W32/Kryptik.FSNS!tr
 Analysis
Analysis
W32/Kryptik.FSNS!tr is a generic detection for a type of trojan. Since this is a generic detection, malware that are detected as W32/Kryptik.FSNS!tr may have varying behavior. At the time of this analysis, this has been detecting variants of the Cerber Ransomware.
Below are examples of some of the behaviors observed in this malware:
- Drops files on the affected host using the following filenames:
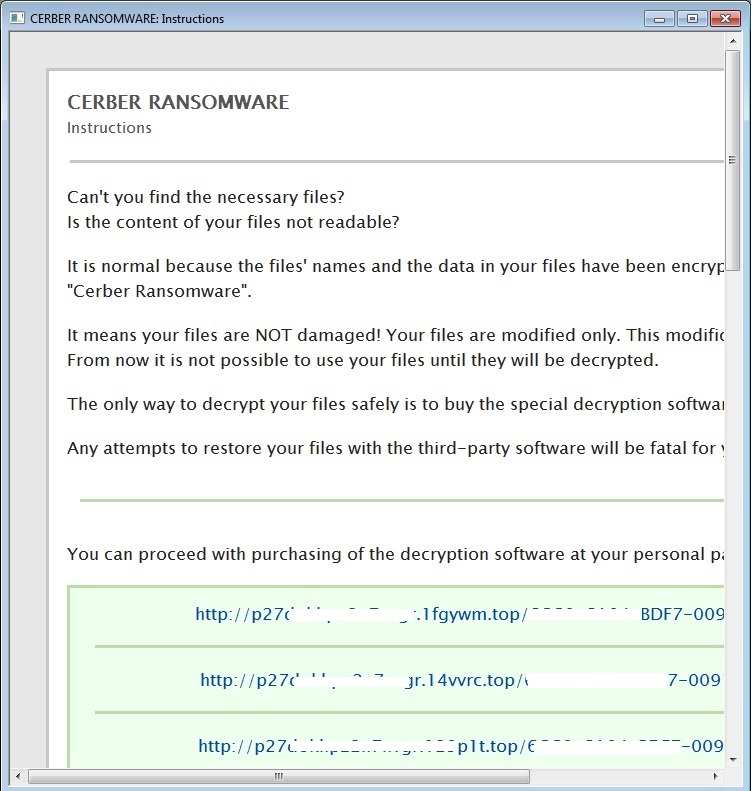
- _R_E_A_D___T_H_I_S___[Random]_.hta : This is an HTML file that contains ransom instructions and is detected as HTML/Kryptik.FSNS!tr. It shows the following when opened:
- Figure 1: Ransom instructions.
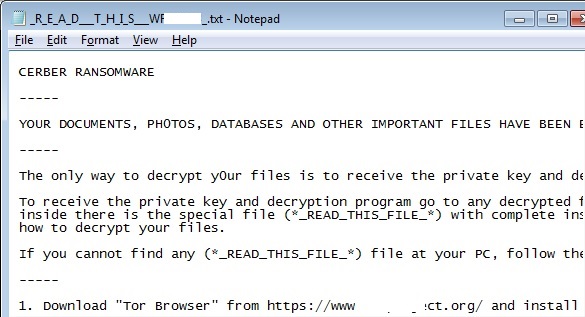
- _R_E_A_D___T_H_I_S___[Random]_.txt : This file is another ransom instruction in text format as illustrated below:
- Figure 2: Ransom instructions.
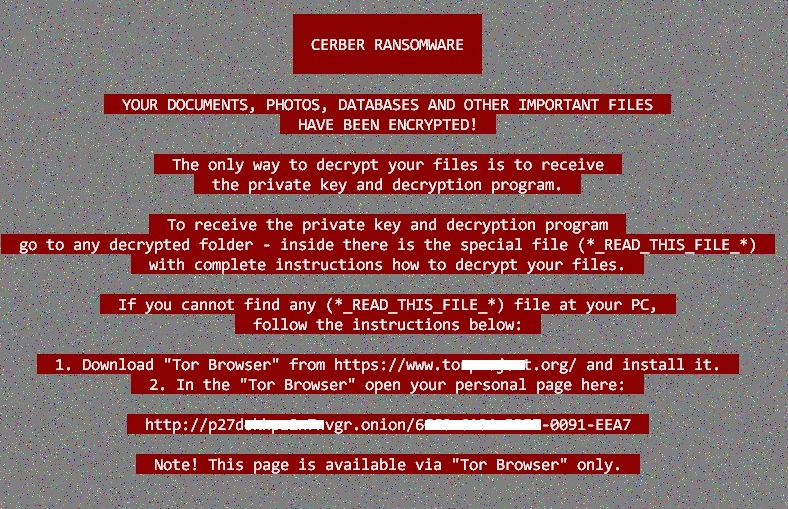
- undefinedAppDataundefined\Local\Temp\[Random].bmp : This picture file is displayed on the user's desktop
- Figure 3: Host's desktop.
- In some instances, this ransomware has been observed to only partially encrypt the target file.
- It applies the following registry modification that affects the user's desktop:
- HKEY_CURRENT_USER\Control Panel\Desktop
- Wallpaper="undefinedAppDataundefined\Local\Temp\[Random].bmp"
- HKEY_CURRENT_USER\Control Panel\Desktop
- It also issues the following command to enable the Windows Firewall, possibly disallowing other malware from taking over affected hosts.
- "undefinedSystemDirundefined\netsh.exe advfirewall set allprofiles state on"
- "undefinedSystemDirundefined\netsh.exe advfirewall reset"
- This malware also generates network traffic via UDP on the subnet 178.xx.160.xx.
- It connects to the following URLs:
- api.block{Removed}.com
- btc.blo{Removed}.io
- This ransomware employs a captcha scheme, possibly designed by the attacker to avoid automated attempts on obtaining the attackers decrypt tool.
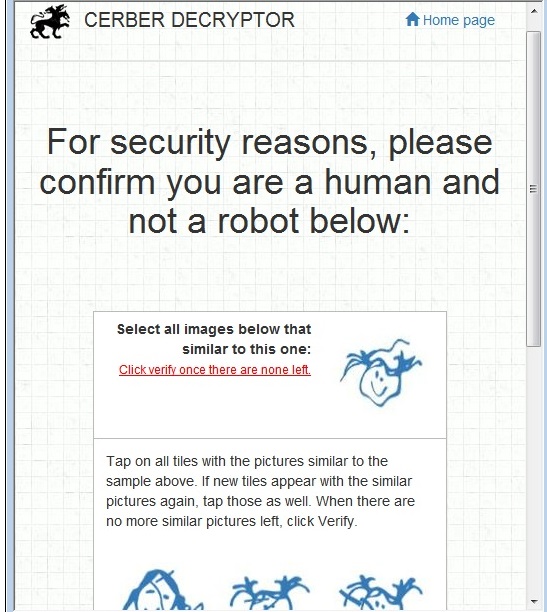
- Figure 4: Cerber's captcha.
- In some instances, this malware deletes itself after execution.
 Recommended Action
Recommended Action
- Make sure that your FortiGate/FortiClient system is using the latest AV database.
- Quarantine/delete files that are detected and replace infected files with clean backup copies.
 Telemetry
Telemetry
Detection Availability
| FortiGate | |
|---|---|
| Extended | |
| FortiClient | |
| FortiMail | |
| FortiSandbox | |
| FortiWeb | |
| Web Application Firewall | |
| FortiIsolator | |
| FortiDeceptor | |
| FortiEDR |