNU!tr.dldr is a generic detection for an Office OLE embedding Exploit. Since this is a generic detection, files that are detected as JS/Agent.RNU!tr.dldr may have varying behavior.
- It drops the following files:
- %TEMP%\[Random].exe : This file is detected as JS/Agent.RNU!tr.dldr.
- %TEMP%\[Random] (2).exe : This file is detected as JS/Agent.RNU!tr.dldr.
- %internet_cache%\content.ie5\[Random].exe : This file is detected as W32/Kryptik.GCFM!tr.
- %APPDATA%\[Random].exe : This file is detected as W32/Kryptik.GCFM!tr.
- Attempts to download from the following URL:
- hxxp://b.r{removed}.io/yrrvbl.exe
- hxxp://www.synergi{removed}.fr/wp-includes/js/jquery/og/invoicee.exe
- hxxp://www.canaangro{removed}.com/dc/doccs.exe
- hxxp://b.re{removed}.io/bhzczx.exe
- hxxp://kzkoicaal{removed}.com
- hxxp://www.synergi{removed}.fr/wp-includes/js/jquery/jv/prices.exe
- hxxp://b.re{remove}.io/bhzczx.exe
- Below is an illustration of an infected document:
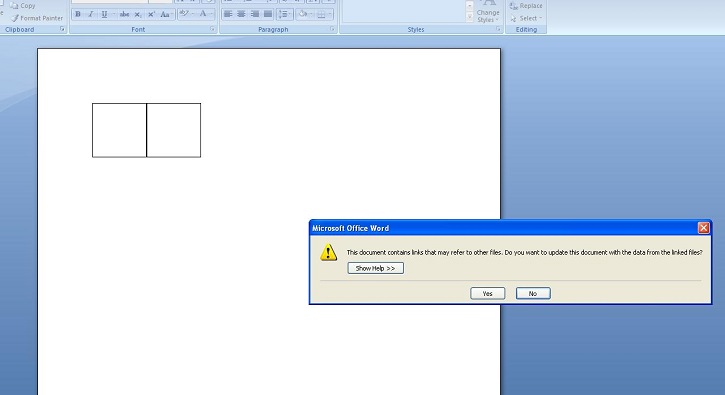
- Figure 1: Infected Document.
 Recommended Action
Recommended Action
- Make sure that your FortiGate/FortiClient system is using the latest AV database.
- Quarantine/delete files that are detected and replace infected files with clean backup copies.
 Telemetry
Telemetry
Detection Availability
| FortiGate | |
|---|---|
| Extended | |
| FortiClient | |
| FortiMail | |
| FortiSandbox | |
| FortiWeb | |
| Web Application Firewall | |
| FortiIsolator | |
| FortiDeceptor | |
| FortiEDR |