W32/GenKryptik.AVEL!tr.ransom
 Analysis
Analysis
W32/GenKryptik.AVEL!tr.ransom is a generic detection for a trojan that may include a potential Locky Ransomware. Since this is a generic detection, malware that are detected as W32/GenKryptik.AVEL!tr.ransom may have varying behaviour.
Below are examples of some of these behaviours:
- This malware may drop any of the following file(s):
- %SystemRoot%\system32\videostorage.exe
- %systemx86%\defragdefrag.exe
- %systemx86%\systemprovider.exe
- %SystemRoot%\system32\launchsystem.exe
- %systemx86%\helpdcom.exe
- %SystemRoot%\system32\cachecrypt.exe
- This malware may connect to any of the following remote sites(s):
- 19{Removed}.119.78.54
- This malware may start services that points to itself by applying any of the following registry modification(s):
- HKEY_LOCAL_MACHINE\System\Controlset001\Services\Videostorage
- Imagepath = %SystemRoot%\system32\videostorage.exe
- HKEY_LOCAL_MACHINE\System\Controlset001\Services\Launchsystem
- Imagepath = %SystemRoot%\system32\launchsystem.exe
- HKEY_LOCAL_MACHINE\System\Controlset001\Services\Cachecrypt
- Imagepath = %SystemRoot%\system32\cachecrypt.exe
- HKEY_LOCAL_MACHINE\System\Controlset001\Services\Videostorage
- During our tests we also observed some instances of Locky Ransomware under this detection that may drop any of the following file(s):
- %Desktop%\asasin-[xxxx].html : where x is any hexadecimal character, this file is dropped all over the affected hosts drive and will serve as ransom notes.
- %Desktop%\asasin.html : This will serve as ransom notes.
- %Desktop%\asasin.bmp : This file is a picture/image and will serve as ransom notes.
- Ransomware affected files will use the filenaming format XXXXXXXX-XXXX-XXXX-XXXXXXXX-XXXXXXXXXXXX.asasin, where X is any alphanumeric character.
- This malware was also observed to affect/encrypt files located on USB or external drives.
- Below is an illustration of the malware's Ransom notes:
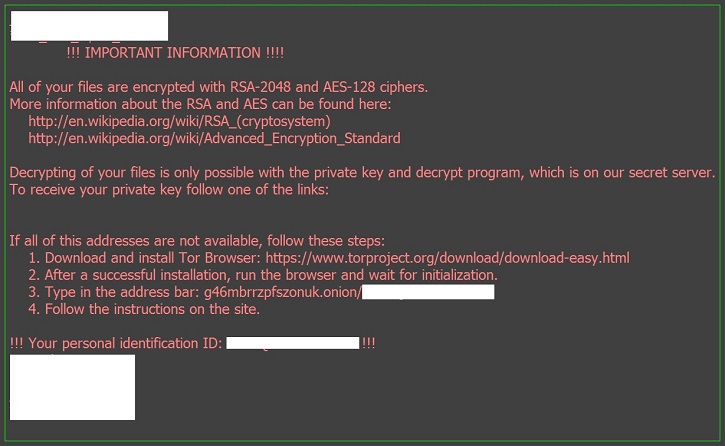
- Figure 1: Ransom notes.
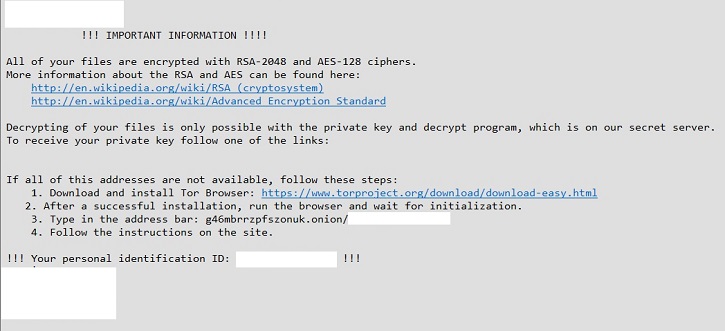
- Figure 2: Ransom notes.
 Recommended Action
Recommended Action
- Make sure that your FortiGate/FortiClient system is using the latest AV database.
- Quarantine/delete files that are detected and replace infected files with clean backup copies.
 Telemetry
Telemetry
Detection Availability
| FortiGate | |
|---|---|
| Extended | |
| FortiClient | |
| FortiMail | |
| FortiSandbox | |
| FortiWeb | |
| Web Application Firewall | |
| FortiIsolator | |
| FortiDeceptor | |
| FortiEDR |