W32/FilecoderPhobos.C!tr.ransom
 Analysis
Analysis
W32/FilecoderPhobos.C!tr.ransom is a generic detection for a trojan.
Since this is a generic detection, malware that are detected as W32/FilecoderPhobos.C!tr.ransom may have varying behaviour.
Below are some of its observed characteristics/behaviours:
- This malware is associated with the Phobos ransomware family.
- Upon execution, this ransomware will disable the firewall, delete shadow copies and then proceed to encrypt the victim's files. The encrypted file names will be appended with the Phobos variant name. The appended extension will be in the pattern of: id[victim_id].[email_address].[variant_name]. Some of the variant names include "elbie", "eking", "makop", "eight", "polsat", "acuna" and "eject".
- After encrypting the victim's data, two ransom notes, "info.hta" and "info.txt", will be dropped to the Desktop and root directory. The note will display a message informing the victim that their files have been encrypted and will direct the victim to make contact with the attacker via email. The note asks for payment in the form of bitcoin and offers decryption for 5 files as a guarantee. Affected users are discouraged on taking this action as it does not guarantee the retrieval of data upon payment.
- The ransomware will continue to run in the background, encrypting any newly created files and an autorun registry will be created for persistence.
- Below are images of the result of executing the ransomware:
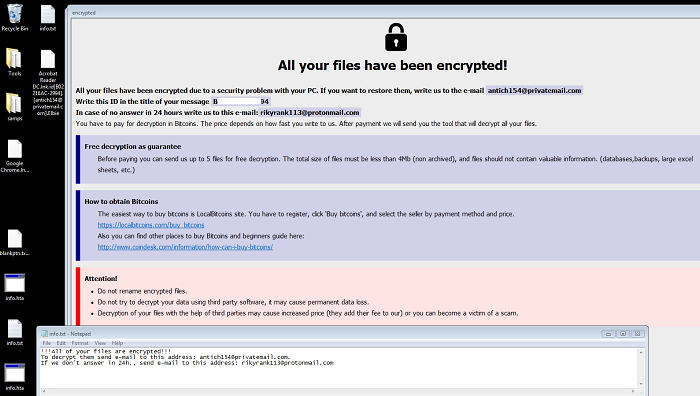
- Figure 1: Desktop with ransom notes (elbie variant).
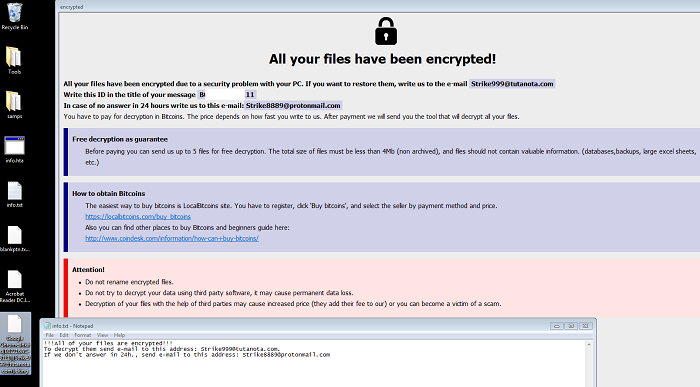
- Figure 2: Desktop with ransom notes (eking variant).
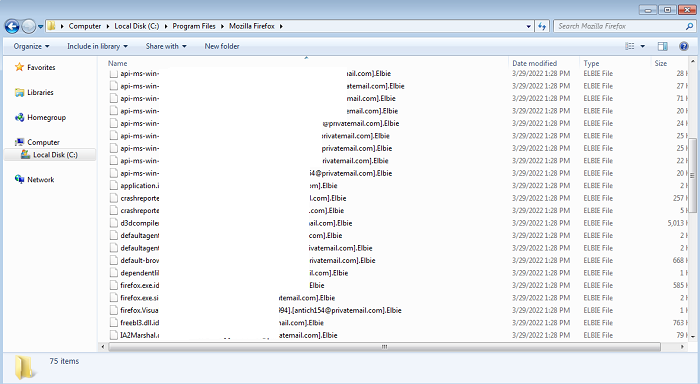
- Figure 3: Encrypted files.
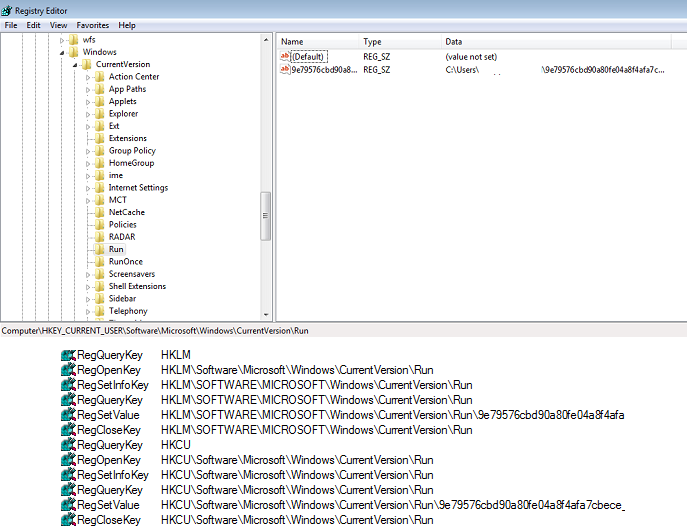
- Figure 4: Autorun registry.
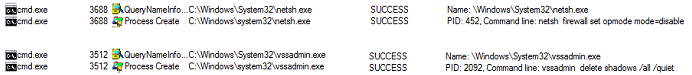
- Figure 5: Disable firewall and delete shadow copies.
- Following are some of the near/exact IOCs/file hash associated with this detection:
- Md5: 9e79576cbd90a80fe04a8f4afa7cbece
Sha256: 9bd421c6f7f7d8278036944fcad3e04db408619678acf1b2024ef69d85c3932b - Md5: 1d8c9e87415b2ae89fbe5060556b1816
Sha256: 00ce890733b76a4a28523664b4eba086cb66b1eb446b7503c9f8f3ffdddaa7e5 - Md5: 93e8cbb2c4da8376bb16a0a7e964c046
Sha256: 58fb76057468661da38efc981c64292987184226f82b7eddeff1844f6a725d95 - Md5: 373a7a21c65d50861b0f7fa81d998165
Sha256: 4c957fadcdcaa43f3ea17c2f6db5cec7930d79122e05f920792e460b3ae34f52 - Md5: ab7b66ee5385cb473b9c15db3e239692
Sha256: 8710ad8fb2938326655335455987aa17961b2496a345a7ed9f4bbfcb278212bc
- Md5: 9e79576cbd90a80fe04a8f4afa7cbece
 Recommended Action
Recommended Action
- Make sure that your FortiGate/FortiClient system is using the latest AV database.
- Quarantine/delete files that are detected and replace infected files with clean backup copies.
 Telemetry
Telemetry
Detection Availability
| FortiGate | |
|---|---|
| FortiClient | |
| FortiAPS | |
| FortiAPU | |
| FortiMail | |
| FortiSandbox | |
| FortiWeb | |
| Web Application Firewall | |
| FortiIsolator | |
| FortiDeceptor | |
| FortiEDR |