MSIL/Filecoder.7DB7!tr.ransom
 Analysis
Analysis
MSIL/Filecoder.7DB7!tr.ransom is a generic detection for a trojan.
Since this is a generic detection, malware that are detected as MSIL/Filecoder.7DB7!tr.ransom may have varying behaviour.
Below are some of its observed characteristics/behaviours:
- Upon execution, this ransomware will encrypt the victims's data and replace the extension of the encrypted files with ".txt". The ransomware will write to the encrypted files and place the ransom message inside the file essentially creating a ransom note out of each encrypted file. The note offers decryption for 1 file for a small fee and directs the user to a TOR site for payment. Affected users are discouraged on taking this action as it does not guarantee the retrieval of data upon payment. The malware will continue to run in the background, encrypting any newly added files to the system.
- Below are images of the ransomware:
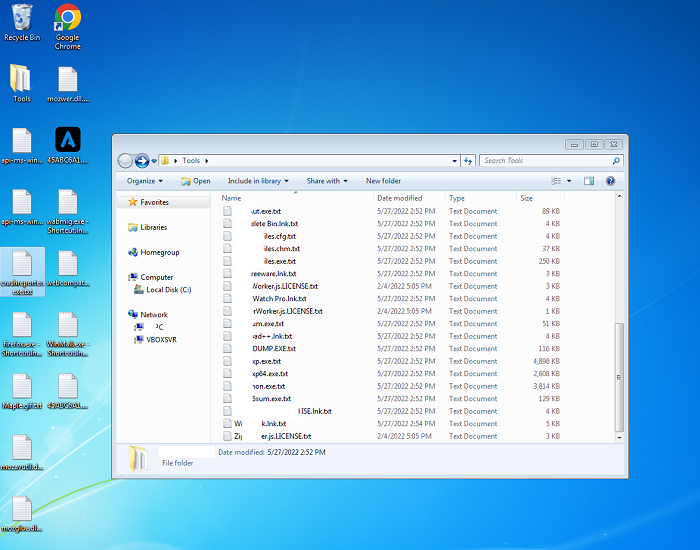
- Figure 1: Encrypted files.
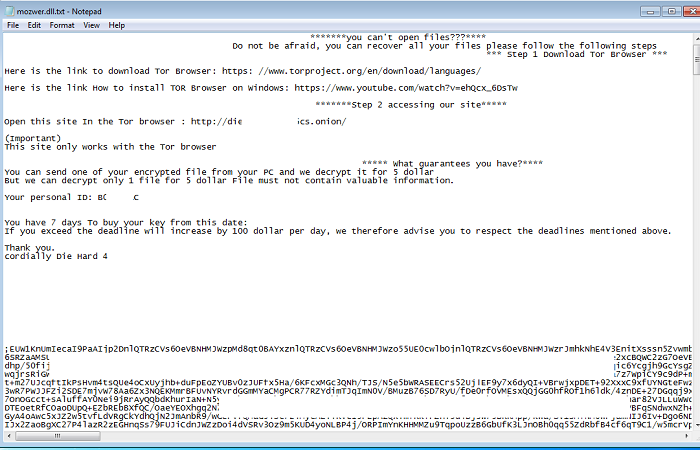
- Figure 2: Ransom note.
- Below are some of the sites associated with the trojan:
- http://die[removed]5cs.onion
- Following are some of the near/exact IOCs/file hash associated with this detection:
- Md5: a96c22902a9a7c5d4fc3282473297db7
Sha256: 1f41de97656b9567db858082699fb516514a1c7ac2cb3c047543ca71566cea98
- Md5: a96c22902a9a7c5d4fc3282473297db7
 Recommended Action
Recommended Action
- Make sure that your FortiGate/FortiClient system is using the latest AV database.
- Quarantine/delete files that are detected and replace infected files with clean backup copies.
 Telemetry
Telemetry
Detection Availability
| FortiGate | |
|---|---|
| Extreme | |
| FortiClient | |
| Extended | |
| FortiMail | |
| Extended | |
| FortiSandbox | |
| Extended | |
| FortiWeb | |
| Extended | |
| Web Application Firewall | |
| Extended | |
| FortiIsolator | |
| Extended | |
| FortiDeceptor | |
| Extended | |
| FortiEDR |