Android/DroidKungFu.F!tr
 Analysis
Analysis
Android/DroidKungFu.F!tr is a variant of
Android/DroidKungFu.A!tr.
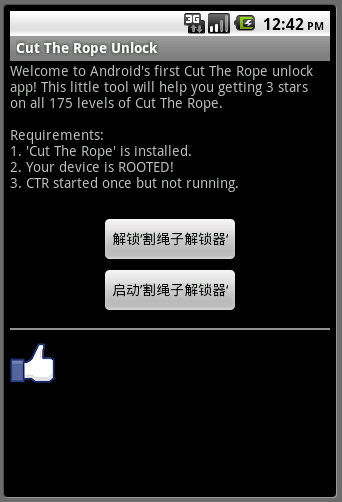
The samples we have analyzed pose as a Level Unlocker for the famous game Cut The Rope. The samples do indeed try to unlock the levels (a functionality which is not malicious, perhaps just a spoiler), but in addition, they also communicate with remote servers . In a word, Android/DroidKungFu.F!tr trojanizes the level unlocker application.
The catch in Android/DroidKungFu.F!tr is that it trojans applications which require root privileges to work. For instance, the real Cut the Rope Level Unlocker requires root privileges. The trojaned version uses the root privilege to drop and run native code on the device.
![]()
Figure 1. The icon of Android/DroidKungFu.F!tr mentions the game Cut the Rope.
Technical Details
The difference with variant A are mainly technical:
- Package name and hierarchy
- Command and Control Server URLs
- C&C commands and URLs are implemented natively (like the Android/DroidKungFu.E!tr variant)
- Native code contains obfuscated strings. It does not use AES encryption as in other variants, but applies a bitwise NOT to all bytes.
- Does not embed any exploits to root the phone. Instead, it assumes the phone is rooted.
First of, besides its malicious tasks, the malware actually unlocks levels for Cut the Rope. This consists in dumping a specific configuration file in the shared preferences directory of Cut the Rope. This feature is not malicious.
The unlocking configuration is found in the package, in assets/CtrApp.xml, and it must be copied to /data/data/com.zeptolab.ctr/shared_prefs/.
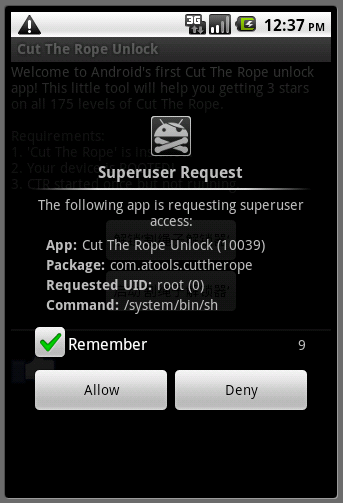
To do so, i.e write in another directory tree, the unlocking application must have root privileges. Figure 3 shows the application requesting root privileges.
|
|
| Figure 2. Android/DroidKungFu.F!tr poses as an unlocker for Cut the Rope. | Figure 3. The unlocker application requests root permissions to unlock all levels of the game. |
Checking that the device is rooted is done by checking whether the Superuser.apk application is installed or not (Figure 3 shows the Superuser application). If the application is not installed, the device is assumed not to be rooted and the malware simply exits.
Meanwhile, the trojan launches a background service called UpdateCheck. This service executes embedded native code located in a library called libavd3.so.
This library contains obfuscated strings - encrypted using a bitwise NOT. The strings are first decrypted and then, the library extracts an executable file hidden withing the library. This executable handles the malicious parts of the malware.
The dropped executable also contains obfuscated strings, also using a bitwise NOT. Its first task is to decrypt all those strings.
The dropped file will try to copy itself as:
- /system/bin/debuggerd
- /system/bin/vold
- /system/bin/rm
- /system/bin/move
- /system/bin/mount
- /system/bin/ifconfig
- /system/bin/chown
- /system/bin/dhcpd
- /system/bin/installd
- /system/lib/libd1.so
There are 3 C&C servers URLs:
- http://[CENSORED]new.com:8511/search/
- http://[CENSORED]go8.com:8511/search/
- http://[CENSORED]968.com:8511/search/
- GETID: The server sends back a unique identifier for the trojan
- GETTASK: The server sends back a task for the trojan
- URLREPORT: The trojan sends a report of activities to the C&C
- StartDown
- DownNet
- DownSys
- DownOk
- OKNOLOCK
- INSTOK
- RUNOK
- DELOK
- URLOK
 Recommended Action
Recommended Action
- FortiGate Systems
- Check the main screen using the web interface for your FortiGate unit to ensure that the latest AV/NIDS database has been downloaded and installed on your system - if required, enable the "Allow Push Update" option.
FortiClient Systems
- Quarantine/delete files that are detected and replace infected files with clean backup copies.
 Telemetry
Telemetry
Detection Availability
| FortiClient | |
|---|---|
| Extreme | |
| FortiMail | |
| Extreme | |
| FortiSandbox | |
| Extreme | |
| FortiWeb | |
| Extreme | |
| Web Application Firewall | |
| Extreme | |
| FortiIsolator | |
| Extreme | |
| FortiDeceptor | |
| Extreme | |
| FortiEDR |