Android/Spyoo.A!tr.spy
 Analysis
Analysis
Android/Spyoo.A!tr.spy is a piece of malware targetting Android mobile phones.
The package, once registered wiht a remote website, allows information from the victim's phone such as GPS location and SMS, call and browsing history to be sent regularly to this location. It also contains the ability to hide incoming calls from specific numbers from the victim.
Technical Details
The malware comes in the form of a package called iits.spyoo. Upon installation, the user doesn't see the application icon in the phone's menu however, it can be seen it in the list of installed applications in the Settings Menu under the name "Copy9"(refer Spyoo-A-Icon.png).
Fig1. The malicious application icon
The permissions required by the application are shown in the figure below.
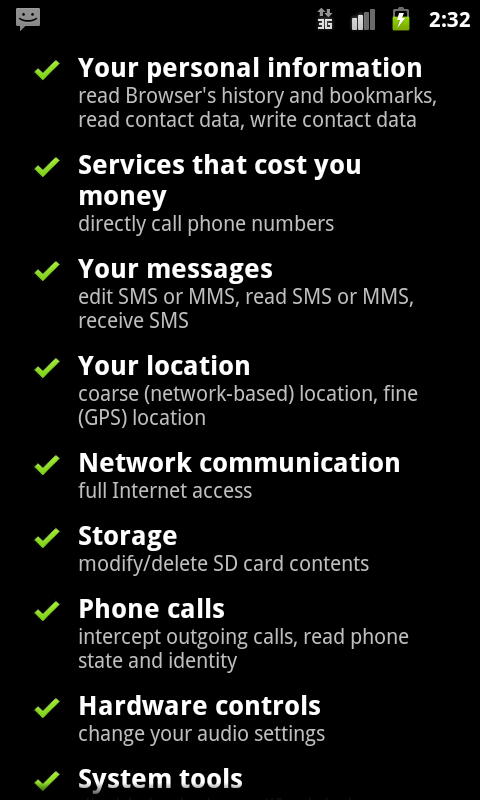
Fig2. Permissions required by the application. The malicious package contains the following important components :
- iits.receiver.LoginReciever: This receiver is launched every time an outgoing call is made from the phone. If the number called equals a special code "#123456*", it launches the Program activity described below
- iits.spyoo.Program (refer Fig3): This is the main activity of the application. It, in turn, launches the Login activity described below

Fig3. Main program launched after entering the special code - iits.spyoo.Login (refer Fig4): It initializes a database named "SPYOO" that is used to gather information about the victim's phone sent by the application. If the phone is registered with the remote URL i.e. a valid username and password are entered, it launches the service SpyooService described below
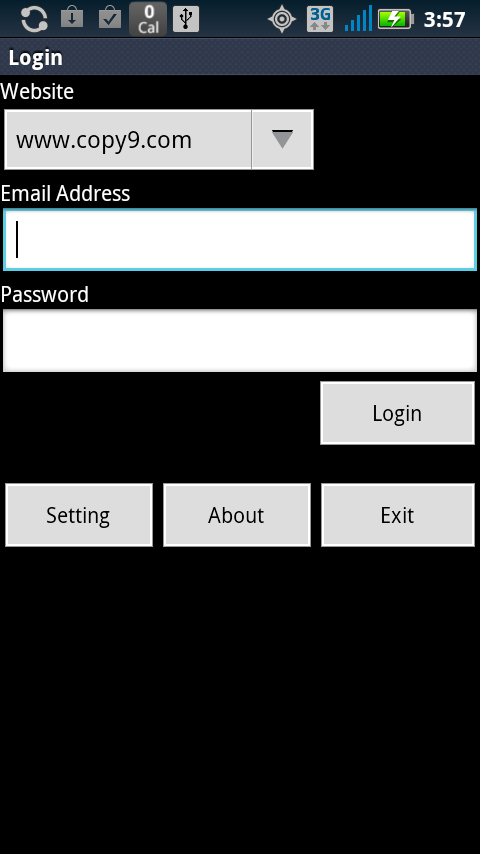
Fig4. Login screen seen after launching main program - SPYOO : This is the database created by the application on the victim's phone. It contains tables : Account, Call, GPS, SMS, Setting, URL etc. The database structure is described in the figure below
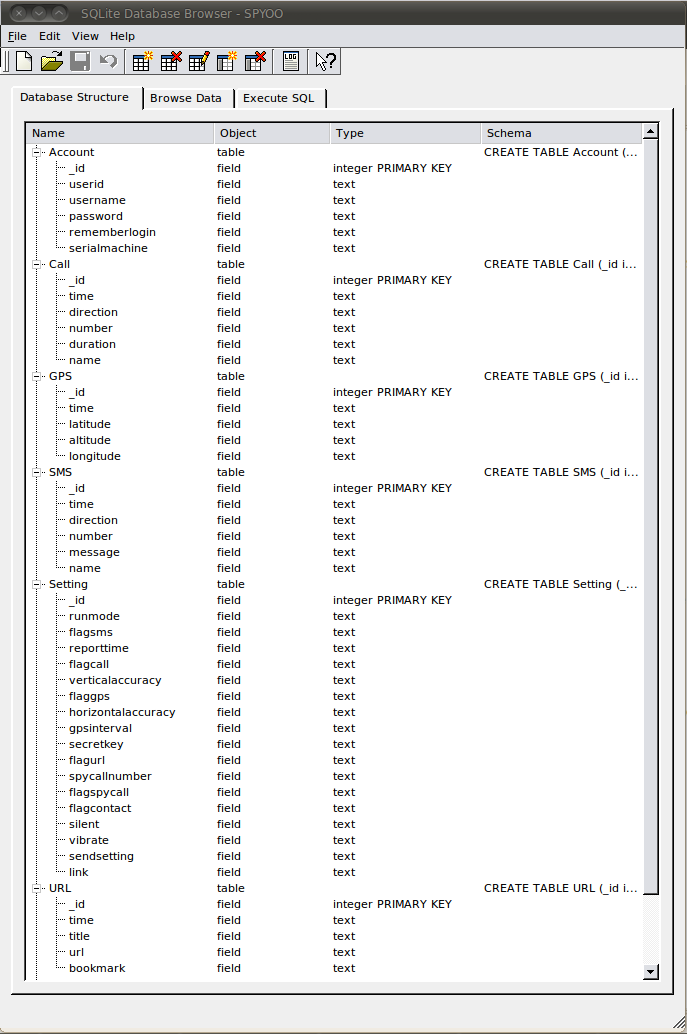
Fig5. SPYOO Database Structure - iits.service.SpyooService : This is the main service responsible for launching listeners that collect information from the victim's phone and sending it to specific locations. When launched, it checks whether a username and password has been used to register the application. If yes, the following data, along with the phone's IMEI, is sent to the corresponding URLs:
