Android/PrnLocker.A!tr
 Analysis
Analysis
Android/PrnLocker.A!tr.dldr is a piece of malware targetting Android mobile phones.
The malicious package generally comes within or disguised as an application for viewing for pornographic videos or as a browser update.
However, in the background, it installs a Trojan horse contained within itself on the phone, that periodically leaks Build information about the phone as well as contact information, call logs and pictures taken.
Lastly, it inhibits regular usage of the phone by retaining a message on the phone stating the system is being updated.
The main applications generally come as a BrowserUpdate, in packages named "edu.greenhouses.icing", "net.elite.combinations" etc.
In some cases, it is also found contained within and loaded by Android/PrnLocker.A!tr.dldr
Upon launch, the application requests Device Administrator Privileges, which, if granted, make uninstallation of the application tricky.
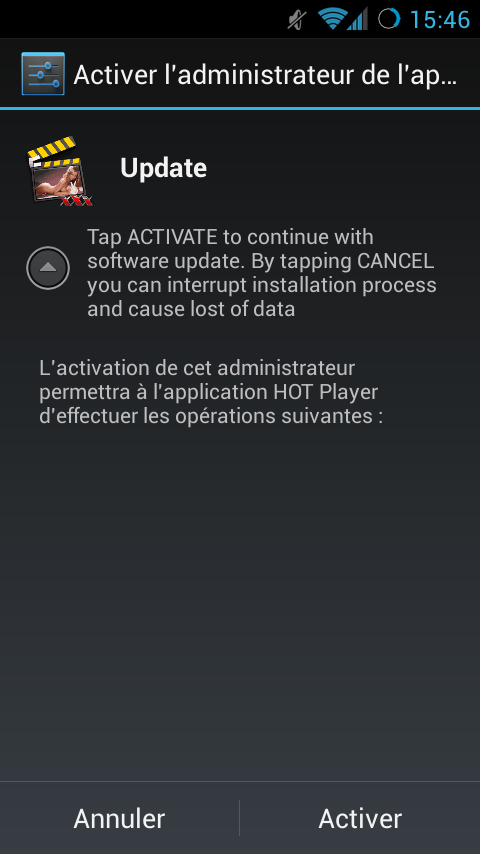
Fig1 : Request for Device Administrator Privileges
The package is obfuscated and encrypts the main strings used by the package. An example of the decrypted configuration strings is :
[overanxious, diffusivity, 62, android.intent.action.VIEW, data, topology, removeActiveAdmin, display_name, com.android.settings.DeviceAdminAdd, android_id, degraded, seclocktexts, waitlock, abloom, web1: , ce, le, indeed, hacks, se, javascript:badCode(), id, params.png, EGZrUeYMICRj1CeRXt0VNQ==, android.intent.action.MAIN, 61, ,, Tap ACTIVATE to continue with software update. By tapping CANCEL you can interrupt installation process and cause lost of data, 17, rws, generosity, ENETUNREACH, 5, fat, 0, seclock, add, file:///android_asset/none.html, ___, 14, exception , AES, 9, energy, cam1, .apk, 15, requestLocationUpdates, mockup, chalice, speedily, badcode, svc, power, android.hardware.camera.front, outvoted, floppy, .html, phone, phones, .jpg, ., 6, android.hardware.camera, hardlock, r, thatcher, alarm, 1, da1, vurl, loadInstallData, same, apkfile, fewness, com.android.settings, utf-8, reinsurance, 3, javascript:loadImage(), package:, market://details?id=, 4, , android.intent.action.SCREEN_OFF, android.app.action.ADD_DEVICE_ADMIN, com.android.vending, 11, notification, android.intent.action.USER_PRESENT, android.intent.category.HOME, 16, 5.4, hxxp://pXXXXXy.biz, simplify, 2, connectivity, [], rephrase, beleaguered, onced, 8, tripoli, destabilise, android.intent.action.DELETE, device_policy, network, hxxp://seXXXXXXXXbe.biz, spellable, alluvia, android.intent.action.BOOT_COMPLETED, html, report, com.android.packageinstaller, 12, 10, unlock, unashamedly, com.android.launcher, 7, location, webapi, number, palming, tpsc, gps, ?p=, android.app.extra.ADD_EXPLANATION, prohibitively, activity, dispossession, enhancements, android.intent.action.SCREEN_ON, meaninglessly, null, file:///android_asset/index.html, S, file://, force-locked, N, softlock, result, none, window, yyyy-MM-dd HH:mm:ss.SSS, bearing, android.permission.READ_SMS, 60, index.html, fri, grills, android.app.extra.DEVICE_ADMIN, rurl, application/vnd.android.package-archive, com.android.packageinstaller.PackageInstallerActivity, date DESC, trademark, 13, ]The malware collects information from the phone and mainly sends out 2 kinds of HTML POST messages with different parameters explained below:
- report These messages are sent after the malware is installed and every time a picture is taken from the infected phone. The parameters Build Information, details of saved contacts and log information from attempts to launch the front camera.
- data These messages include parameters pertaining to Build Information, Call logs, Installed package information and Location info. The messages are sent in AES encrypted, then Base-64 encoded format.

Fig2 : Screen Lock
Permissions required by the application:
- INTERNET
- READ_PHONE_STATE
- WAKE_LOCK
- ACCESS_NETWORK_STATE
- RECEIVE_BOOT_COMPLETED
- PROCESS_OUTGOING_CALLS
- WRITE_EXTERNAL_STORAGE
- WRITE_CONTACTS
- WRITE_SETTINGS
- SYSTEM_ALERT_WINDOW
- CAMERA
- GET_TASKS
- ACCESS_COARSE_LOCATION
- ACCESS_FINE_LOCATION
- ACCESS_COARSE_UPDATES
- READ_CONTACTS
- READ_PROFILE
- READ_CALL_LOG
Certificate information:
- Owner: CN=, OU=, O=, C=
- Issuer: CN=, OU=, O=, C=
 Recommended Action
Recommended Action
- Make sure that your FortiGate/FortiClient system is using the latest AV database.
- Quarantine/delete files that are detected and replace infected files with clean backup copies.
 Telemetry
Telemetry
Detection Availability
| FortiGate | |
|---|---|
| Extreme | |
| FortiClient | |
| Extended | |
| FortiMail | |
| Extended | |
| FortiSandbox | |
| Extended | |
| FortiWeb | |
| Extended | |
| Web Application Firewall | |
| Extended | |
| FortiIsolator | |
| Extended | |
| FortiDeceptor | |
| Extended | |
| FortiEDR |