Android/FakeDefend.B!tr
 Analysis
Analysis
Android/FakeDefend.B!tr is a piece of malware targetting Android mobile phones.
The malicious package comes disguised as a Browser update for Mozilla Firefox. However, in the background, it sends out the phone's IMEI and some other information to a remote server signalling installation of the malware on the phone.
It also retrieves a list of phone numbers from another remote server.
The malware appears to have been written by the same authors as Android/FakeDefend.A!tr
The main application is called "Browserupdate" (ref Fig1) and comes in the package "com.example.silnetcall" (mistyped as such).
![]()
Fig1 : Browserupdate Icon
As the name suggests, the application masquerades as a Browser update application. When launched, the user sees a screen as seen in Fig2
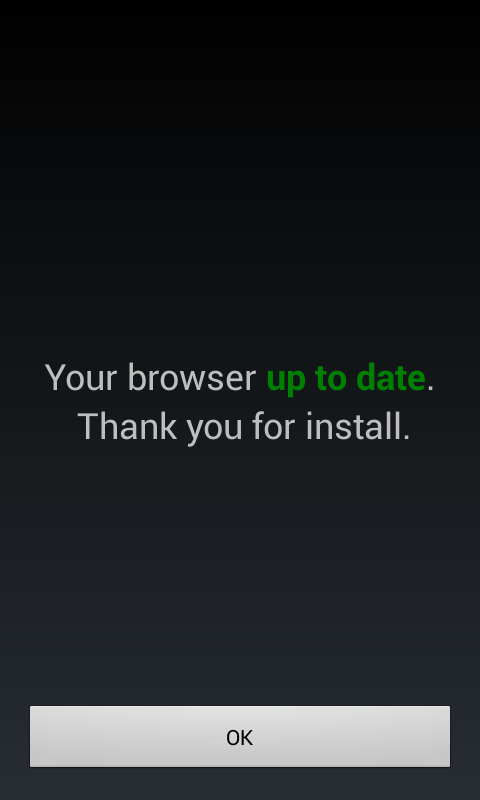
Fig2 : Main Application Screen
However, no update is installed. Instead, in the background, the following operations are carried out :
When the application is installed, an HTTP request is sent to
"http://XX.XX.XXX.231/numbers/index.php"which responds with an array of phone numbers. These numbers are saved into a database called NUMBERS.db.
Next, an HTTP request is sent to the URL found hardcoded in the package (saved as "domains" in the shared preferences) in the format
[Domains] + "api/ping/?uid=" + [UID] + "id.subid=" + [ID.SUBID] + "android_version=" + Build.VERSION.SDK_INT + "device_manufacturer=" + Build.MANUFACTURER + " " + Build.MODEL + "connection_type=" + [CONN] + "location=" + [LOC] + "operator=" + [OP_NAME] + "number=" + [NUM] + "density=" + [DENS] + "resolution=" + [DISP]where
- UID = MD5 hash of a randomly chosen number
- ID and SUBID are found hardcoded in the package
- CONN = "" or "Wif-Fi"(misspelt) or "Mobile UNKNOWN"
- LOC = Latitude + ", " + Longitude
- OP_NAME = SIM Operator Name
- NUM = IMSI or IMEI
- DENS = DisplayMetrics.density
- DISP = DisplayMetrics.widthPixels + "x" + DisplayMetrics.heightPixels
The malware also contains a LockScreen as seen in Fig3 that should ideally be displayed when one of the numbers on the list of numbers in NUMBERS.db is dialled but the malware doesn't function as intended.
We assume the malware is an incomplete/damaged version of what the authors originally intended to make.
The LockScreen can easily be closed/escaped.
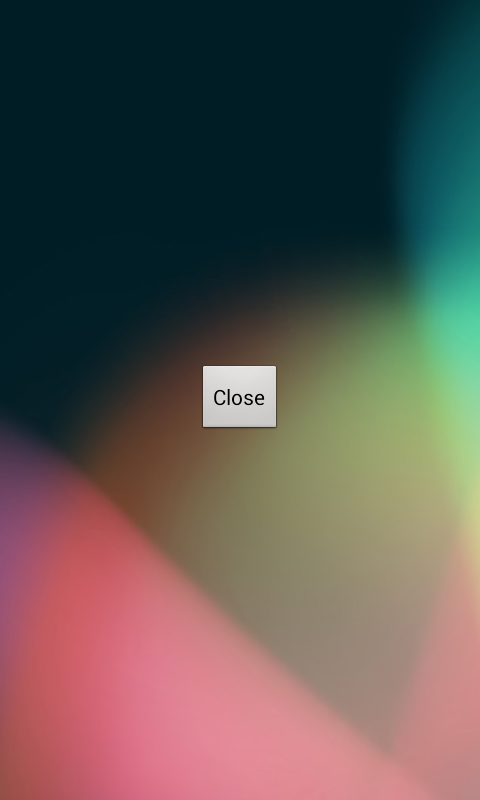
Fig3 : Lock Screen
The application is kept running in the background by means of a KeepAliveService and an UpdateService that are launched whenever the Screen is turned on or off.
Permissions required by the application:
- INTERNET
- CALL_PHONE
- WAKE_LOCK
- SYSTEM_ALERT_WINDOW
- READ_PHONE_STATE
- MODIFY_AUDIO_SETTINGS
- WRITE_SETTINGS
- RECEIVE_BOOT_COMPLETED
- ACCESS_FINE_LOCATION
- ACCESS_COARSE_LOCATION
- ACCESS_NETWORK_STATE
Certificate information: Owner: CN=fc, OU=hjb; Issuer: CN=fc, OU=hjb
 Recommended Action
Recommended Action
- FortiGate Systems
- Check the main screen using the web interface for your FortiGate unit to ensure that the latest AV/NIDS database has been downloaded and installed on your system - if required, enable the "Allow Push Update" option.
FortiClient Systems
- Quarantine/delete files that are detected and replace infected files with clean backup copies.
 Telemetry
Telemetry
Detection Availability
| FortiGate | |
|---|---|
| Extended | |
| FortiClient | |
| Extreme | |
| FortiAPS | |
| FortiAPU | |
| FortiMail | |
| Extreme | |
| FortiSandbox | |
| Extreme | |
| FortiWeb | |
| Extreme | |
| Web Application Firewall | |
| Extreme | |
| FortiIsolator | |
| Extreme | |
| FortiDeceptor | |
| Extreme | |
| FortiEDR |