VBA/Emotet.RES!tr
 Analysis
Analysis
VBA/Emotet.RES!tr is a generic detection for a trojan.
Since this is a generic detection, malware that are detected as VBA/Emotet.RES!tr may have varying behaviour.
Below are some of its observed characteristics/behaviours:
- VBA/Emotet.RES!tr is related to the Emotet resurgence outbreak.
- This malware comes in the form of an inflated Microsoft Word document, typically distributed through spam emails, and contains a malicious payload within the VBA script.
- Upon opening the document, there will be an image in the file declaring the document as protected and asking the user to enable editing/content to allow macros. After clicking "Enable Content", the malicious script will execute and attempt to connect to malicious domains to download malicious payloads, such as Emotet.
- The malware will utilize Regsrv32.exe to register the downloaded file so that the malicious file can be used by Windows.
- Below are images of the malicious document:
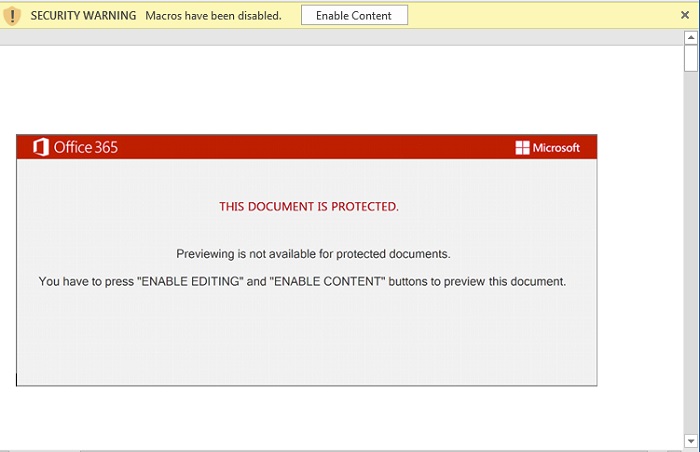
- Figure 1: Document with message directing user to click "Enable Content".
- Figure 2: Document inflated with 0's to possibly avoid AV scanner detection.
- Following are some of the exact IOCs/file hashes associated with this detection:
- Md5: 77504bdcdb24c73c4347b8c7c71b77a2
Sha256: c6391461a4278c741a977b22425a8e0441c1c7eaa0f07717edf99fc1499a78a4 - Md5: 798044fd3b8172ecfee2b69b6a8a5919
Sha256: 6ba3993b0f9e4e527f4f63c01ea026ad7a8f7c8bf78457d0d4bbdcfebc9d8dd6 - Md5: 98b22a542af160beee9887f52caa9e32
Sha256: df92b51119c69423299a6c77ef48ccf5c88871f17a6178e55a12896e364854ee - Md5: af1a92a615b9c8fa813b798af55218f9
Sha256: 92e35aabe2753c1b509415139e2d296a9b8b87f47f1ee6f50ac95f1151a7bcbc - Md5: 8b1da5c1512d21653cf0c023e18f1570
Sha256: 22d9b272b534166f2f7cbf7250bfeff13b2063df8a207fd96f24d85c2b24c334
- Md5: 77504bdcdb24c73c4347b8c7c71b77a2
 Recommended Action
Recommended Action
- Make sure that your FortiGate/FortiClient system is using the latest AV database.
- Quarantine/delete files that are detected and replace infected files with clean backup copies.
 Telemetry
Telemetry
Detection Availability
| FortiGate | |
|---|---|
| FortiClient | |
| FortiAPS | |
| FortiAPU | |
| FortiMail | |
| FortiSandbox | |
| FortiWeb | |
| Web Application Firewall | |
| FortiIsolator | |
| FortiDeceptor | |
| FortiEDR |