LNK/Agent.HVE3!tr.dldr
 Analysis
Analysis
LNK/Agent.HVE3!tr.dldr is a generic detection for a LNK / PowerShell Downloader Trojan that installs Locky Ransomware,
detected as W32/GenKryptik.BCIL!tr.ransom.
Since this is a generic detection, this malware may have varying behaviour.
Along with W32/GenKryptik.BCIL!tr.ransom, below are some of the observed characteristics/behaviours for this infection:
- This malicious document has an embedded a powershell commandline through a Shortcut link located in %Temp%\. The powershell LNK then reads a further script obtained from hxxp://ddcm{Removed}.nl/KJhdshve3.
This script in turn will then download the actual Ransomware from any of the following sites:
- hxxp://teesaddictio{Removed}.com/HkkfY73r
- hxxp://dangelofavat{Removed}.com/HkkfY73r
- hxxp://cibeservic{Removed}.it/HkkfY73r
- hxxp://washingtoncountyyellowpagesdirector{Removed}.com/HkkfY73r
- hxxp://fso{Removed}.co.za/HkkfY73r
- hxxp://euroregistr{Removed}.net/HkkfY73r
- hxxp://ceocfonewslin{Removed}.com/HkkfY73r
- hxxp://evengrollighromso{Removed}.net/p66/HkkfY73r
- Below are illustrations of infected document(s):
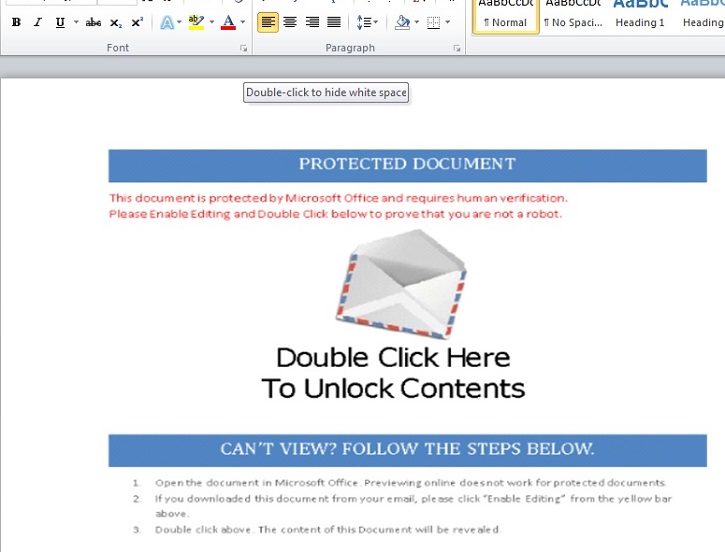
- Figure 1: Infected document.
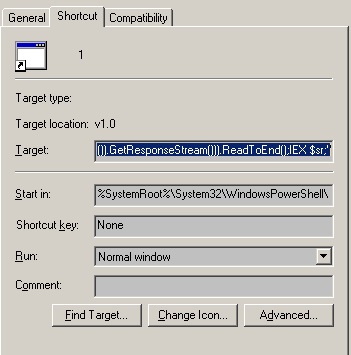
- Figure 2: Powershell LNK.
 Recommended Action
Recommended Action
- Make sure that your FortiGate/FortiClient system is using the latest AV database.
- Quarantine/delete files that are detected and replace infected files with clean backup copies.
 Telemetry
Telemetry
Detection Availability
| FortiGate | |
|---|---|
| FortiClient | |
| FortiAPS | |
| FortiAPU | |
| FortiMail | |
| FortiSandbox | |
| FortiWeb | |
| Web Application Firewall | |
| FortiIsolator | |
| FortiDeceptor | |
| FortiEDR |