Android/NotCompatible.A!tr.bdr
 Analysis
Analysis
Android/NotCompatible.A!tr.bdr is a trojan targetting
Android mobile phones.
It disguises as a legitimate security update when victims
visit compromised websites, triggering a drive-by download.
It communicates with a remote C&C server which will send commands
allowing a remote attacker to use the device as a proxy server to
gain access to private networks.
Technical Details
Android/NotCompatible.A!tr.bdr is downloaded on the victim's mobile phone when he/she visits a compromised website containing a malicious iframe redirecting the Android phone to either:
- http://gao[REMOVED].info/[REMOVED]
- http://android[REMOVED].info/fix1.php
After download, a notification will be displayed, trying to lure the victim into thinking they need to install a security update.
However, the installation will only complete if the victim has:
Settings -> Applications -> Unknown sources set to enabled.
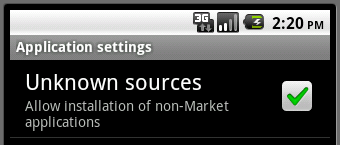
Figure 1: Unknown sources option checked.
The trojan asks for the following permissions:
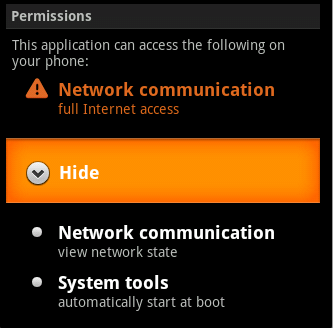
Figure 2: Permissions.
This will enable the trojan to be run each time the device is started.
The trojan installs and runs a service called SecurityUpdateService.
The service first tries to decrypt an AES encypted file using the SHA-256 hash of the hard-coded string "ZTY4MGE5YQo". The file is located in the ressources folder of the application: /res/raw/data.
The file contains 2 remote server URLs:
- not[REMOVED]app.eu:8014
- 3na[REMOVED].ru:8014
- connectProxy: Get the IP address and port and tries to open a connection, will redirect traffic to that host
- newServer: Modify the AES encrypted data file with a new C&C URL
- sendError: Send a custom packet when the command is not valid
- sendPong: Send a custom packet to reply to the server's "ping". It is used to test connectivity on the device.
- shutdownChanal: Closes a specific connection with a remote host
 Recommended Action
Recommended Action
- FortiGate Systems
- Check the main screen using the web interface for your FortiGate unit to ensure that the latest AV/NIDS database has been downloaded and installed on your system - if required, enable the "Allow Push Update" option.
FortiClient Systems
- Quarantine/delete files that are detected and replace infected files with clean backup copies.