Android/FakeInst.C!tr
 Analysis
Analysis
Android/FakeInst.C!tr is a piece of malware for phones running Android OS
It appears to be an installer application (see Figure 1) however, sends out SMS messages to premium numbers without constent of the user, hence causing losses.
Figure 1. Android/FakeInst.C!tr is installed on the device
This behaviour is very similar to other variants of Android/FakeInst, except
this variant also makes use of the Android Cloud to Device Messaging (C2DM) services. Once launched, it registers itself to a specific C2DM service that pushes URLs to view on the device.
br>
Technical Details
The malware comes packaged as com.software.application.When launched, the malware starts the Main activity. Among other things, this creates the look and feel of the application, and, in particular, it loads:
- loads an XML resource, texts.xml which contains localized messages for the application.
- loads a raw resource file, act_schemes.cfg, which contains initial settings for the application such as:
- the name of the real legitimate application this installer is meant to install
- the URL where to download the real legitimate application
- a boolean flag which indicates whether SMS should be sent or not
- a SMS text body (line 5)
- gets the network operator code.
Using the network operator code, the malware finds out the MCC (Mobile Country Code) and MNC (Mobile Network Code) - basically for which country and operator the victim has a mobile phone subscription - and selects a default list of short codes phone numbers.
In the end, the malware sends SMS messages either to the number specified in PREF1 of its preference file (a file named PREFS), or if that field does not exist, it sends an SMS to a random number picked up in the default list of short codes used for the victim's MCC/MNC.
The malware also stores several parameters in its preferences file:
- PREF1: SMS short code
- SMS_DATA_KEY: SMS body
- SENDED_SMS_COUNTER_KEY: a counter for the number of SMS that were sent
- NET_OP: first 5 digits of the IMSI
- WAS_INSTALLED: a boolean indicating whether the final application was installed or not
- INSTALLED_URL: the URL to download the final application from
- PAYED_KEY: a boolean (NO or YES) indicating if the victim paid for the final app or not
- deviceRegistrationID
Additionally, the malware also registers to a C2DM server. C2DM is a service that helps developers send data from servers to their applications on Android device.
The malware registers to a service set up by the malware author behind the opaque email noviigfastn@gmail.com, and also to an HTTP server http://androids-market.ru.
Then, whenever he wishes to, the malware author pushes information to the Android Cloud C2DM servers, and those messages get pushed to devices who registered.
In this particular case, the malware seems to be pushing URLs to the device. The URLs are then automatically displayed on the device, along with some notification text. On an implementation point of view, the malware declares 4 receivers
- Notificator : It is launched when the phone is booted and is responsible for the notifications shown to the user after installation of the application
- Checker : It is used to make checks on the SMS message to be sent and if certain conditions are fulfilled, the SMS message is sent
- SmsReceiver : It listens for SMS messages received on port 8901 of the phone. Its function is to verify whether an SMS message received on the phone is from a premium number or not. It also maintains a counter for the number of SMS messages sent from the phone.
- com.google.android.c2dm.C2DMBroadcastReceiver : It requires the permission com.google.android.c2dm.permission.SEND and is launched when either a message or the registration intent is received from an Android C2DM server.
Permissions requested by the malware are :
- WRITE_EXTERNAL_STORAGE - granted only when the requesting application is signed with the same certificate as the application. If certificates match, permission is granted without user's explicit approval
- INTERNET
- READ_PHONE_STATE
- READ_SMS
- SEND_SMS
- RECEIVE_SMS
- WAKE_LOCK
- com.software.application.permission.C2D_MESSAGE: prevents other applications from registering and receiving the application's messages.
- com.google.android.c2dm.permission.RECEIVE states that the application has permission to register and receive messages from the Android C2DM server
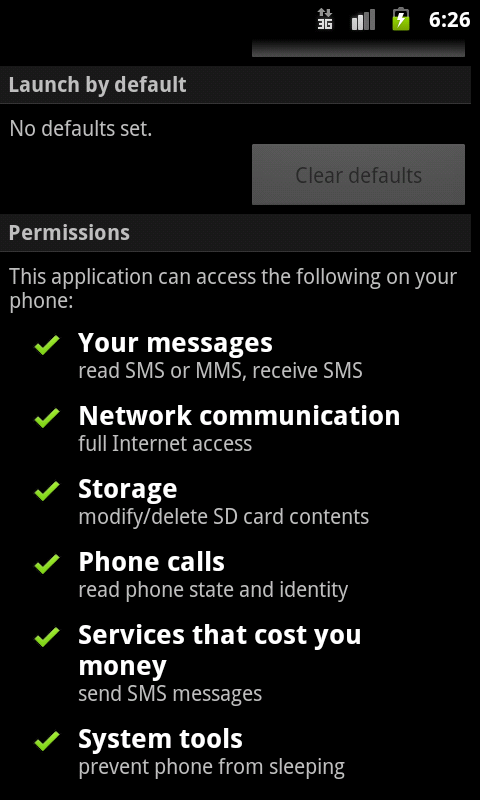
Figure 2. Permissions requested by the malware
 Recommended Action
Recommended Action
- FortiGate Systems
- Check the main screen using the web interface for your FortiGate unit to ensure that the latest AV/NIDS database has been downloaded and installed on your system - if required, enable the "Allow Push Update" option.
FortiClient Systems
- Quarantine/delete files that are detected and replace infected files with clean backup copies.
 Telemetry
Telemetry
Detection Availability
| FortiGate | |
|---|---|
| Extended | |
| FortiClient | |
| FortiMail | |
| FortiSandbox | |
| FortiWeb | |
| Web Application Firewall | |
| FortiIsolator | |
| FortiDeceptor | |
| FortiEDR |