Android/Gamex.A!tr
 Analysis
Analysis
Android/Gamex.A!tr is a piece of malware targetting Android mobile phones.
The malicious package may come disguised as applications such as SDCardBooster or BlueTooth File Transfer or GPS that require root permissions from the end user. If this permission is granted, a second package contained in the assets of the original package is installed and started. This internal package then sends the victim's IMEI and IMSI to the attacker's server. Subsequently, it downloads a list of packages to be installed on the victim's phone and finally downloads and installs each package on the victim's phone.
The malware may come in applications called "SDboost", "GPS", "Bluetooth File Transfer" etc. and may come in the packages "de.mehrmannd.sdbooster", "it.medievals.blueftp", "com.chartcrossd.gpstest" etc.
These applications start a service called com.android.md5.Settings which in turn uses classes in a package called com.gamex.inset that perform the malicious activity of the application described below.
Firstly, a file found in the package assets called "logos.png" is decrypted and saved to "/system/app/ComAndroidSetting.apk".
This saved package is then installed and a broadcast sent out to start the application.
The inner package is detected as Android/Gamex.B!tr and details of this inner package are as follows.
- It comes in a package called com.android.setting (not to be confused with the legitimate Android Settings package "com.android.settings")
- It is automatically launched in the background whenever the phone is switched on.
- When launched, it contacts the URL "hxxp://www.[REMOVED].com/inputex/index.php?s=/Interface/keinter/a1/" + IMEI + "/a2/" + IMSI + "/a3/" + Build.MODEL + "/index/" + CMP_ID where CMP_ID is found in the package's manifest file (eg: 'xian1234') NOTE: The URL above is obtained by decryption of a file logo.png found in the package assets
- Also, contained in the package assets is a file called icon.png which is decrypted in order to obtain another package. This package is installed and launched. This package is detected as Android/Gamex.A!tr.dldr and is described below.
- It is called "Updater" and has the package name com.android.update"
- This service is also automatically launched in the background whenever the phone is switched on.
- Next, it downloads a list of applications from the URL "hxxp://www.[REMOVED].com/InstallApk/php4sam.php".
- The list of URLs downloaded is saved into a database called soft.db in a table dbsoft NOTE: The URL above is obtained by decryption of a file icon.png found in the package assets
- It then downloads these applications depending upon network state from the URL "hxxp://www.[REMOVED].com/inputex/index.php?Interface/neiinter/a1/" + IMEI + "/nam/" + [App_name]
- Finally, the downloaded applications are installed on the victim's phone.
The figure below shows the Updater application seen on the list of Running Applications in the Settings Menu
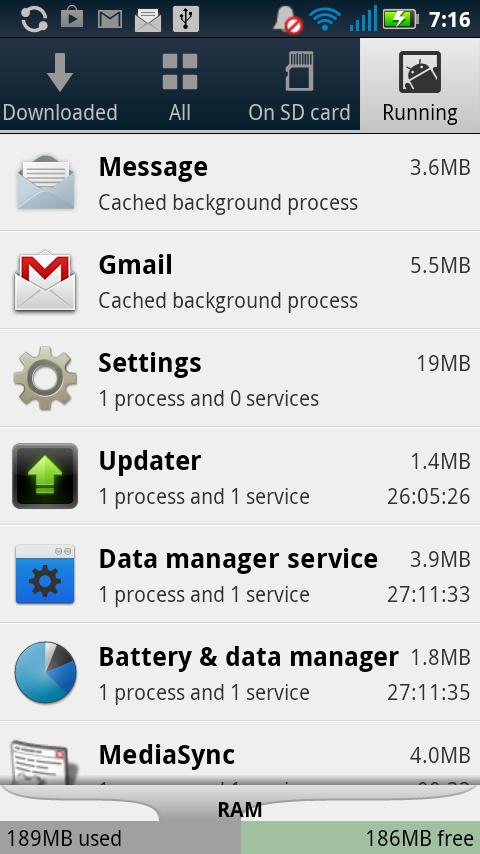
Fig1 : Updater application on list of Running applications
Permissions required by the application:
- INTERNET
- WRITE_EXTERNAL_STORAGE
- ACCESS_NETWORK_STATE
- RECEIVE_BOOT_COMPLETED
- READ_PHONE_STATE
Certificate information:
- Owner: CN=uu
- Issuer: CN=uu
- Serial number: 393af07b
 Recommended Action
Recommended Action
- FortiGate Systems
- Check the main screen using the web interface for your FortiGate unit to ensure that the latest AV/NIDS database has been downloaded and installed on your system - if required, enable the "Allow Push Update" option.
FortiClient Systems
- Quarantine/delete files that are detected and replace infected files with clean backup copies.
 Telemetry
Telemetry
Detection Availability
| FortiGate | |
|---|---|
| Extreme | |
| FortiClient | |
| Extended | |
| FortiMail | |
| Extended | |
| FortiSandbox | |
| Extended | |
| FortiWeb | |
| Extended | |
| Web Application Firewall | |
| Extended | |
| FortiIsolator | |
| Extended | |
| FortiDeceptor | |
| Extended | |
| FortiEDR |