JS/Kryptik.BIH!tr
 Analysis
Analysis
This detection is for a series of Javascript trojan and Win32 involved in an attack well known as Kovter.
Below are some of its known behaviours:
- This malware involves various Javascript components along with a possible Win32 binary detected as W32/GenKryptik.AJNV!tr.
- This malware attack has been known to have propagated through malicious Spam campaign or through click bait strategy.
- There has also been well known reports that a popular pornography site, pornhub, has been attacked and had known to serve infected Ads, that might have caused some infection to its viewers.
- The malware utilizes powershell command to further download the Kovter component.
- This malware has been known to insert data within the registry of the affected host serving as its persistence mechanism as indicated below:
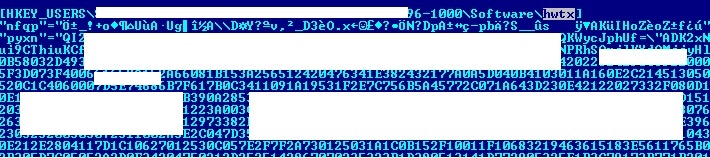
- Figure 1: Infected registry.
- Some samples of this malware may connect to any of the following remote sites(s):
- 18{Removed}.117.72.90
- phohww1188{Removed}.org
- cipaewallsandfloor{Removed}.net
- Some instances of this malware may delete itself after execution.
 Recommended Action
Recommended Action
- Make sure that your FortiGate/FortiClient system is using the latest AV database.
- Quarantine/delete files that are detected and replace infected files with clean backup copies.
 Telemetry
Telemetry
Detection Availability
| FortiGate | |
|---|---|
| Extended | |
| FortiClient | |
| FortiMail | |
| FortiSandbox | |
| FortiWeb | |
| Web Application Firewall | |
| FortiIsolator | |
| FortiDeceptor | |
| FortiEDR |
Version Updates
| Date | Version | Detail |
|---|---|---|
| 2020-03-04 | 75.71900 | Sig Updated |