- GPS information such as latitudes and logitudes with the corresponding time are sent to the URL LINK/logs/log_gps.aspx
- SMS history from the phone is sent to the URL LINK/logs/log_sms_post.aspx
- Call history from the phone is sent to the URL LINK/logs/log_call.aspx
- Browswer history from the phone is sent to the URL LINK/logs/log_url.aspx
- It then updates the Setting table with settings obtained from the URL LINK/logs/getsetting.aspx where the value of LINK is retrieved from the 'Setting' table.
- iits.spyoo.AutoRun : This activity is responsible for stopping and then starting the SpyooService
- iits.receiver.AutoRunReceiver: This receiver is launched everytime the phone is rebooted and starts the AutoRun activity
- iits.receiver.DateTimeReceiver: This receiver is launched everytime the date or time settings on the phone are changed and starts the AutoRun activity
- iits.receiver.AutoAnswerReceiver: This receiver is launched everytime there's a change in the call state on the phone. When launched, it can control the phone's volume and vibrator settings and if the number matches the value of 'spycallnumber' in the 'Setting' table, displays a blank screen and calls the service AutoAnswerIntentService described below
- iits.service.AutoAnswerIntentService: This service silences the phone's ringer and answers the incoming call, hence hiding all evidence of the incoming call from the victim.
 Recommended Action
Recommended Action
- FortiGate Systems
- Check the main screen using the web interface for your FortiGate unit to ensure that the latest AV/NIDS database has been downloaded and installed on your system - if required, enable the "Allow Push Update" option.
FortiClient Systems
- Quarantine/delete files that are detected and replace infected files with clean backup copies.
 Telemetry
Telemetry
Detection Availability
| FortiGate | |
|---|---|
| Extended | |
| FortiClient | |
| Extreme | |
| FortiAPS | |
| FortiAPU | |
| FortiMail | |
| Extreme | |
| FortiSandbox | |
| Extreme | |
| FortiWeb | |
| Extreme | |
| Web Application Firewall | |
| Extreme | |
| FortiIsolator | |
| Extreme | |
| FortiDeceptor | |
| Extreme | |
| FortiEDR |