 Analysis
Analysis
JS/Nemucod.DMX!tr is a generic detection for a type of javascript downloader trojan. Since this is a generic detection, malware that are detected as S/Nemucod.DMX!tr may have varying behavior. At the time of this analysis, the javascript downloader has been observed to download and run the GlobeImposter ransomware.
Below are examples of some of these behavior:
- This malware drops the following files:
- undefinedinternet_cacheundefined\content.ie5\e36puy1s\87wefhi[1].txt : This file is detected as W32/GlobeImposter.A!tr.
- undefinedTempundefined\lslqglvhn2.exe : This file is detected as W32/GlobeImposter.A!tr.
- undefinedAllUsersProfileundefined\lslqglvhn2.exe : This file is detected as W32/GlobeImposter.A!tr .
- undefinedTempundefined\__te.tmp.bat : This file is detected as BAT/Agent.352B!tr.
- The following suspicious registry key(s) have been added to cause the program to be run each time a user logs on:
- HKEY_CURRENT_USER\Software\Microsoft\Windows\Currentversion\Runonce
- Certificatescheck = undefinedAllUsersProfileundefined\lslqglvhn2.exe
Entries made by executable programs are deleted after being processed.
- This javascript downloader downloads a file from the following URL:
- hxxp://flooringforyo{Removed}.co.uk/87wefhi??LslqGlVHN=LslqGlVHN
- Below is an example after the system get infected : How to decypt files:
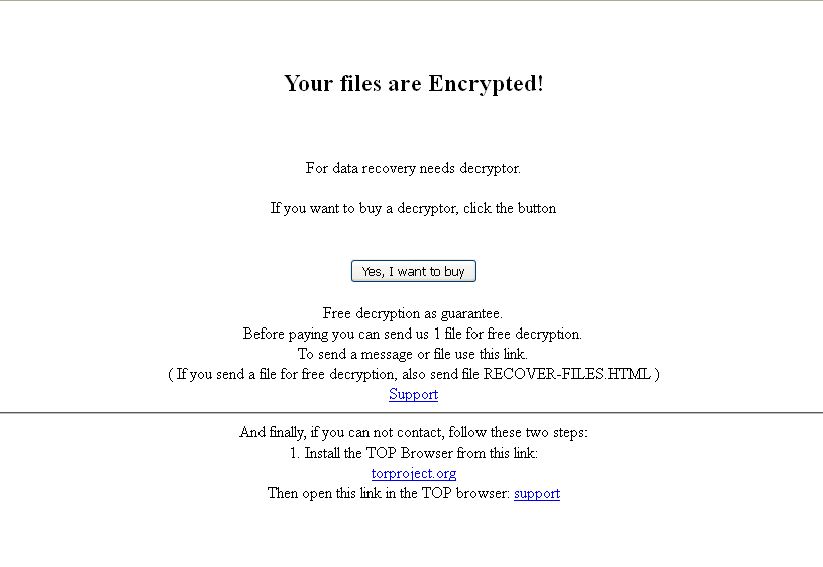
- Figure 1: Instruction to how to decrypt the encrypted files.
|
 Analysis
Analysis Recommended Action
Recommended Action Telemetry
Telemetry