Android/Fake10086.A!tr
 Analysis
Analysis
Android/Fake10086.A!tr affects mobile phones running Android 1.6 and greater.
It ships with an operational application to find nearby hotel rooms (see screenshots 1 and 2), but once installed blocks all incoming SMS from 10086 and silently connects to remote websites to which it posts information related to the victim's phone (IMEI and phone number for instance).

|
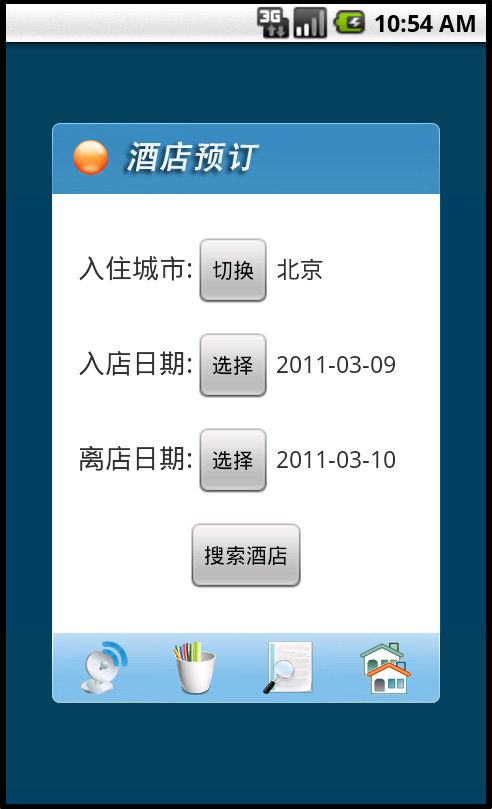
|
| Figure 1. Book Economy Hotels (splash screen) | Figure 2. Select a hotel for a given city and dates |
Technical Details
Android/Fake10086.A!tr requires numerous permissions to run:
- android.permission.INTERNET
- android.permission.ACCESS_FINE_LOCATION
- android.permission.ACCESS_COARSE_LOCATION
- android.permission.ACCESS_NETWORK_STATE
- android.permission.WRITE_EXTERNAL_STORAGE
- android.permission.RECEIVE_BOOT_COMPLETED
- android.permission.RECEIVE_SMS
- android.permission.SEND_SMS
- android.permission.ACCESS_NETWORK_STATE
- android.permission.CHANGE_NETWORK_STATE
- android.permission.READ_PHONE_STATE
- android.permission.WAKE_LOCK
- android.permission.WRITE_EXTERNAL_STORAGE
But other permissions (e.g RECEIVE_SMS, SEND_SMS, READ_PHONE_STATE) are suspicious. Indeed, the READ_PHONE_STATE is used by the trojan to retrieve the IMEI of the victim and post the information to a remote web site:
hxxp://www.youlubg.com:81/Coop/request3.php
Precisely, the malware collects various information regarding the victim's phone and stores that information (savePhoneInfo function in SettingManager class) in a hidden file in /data/data/com.hotel/files/.hide/upload.xml. This XML file is then posted (HTTP POST) to the remote website:
<?xml version="1.0" encoding="UTF-8" standalone="yes" ?> <body> <imei>VICTIM S IMEI</imei> <version>1.0.1</version> <smscenter>8613800100500</smscenter> <first>1</first> <handled>0</handled> <pid>20013</pid> <installtime>8 Mar 2011 13:13:38 GMT</installtime> <sysversion>7</sysversion> <auth>michael</auth> <fare>0</fare> <phonenum>VICTIM PHONE NUMBER</phonenum> <reason>simLoaded</reason> </body>The remote server replies with configuration data, stored in the same hidden directory, named serverInfo.xml:
<?xml version="1.0" encoding="UTF-8"?> <body> <auto_run>1</auto_run> <auto_link_time>24</auto_link_time> <version>1.0.1</version> <channel> <channel_name>vedio</channel_name> <vedio_url>hxxp://211.136.165.53/wl/rmw1s/pp66.jsp</vedio_url> <channel_sms>2</channel_sms> <intercept_key> <key>MOBILE</key> <key>FEES</key> <key>1 yuan</key> <key>2 yuan</key> </intercept_key> <intercept_time>2000</intercept_time> <limit_nums_day>4</limit_nums_day> <limit_nums_month>4</limit_nums_month> </channel>
The hidden directory also stores other hidden files:
- vedio.xml
- vedio_file.3gp: a video
- log.txt: debug log
The trojan stores its settings in /data/data/com.hotel/shared_prefs/setting.xml:
<?xml version='1.0' encoding='utf-8' standalone='yes' ?> <map> <boolean name="internet_connect_failed" value="true" /> <string name="pid">20013</string> <string name="sms_temp_block_num_and_times">10086;1</string>In particular, note the sms_temp_block_num_and_times tag (which corresponds to the get and setSMSTempBlockNumAndTimes method of the SettingManager class).
The first number corresponds to a pattern of phone numbers to block: in that case, all SMS messages coming from phone numbers ending with 10086 will be blocked.
The second number corresponds to the number of SMS to block.
So, in theory, only one SMS from 10086 should be blocked, but actually, each time an SMS is received (handled by the PrivilegedSmsReceiver class), the trojan re-configures the malware to block SMS from 10086 one more time. Consequently, SMS coming from numbers ending by 10086 will never be displayed.
The malware also supports other malicious functionalities which haven't been fully analyzed yet, such as deleting the last entry in the call log, blocking keys or ports.
 Recommended Action
Recommended Action
- FortiGate Systems
- Check the main screen using the web interface for your FortiGate unit to ensure that the latest AV/NIDS database has been downloaded and installed on your system - if required, enable the "Allow Push Update" option.
FortiClient Systems
- Quarantine/delete files that are detected and replace infected files with clean backup copies.
 Telemetry
Telemetry
Detection Availability
| FortiGate | |
|---|---|
| Extreme | |
| FortiClient | |
| Extended | |
| FortiMail | |
| Extended | |
| FortiSandbox | |
| Extended | |
| FortiWeb | |
| Extended | |
| Web Application Firewall | |
| Extended | |
| FortiIsolator | |
| Extended | |
| FortiDeceptor | |
| Extended | |
| FortiEDR |