Android/Zitmo.A!tr
 Analysis
Analysis
Android/Zitmo.A!tr is a trojan targetting Android devices.
It spies incoming SMS messages and forwards them to a swedish cell phone
number.
The idea is to steal credentials that might be sent via SMS.
A "Zertifikat" icon shows in the launcher:

Technical Details
Once installed, the application creates a SharedPreferences file called "SecurityService" to store values it will be using such as:
- adminNumber: C&C, default is +46769xxxx (swedish number belonging to Tele2 operator)
- serviceStatus: boolean, if set to true, forward all incoming SMS to C&C.
- isFirstLaunch: boolean set to true if this is the 1st time the application is launched.
It then displays the following message in German:
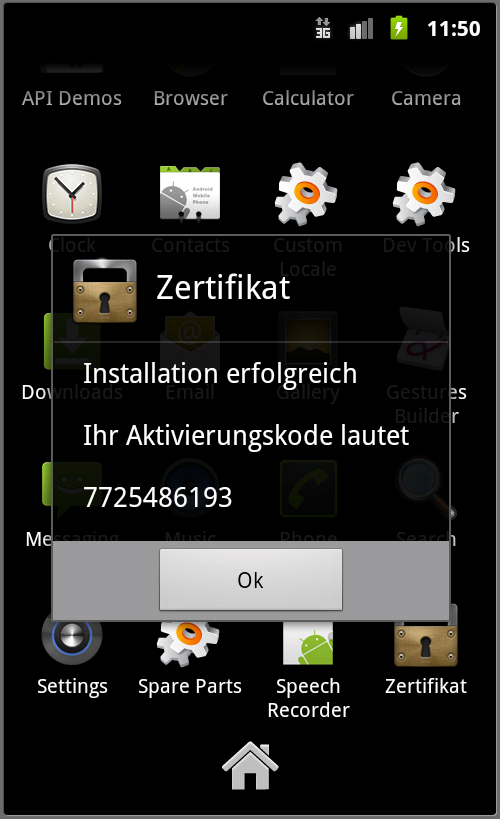
The trojan runs in the background although the application may look like it has stopped.
The trojan installs a receiver which then intercepts SMS messages to check whether they are commands received from the C&C:
- If SMS body is "on" and if it originates from adminNumber:
enable the malicious service and delete the SMS message so that the victim does not suspect anything, and send the SMS "ONOK" back to the C&C. - If SMS body is "off" and originates from adminNumber:
disable the malicious service and delete the SMS message so that the victim does not suspect anything, and send the SMS "OFOK" back to the C&C. - If SMS body contains "set admin [number]":
Change the adminNumber with this new number, and send the SMS "SAOK" back to the C&C. - If the malicious service is enabled, and it is not a command from the C&C,
forward the incoming SMS to the C&C in this format:
message: SMS_BODY. F:ORIGINATING_NUMBER
and delete the message so that the victim does not see it.
 Recommended Action
Recommended Action
- FortiGate Systems
- Check the main screen using the web interface for your FortiGate unit to ensure that the latest AV/NIDS database has been downloaded and installed on your system - if required, enable the "Allow Push Update" option.
FortiClient Systems
- Quarantine/delete files that are detected and replace infected files with clean backup copies.
 Telemetry
Telemetry
Detection Availability
| FortiClient | |
|---|---|
| Extreme | |
| FortiMail | |
| Extreme | |
| FortiSandbox | |
| Extreme | |
| FortiWeb | |
| Extreme | |
| Web Application Firewall | |
| Extreme | |
| FortiIsolator | |
| Extreme | |
| FortiDeceptor | |
| Extreme | |
| FortiEDR |